Your Password Isn't Enough: Why Your Digital Life Needs Multifactor Authentication Today
Oct 21

Experience OutThink
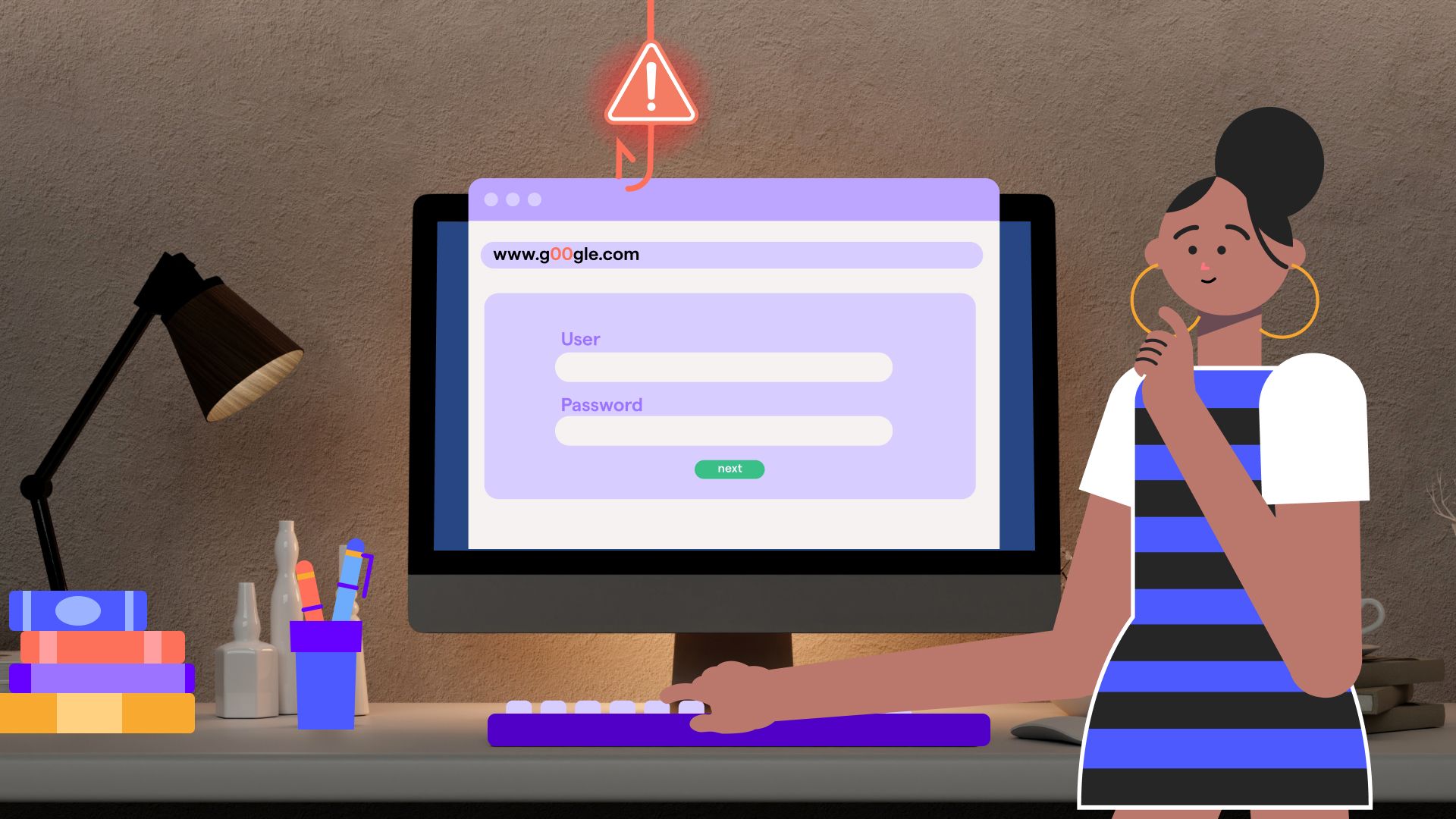
Imagine this: You're checking your email over morning coffee when you notice something strange - someone from halfway across the world just logged into your bank account. Your heart races as you realize your password has been compromised.
