AI-Powered Phishing Simulator
65% of users open emails, links and attachments from unknown sources on a work device. Join the ranks of businesses that have successfully trained their teams to recognize and thwart phishing attacks.
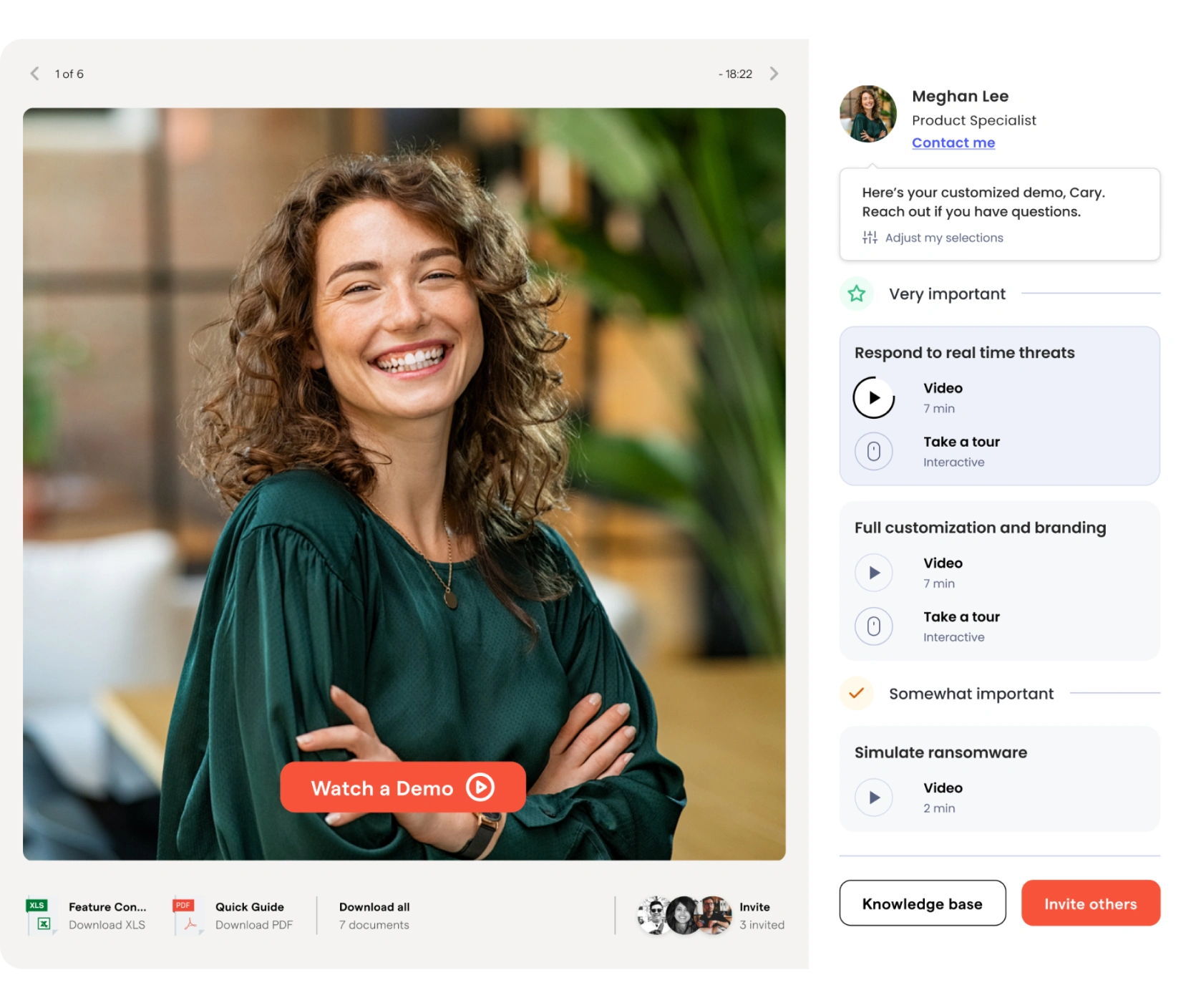
Stay one step ahead of hackers
Experience realistic, adaptive phishing scenarios tailored to your organization’s needs.
