The Strategic Role of Adaptive Security Awareness Training Content
Apr 21

Experience OutThink
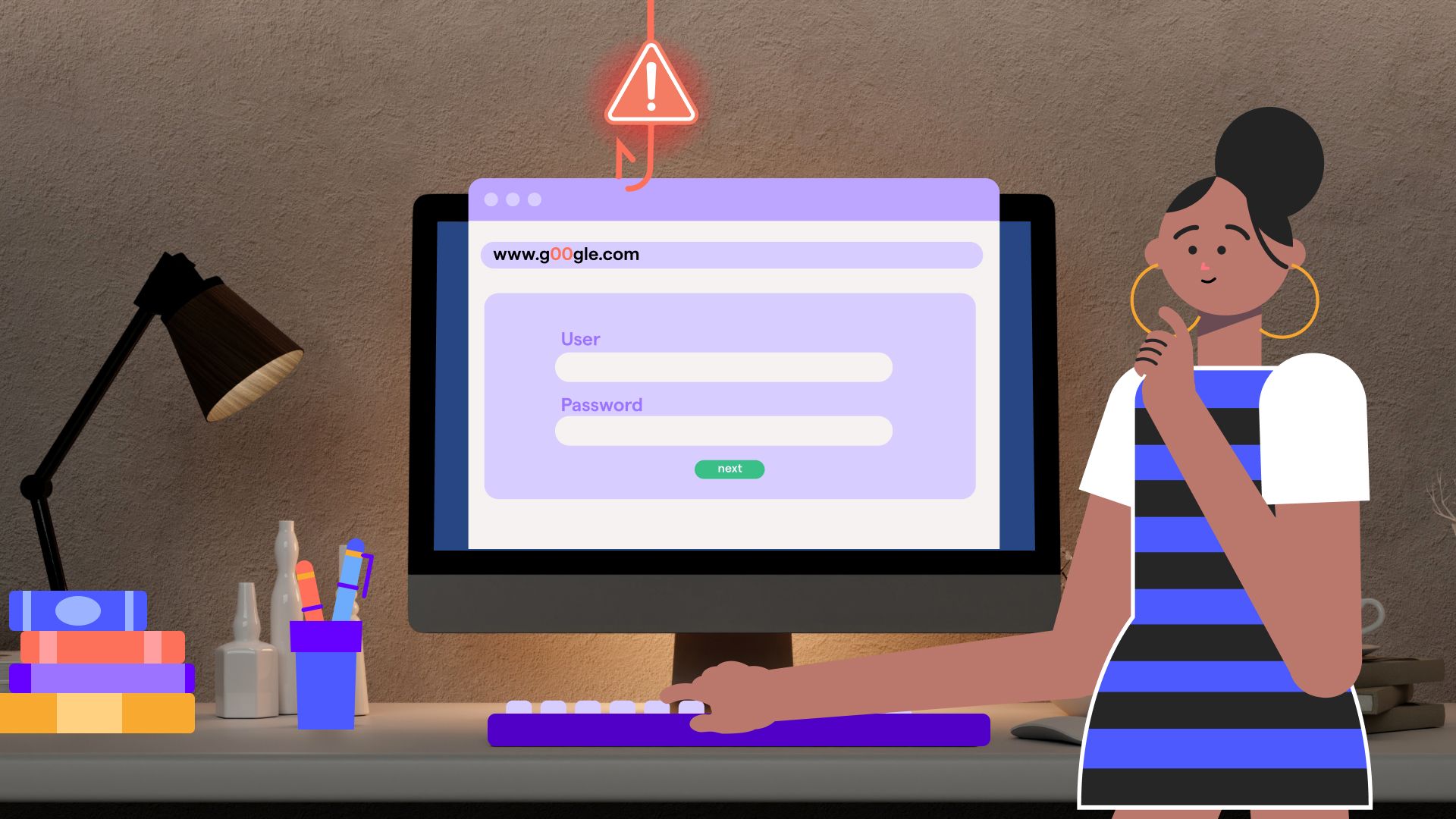
Picture this: Your company just invested thousands in the latest cybersecurity tools. Firewalls? Check. Intrusion detection? Check. Advanced threat protection? Double check. Then one morning, Sarah from accounting clicks a convincing email link, and suddenly your systems are compromised.
Sound familiar? That's because in today's digital world, the strongest technical defenses can be undone by a single human error.
Let's be honest - traditional security training has earned its boring reputation. We've all sat through those generic videos that feel more like a chore than a valuable learning experience.
"Click next to continue." Yawn.
But here's the reality: cybercriminals are getting smarter, more targeted, and more convincing. The phishing email that lands in your marketing team's inbox looks nothing like the one your IT department receives. So why are we still training everyone the same way?
Think about it - would you teach a chef and a doctor the same skills? Of course not! So why do we use one-size-fits-all security training?
When the finance team learns how to spot invoice fraud that resembles their daily workflow, they pay attention. When developers see security scenarios relevant to code repositories they use, it clicks. Relevance creates engagement - it's that simple.