This scenario plays out thousands of times daily, but there's a simple shield that could have prevented it: Multifactor Authentication (MFA). As highlighted by CISA and the National Cybersecurity Alliance for Cybersecurity Awareness Month 2024, activating MFA isn't just another security recommendation, it's your digital life's safety net in an increasingly dangerous online world.
Why MFA Is Your Digital Bodyguard
Think of your password as a single lock on your front door. Now imagine that cyber criminals have master keys that can potentially open that lock. Scary, right?
That's essentially what happens in today's threat landscape where sophisticated hackers can crack, steal, or guess passwords with alarming efficiency.
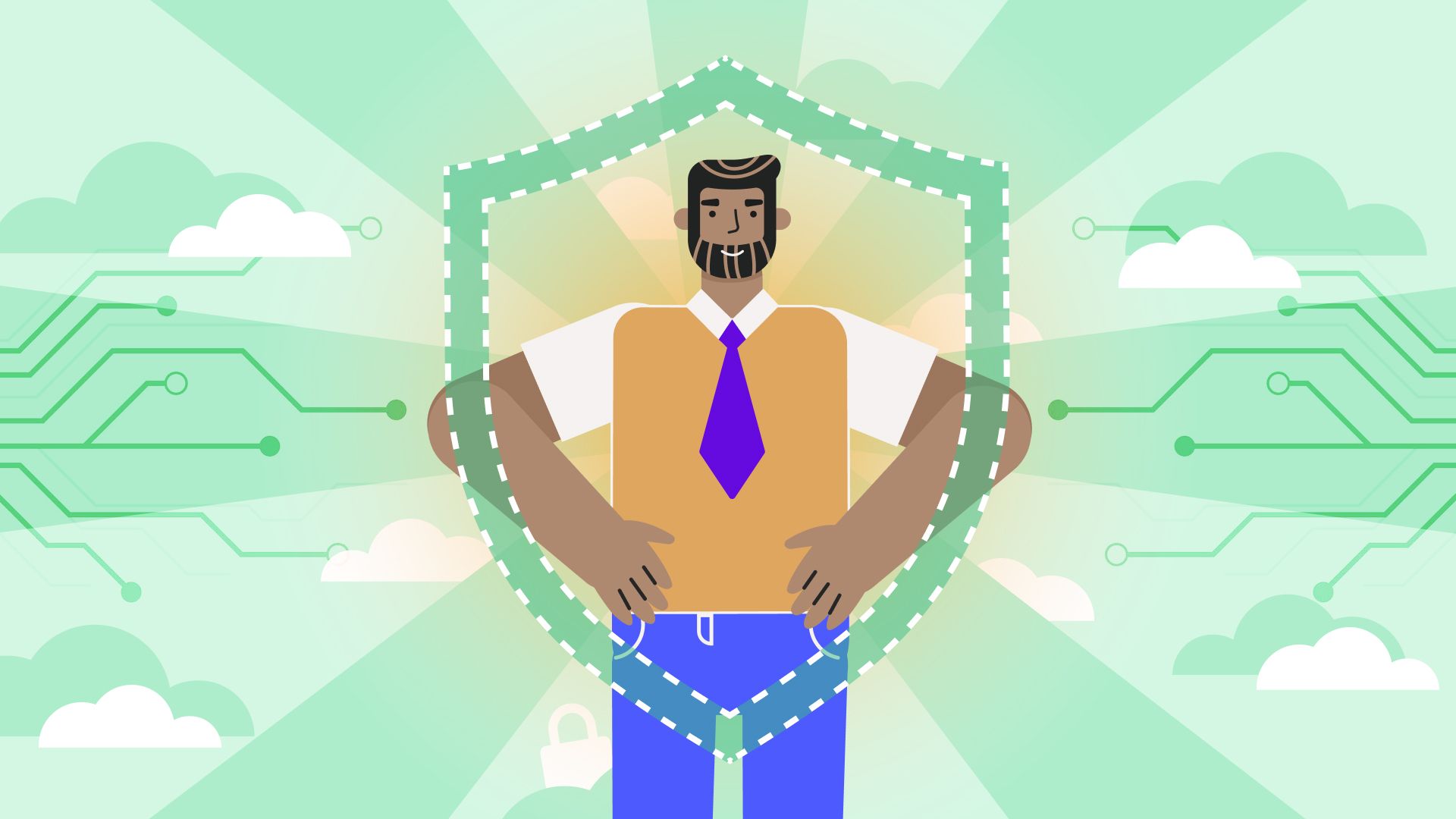
MFA adds multiple locks to your digital door. Even if someone gets your password (the first "key"), they still can't get in without the second verification method - typically something you physically possess like your phone for a text code or authentication app.