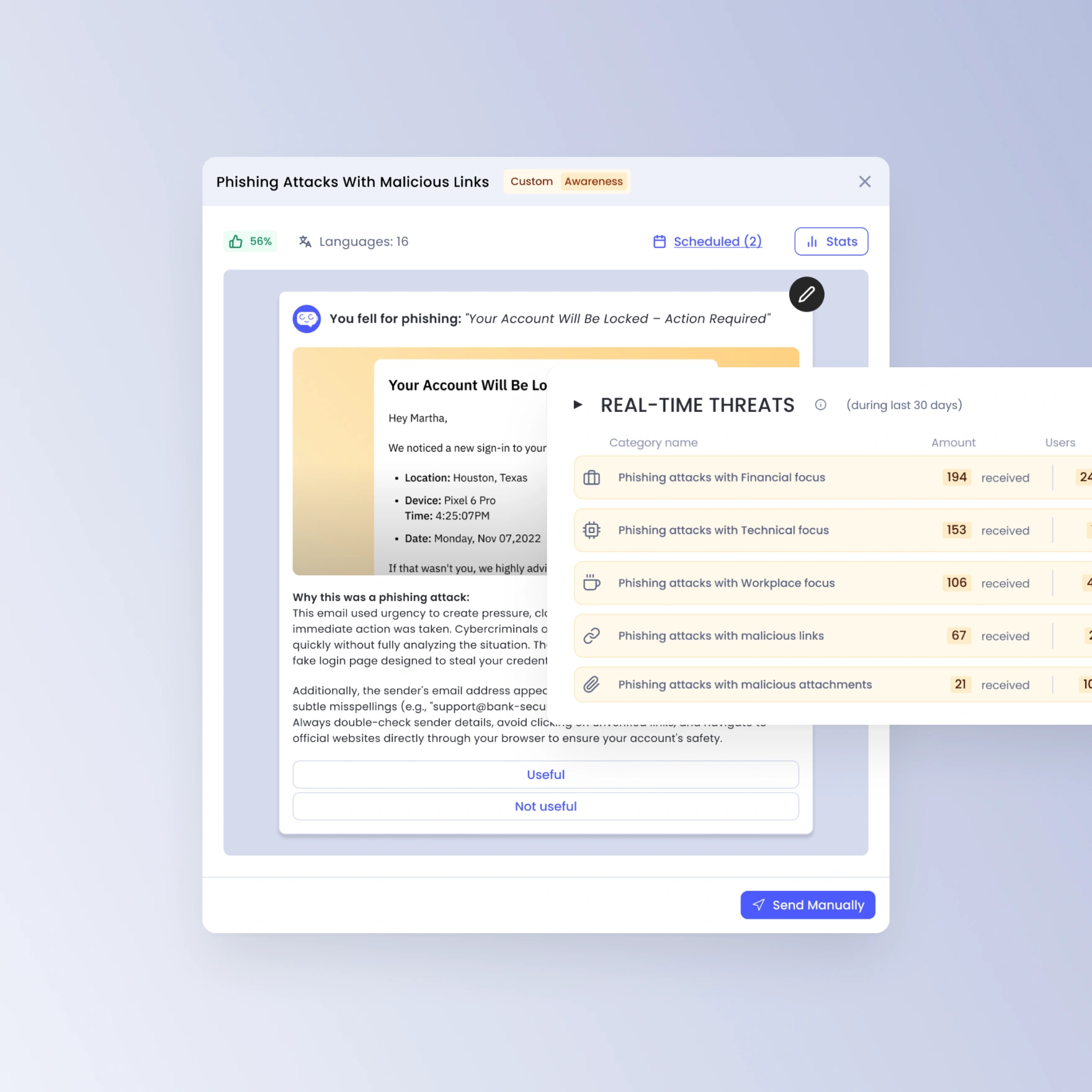
Respond to evolving threat insights in real-time
Leverage the same social engineering tactics real-world hackers use to create authentic learning experiences. Implement updated templates, and keep users prepared for emerging techniques.