Recent studies show that employees are 75% more likely to remember security protocols when the training reflects their actual job responsibilities. This isn't just about better training; it's about effective protection.
Recognizing this need, OutThink is launching a new Security Awareness Training (SAT) Program Generator. Our platform analyzes behavioral patterns and learning styles to create personalized training journeys. That means Mary in finance gets scenarios about wire transfer fraud, while Dave in IT focuses on spotting unusual network activity.
The result? Security awareness training that sticks because it makes sense for each person's role.
What Is Security Awareness Training Content?
Security awareness training content consists of structured learning materials that educate employees on how to identify, prevent, and respond to cyber threats. This content may cover everything from phishing awareness to password hygiene, safe data handling, and insider threat detection.
But not all training is created equal. Effective programs are interactive, role-specific, and continually updated to reflect evolving risks instead of relying on static, check-the-box compliance.
The Need for Personalized Security Awareness Training
Generic training often misses the mark. According to the Cybersecurity and Infrastructure Security Agency (CISA), tailoring awareness programs to reflect employees' actual responsibilities leads to better retention and risk mitigation.
This need for tailored training is further supported by Gartner, which ranks OutThink 4.9 out of 5, highlighting its excellence in delivering highly personalized, behavior-focused security awareness training.
The most effective security awareness training content shares these key elements:
- It speaks to your job: personalized scenarios that mirror real threats you might encounter
Effective training mirrors the real-world challenges employees face in their specific functions. This includes aligning content with threat scenarios that are most likely to impact each department.
- It's engaging: Interactive challenges that test your knowledge in realistic situations
Training that includes simulations, scenario-based challenges, and quizzes drives better knowledge retention. In fact, interactive methods outperform traditional, passive formats by up to 75% in retention.
It evolves: Regular updates that reflect the latest threats, not outdated risks from three years ago
Cyber risks evolve quickly. That’s why programs must continuously adapt. CISA emphasizes that “awareness is a continuous process,” not a one-off initiative.
The best programs now offer training as an ongoing cycle - complete with role-specific refreshers, microlearning, and phishing simulations - which makes it easier to embed security practices into daily routines.
For organizations evaluating comprehensive AI SAT platforms, understanding the full landscape of available tools and their capabilities is essential for making informed decisions that align with specific security needs and organizational goals.
- It fits into your workday - Quick, focused modules that respect your time and attention span
Nobody has time for hour-long training sessions that derail your entire morning. Modern security awareness training delivers bite-sized lessons you can complete between meetings or during a coffee break. These microlearning moments add up to strong security habits without the productivity impact.
When security training feels relevant to your daily work, it transforms from an annoying interruption into a valuable skill.
OutThink’s Adaptive Security Awareness Training
The OutThink's Adaptive Security Awareness Training platform is designed to meet the needs of modern organizations. Using AI and behavioral analytics, it builds dynamic training paths tailored to the risk profiles and learning styles of individual users.
Core Features:
- Role-Based Content tailored to specific departments
- AI-Driven Personalization based on user interaction and behavior
- Real-Time Feedback that guides employees through their progress
- Interactive Learning Modules with real-world cybersecurity scenarios
OutThink’s program stands out by aligning with human behavior, which makes training both relevant and actionable.
Coming Soon: Create Your Perfect Training Program
We're excited to announce our upcoming SAT Program Generator: a tool that lets you build custom training experiences tailored to your organization's specific needs, culture, and risk profile.
Whether you're a global enterprise with complex requirements or a growing business with limited resources, you'll be able to create relevant, engaging security content without starting from scratch.
Benefits of the Generator:
- Customization to reflect your organization’s policies, culture, and threats
- Speed and Efficiency in rolling out new training programs
- Scalability that grows with your teams and infrastructure
Measuring what matters
How do you know if your security training is working? Look beyond simple completion rates to metrics that show real impact:
- Completion Rates - Are employees finishing the modules?
- Knowledge Assessments - Do they understand the material?
- Behavioral Change - Are they reporting threats and acting securely?
- Reduction in Incidents - Is there a drop in breaches linked to human error?
These indicators reveal whether your training is creating actual behavioral change – the goal of any security program
Still, many companies struggle to close the awareness gap. According to a Security Magazine report, 67% of organizations say their employees still lack even basic security awareness. This alarming data point underscoresa the urgency of effective, customized training.
Advancing Organizational Cybersecurity Resilience
Cyber threats are becoming more sophisticated, but so are the solutions. Human-centric, personalized training content equips employees to recognize threats and respond effectively. It transforms them from passive bystanders into proactive cybersecurity allies.
The truth is that your employees can be either your greatest vulnerability or your strongest defense. With the right training approach, you transform them from potential security risks into active participants in your organization's protection.
Adaptive security awareness training makes this transformation possible by meeting people where they are, with content that speaks directly to their role, learning style, and specific risks.
OutThink’s innovative Adaptive SAT platform redefines how security awareness training content is designed, delivered, and measured. This evolution marks a shift from compliance-driven checkbox training to culture-driven cybersecurity readiness.