CISA's research puts this in perspective: Your account is over 99% less likely to be compromised when protected by MFA. That's the difference between almost-certain vulnerability and near-complete protection with just one security setting.
The Human Factor in MFA Adoption
"I'll do it later." "It seems complicated." "It'll slow me down." Sound familiar? These are the thoughts running through many people's minds when they see that MFA setup prompt and keep clicking "remind me later."
This human hesitation is precisely why OutThink takes a human-centric approach to cybersecurity. Research confirms that about 95% of security incidents stem not from sophisticated technical attacks but from human decisions and behaviors.
The challenge isn't getting the technology right, it's helping people understand why that extra 15 seconds during login matters so much. Encouraging employees to adopt MFA isn’t just about technology; it's about changing behavior and fostering a culture of security awareness.
OutThink and MFA
OutThink’s platform integrates tools like machine learning and human risk intelligence to tailor training and reduce risky behaviors. This approach ensures that employees not only understand how to use security tools like MFA but also whyit's essential. By leveraging applied psychology, OutThink helps organizations foster a mindset where users are more likely to turn on MFA proactively, understanding it as a vital part of their role in safeguarding data.
Unlike traditional security training that treats employees as potential threats, OutThink's platform recognizes them as potential allies. Their solution combines machine learning with human risk intelligence to understand why employees resist security measures like MFA.
OutThink's cybersecurity human risk management platform aligns with the broader goals of Cybersecurity Awareness Month by making employees a part of the solution, rather than treating them as a security vulnerability. For example, through their SaaS platform, OutThink delivers intelligent training designed to improve employees' security habits - turning MFA into an organizational standard, not an afterthought.
By helping employees understand not just the how but the why behind MFA, OutThink transforms security from an IT mandate into a shared responsibility that everyone embraces.
MFA Myths
Myth: "MFA is too complicated for everyday users."
Fact: Modern MFA often requires just a single tap on your phone, which is easier than typing a complex password.
Myth: "I don't have anything worth stealing."
Fact: Cybercriminals can use your compromised accounts to attack others or steal your identity even if you don't have financial information stored.
Myth: "MFA will slow down my workflow."
Fact: The average MFA verification takes 5-10 seconds compared to the hours or days required to recover from an account breach.
Your 5-Minute MFA Setup Guide
"I'd enable MFA if I knew how." If that thought has crossed your mind, you're not alone - and you're also just minutes away from significantly stronger security. Here's your quick-start guide!
For Your Personal Digital Life:
- Google accounts: Open Security settings → 2-Step Verification → Get Started
- Microsoft/Outlook: Go to Security settings → Additional security → Two-step verification → Turn on
- Social media: Look for "Security" or "Privacy and Security" in settings, then "Two-factor authentication"
For Your Organization:
- Start with high-value accounts (financial platforms, customer data systems)
- Choose user-friendly options like authenticator apps rather than hardware tokens for better adoption
- Create clear instructions with screenshots specific to your systems
Remember, the best time to set up MFA was yesterday. The second-best time is right now - before you close this article. Take five minutes to secure at least your email account before continuing your day.
Need more detailed guidance? CISA offers comprehensive step-by-step instructions online.
Your Security Moment of Truth
Two months from now, you might not remember most of what you read today. But if you take just one action - enabling MFA on your important accounts - you could be saving yourself from becoming the next cybercrime statistic.
The truth is stark: In the time it took you to read this article, hundreds of accounts without MFA were compromised somewhere in the world. Yours doesn't have to be next.
By combining the technical protection of MFA with the human-focused security awareness that OutThink champions, you're not just checking a cybersecurity box - you're building a sustainable defense that works with human nature, not against it.
This Cybersecurity Awareness Month, make the commitment. Enable MFA today, encourage a colleague to do the same tomorrow, and together we'll build a more secure digital world, one account at a time.
Turning on MFA is a simple but powerful step in protecting both individual and organizational data. By combining the technical advantage of MFA with the human-focused security strategies promoted by OutThink, companies can significantly reduce their cybersecurity risk. This Cybersecurity Awareness Month, make sure MFA is at the top of your organization's priority list.