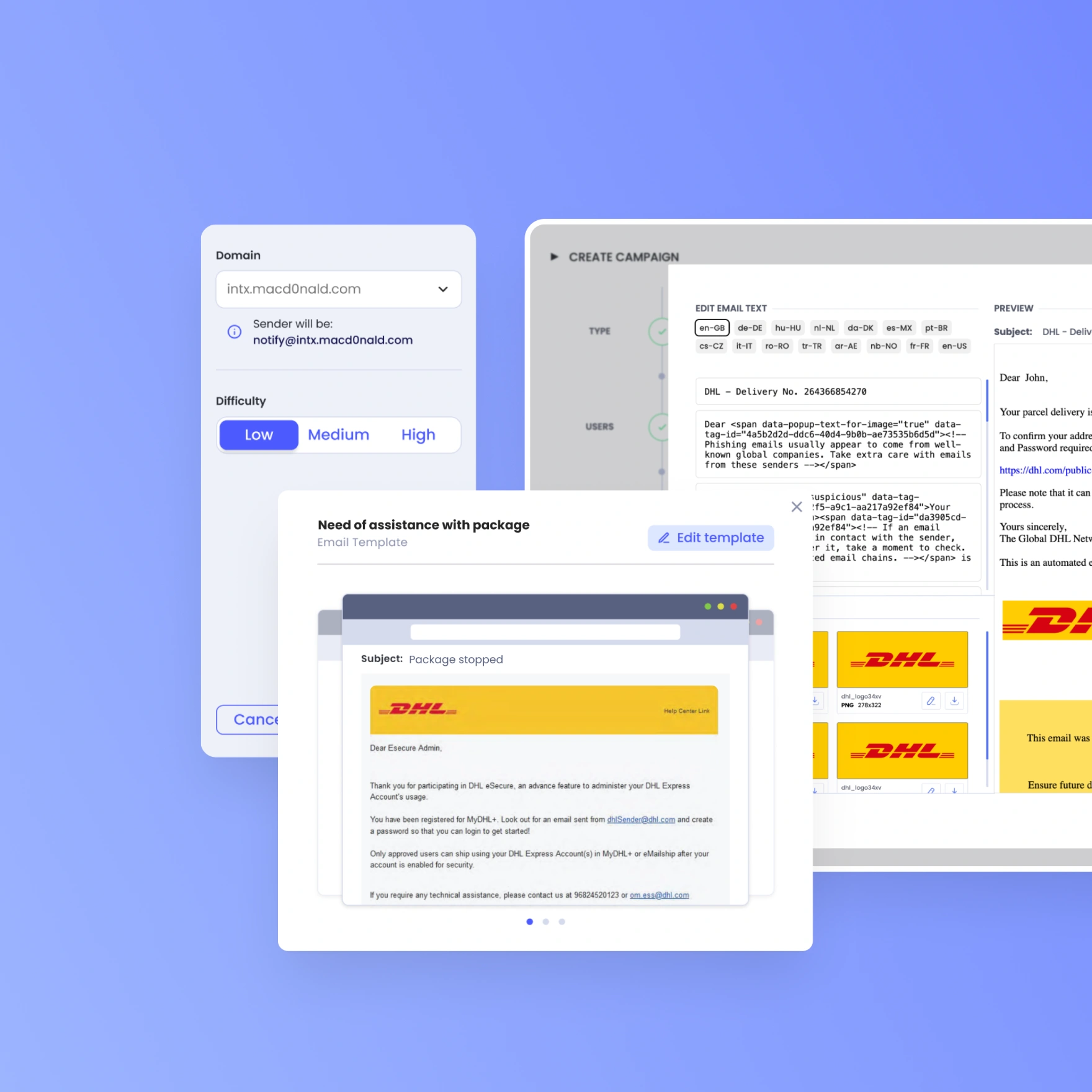
Full customization control
Personalize text, images, difficulty levels and even domains used to send simulated phishing campaigns.
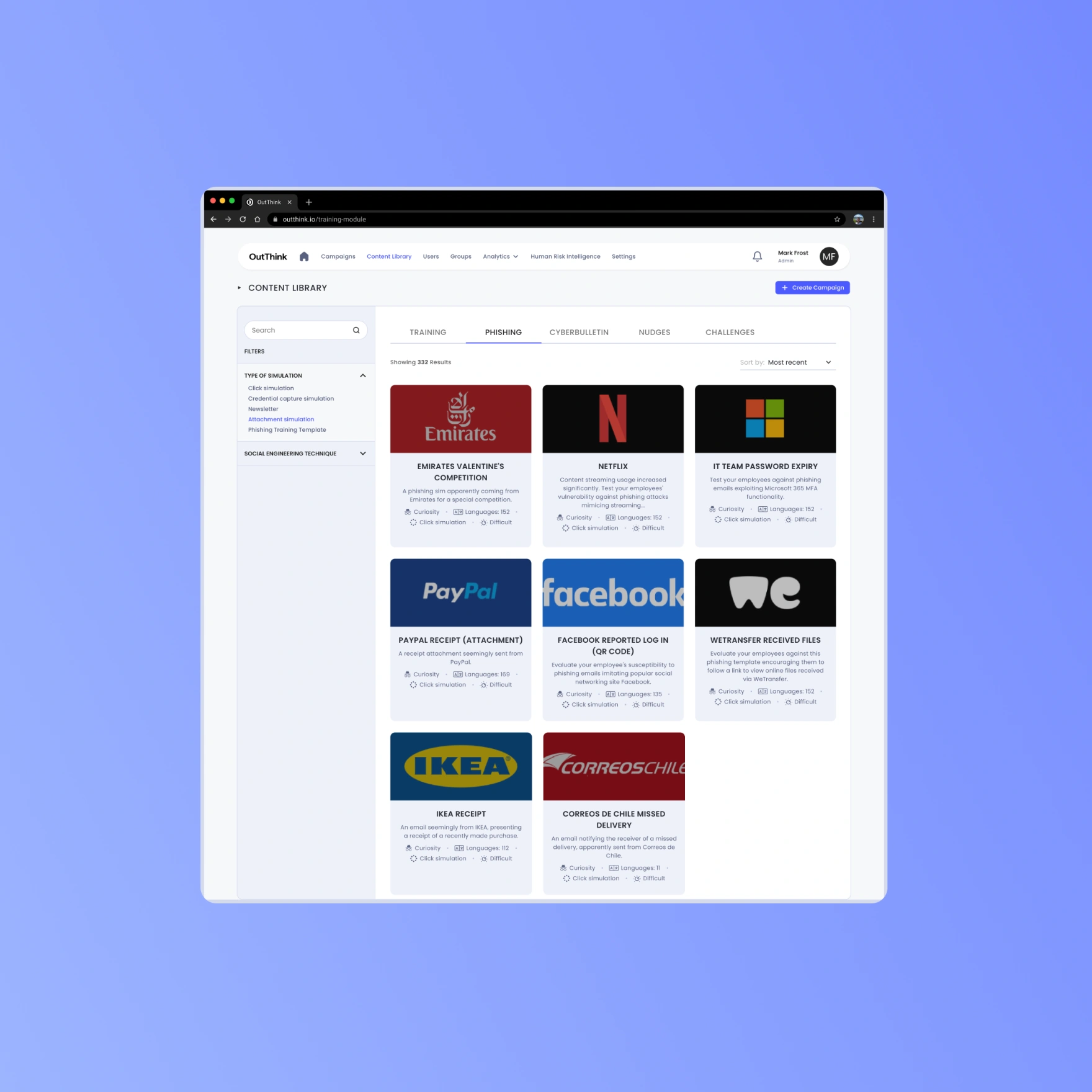
Robust template library
Choose from a vast library of templates including click simulations, credential capture and email attachments.
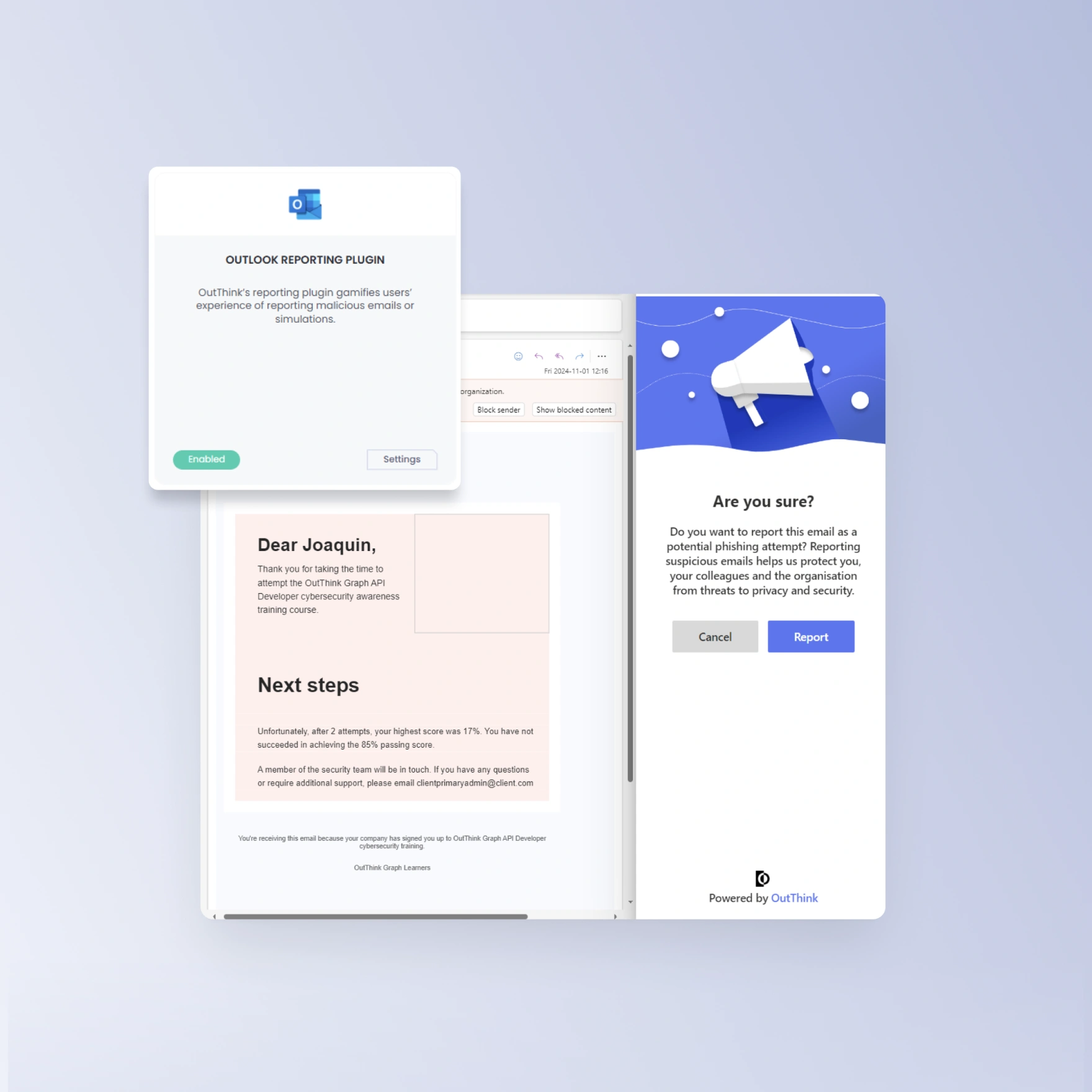
Activate your people as human sensors
Use our Microsoft Outlook and Google Mail reporting plug-ins to ensure your users can report phishing simulations and real suspicious activity to your SOC swiftly.
OutThink is not only very easy to use but also highly effective. To demonstrate its effectiveness, we recently completed our annual information security training and observed a remarkable increase in the number of reported phishing simulations conducted through OutThink— 4X more than before its implementation.

OutThink business email compromise
Deliver hyper-customized phishing simulations directly within your users’ most-used productivity tools.
Simulate ransomware
Deliver hyper-customized phishing simulations directly within your users’ most-used productivity tools.
All your files will be deleted in
08:00:00
Well done! Your negligence allowed us to take control of your computer.
As you read this, your files and those of your company are being encrypted! You can only unlock them with the code we hold.
You have 8 hours to send us proof of transfer of $500 in Bitcoin to the following address:
anonymous-team@gmail.com
Go beyond: Understand human behavior
Gather and act on observed behaviors, whilst protecting user productivity.
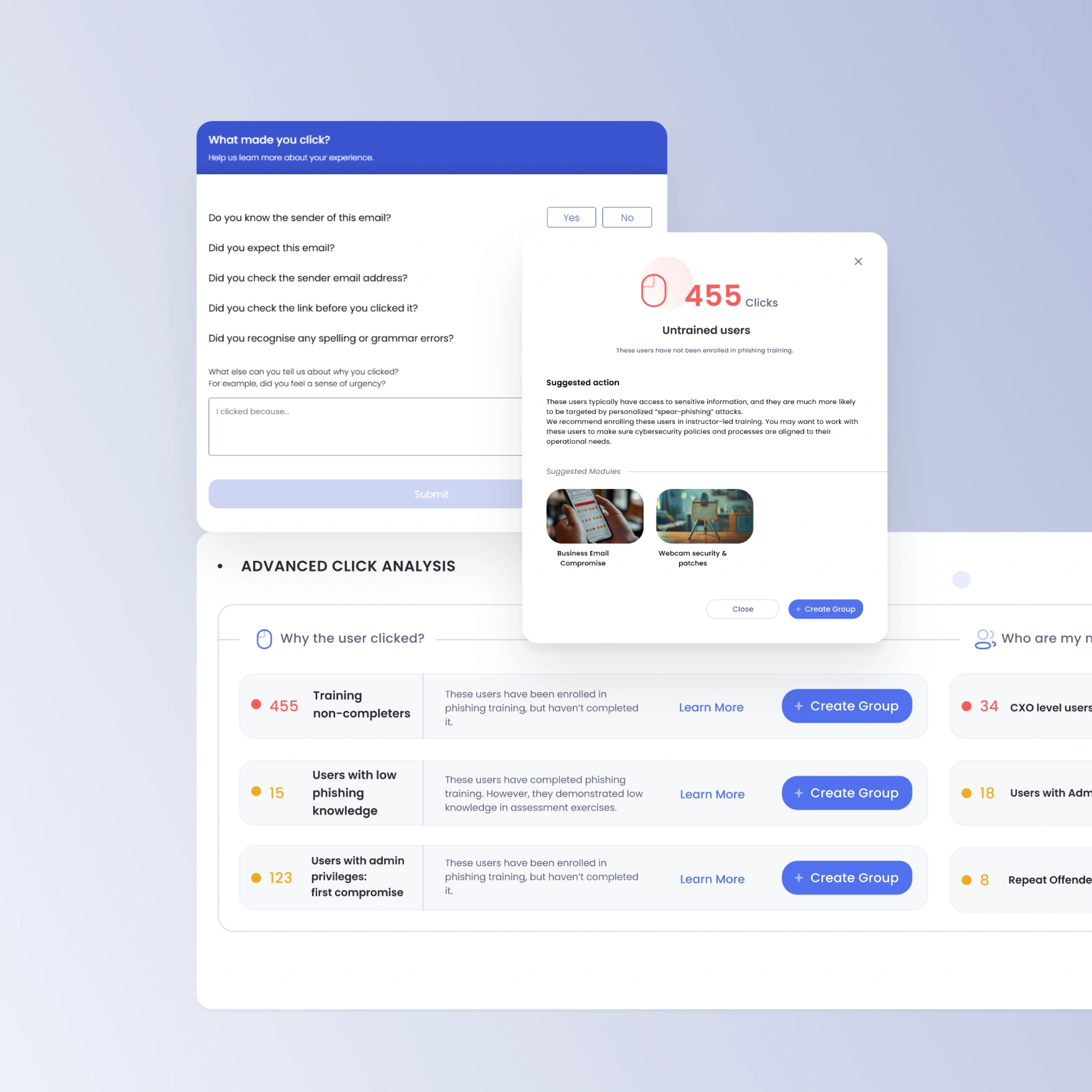
Root cause analysis for compromised users
Leverage OutThink AI to analyze and understand why users are tricked. Address user feedback on security policies, enhancing their effectiveness and resolving potential issues.
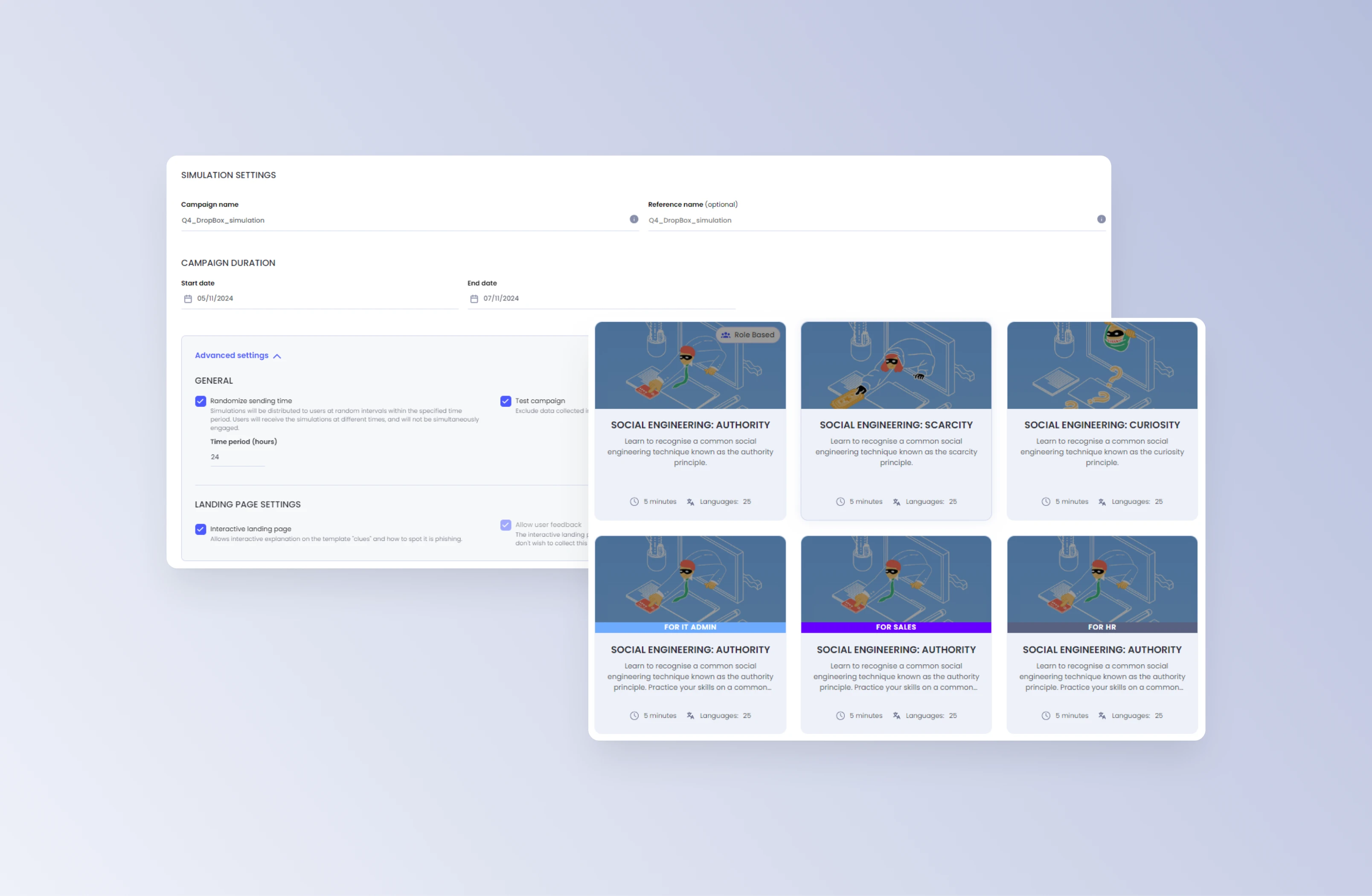
Automated follow-up training for compromised users
Drive engagement and relevance through tailored follow-on training based on specific templates and missed clues.
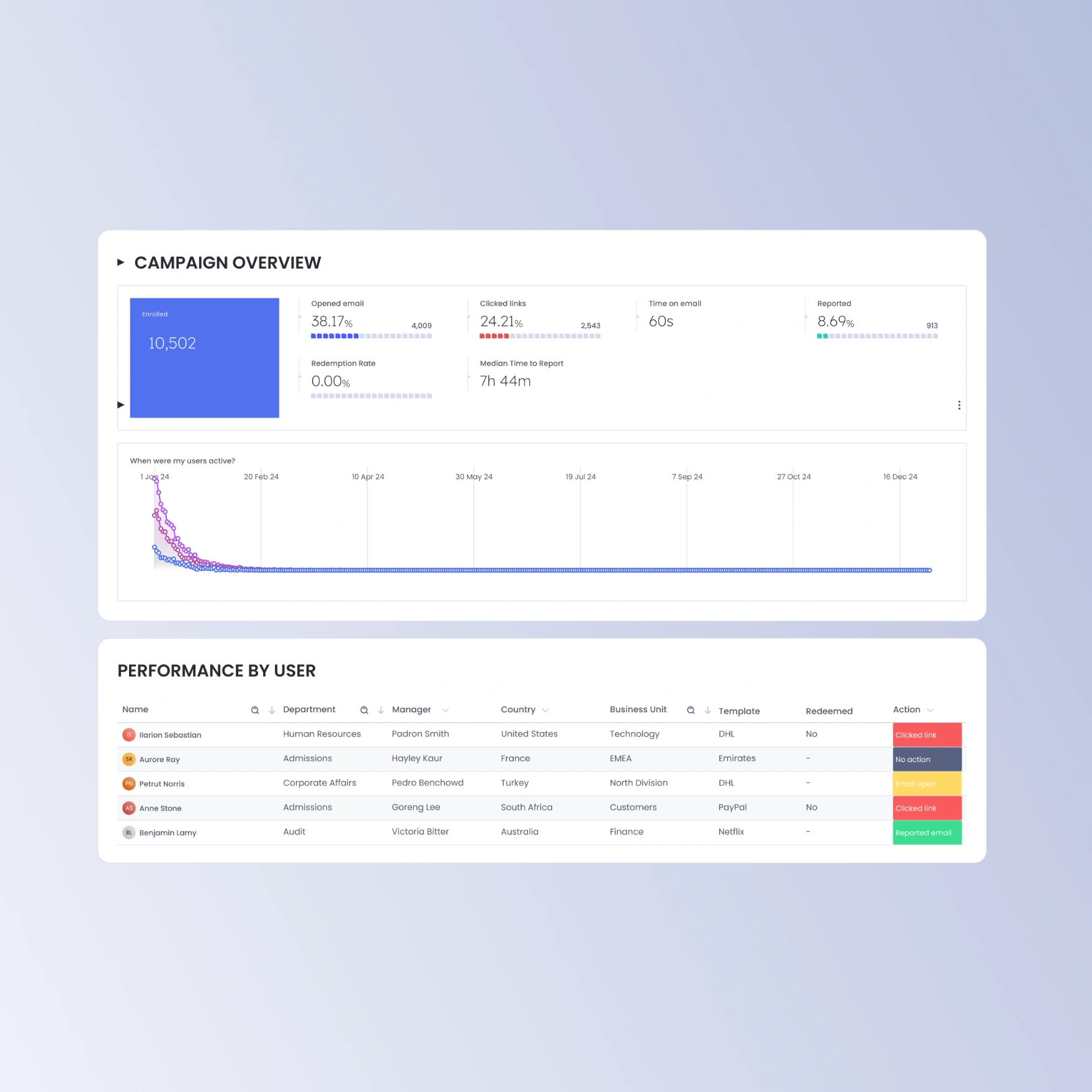
Market leading diagnostic metrics
Go further with access to industry leading campaign metrics covering meantime to report phishing (MTTR) and phishing redemption.
[With OutThink] We've seen two major improvements. First, our efficiency in conducting phishing campaigns has skyrocketed. Second, the feedback from users who fall for phishing simulations is invaluable. OutThink’s generative AI synthesizes this feedback into comprehensive reports within minutes, enabling us to continuously refine our approach and improve the effectiveness of each campaign










