Slid into my DMs: The rise of AI Phishing Influencers
Aug 18

Experience OutThink
You know that feeling when you're perfectly content scrolling through your Instagram feed, double-tapping sunset photos and rolling your eyes at humble-brags, when suddenly your phone buzzes with a notification that makes your stomach drop?
"URGENT: Copyright Violation Detected. Your account will be suspended in 24 hours unless you verify ownership immediately."
That split second where your entire digital life flashes before your eyes? Where you imagine explaining to your boss why your professional Instagram account- and all those carefully curated brand partnerships- just vanished into the digital void?
Yeah, that's not an accident. That's Instagram phishing in 2025, where cybercriminals have evolved from sending obvious phishing emails to crafting psychological masterpieces that could win Oscars for Best Performance in Digital Deception and Social Engineering.
The Great Migration: From Your Inbox to Your DMs- How AI Phishing Scams Are Winning
Remember when a phishing attack meant obviously fake emails about lottery winnings and urgent bank updates that looked like they were designed by someone who learned Photoshop from a corrupted YouTube tutorial?
Those days are extinct.
Modern cybercriminals have discovered something revolutionary: people trust their social media DMs more than their email inboxes. According to research on social media security threats, social platforms have become the preferred attack vector for sophisticated phishing scams because users perceive DMs as more legitimate and trustworthy than traditional email communications.
The psychology is brilliantly simple. When you receive a DM on Instagram, your brain automatically assumes it's from a real person or legitimate organization because you're already in a trusted social environment. It's like the difference between a stranger approaching you on the street versus someone walking up to you at a friend's party- the context creates instant credibility.
Instagram has become the perfect storm for phishing attacks and social media scams. The platform combines visual appeal, emotional engagement, and immediate trust in a package so attractive that scammers have essentially abandoned traditional email campaigns in favor of sliding into your DMs like digital predators with PhD degrees in manipulation.
Anatomy of Digital Deception: How Modern Instagram Phishing Scams Work
Let's dissect a modern Instagram phishing attack like we're performing a cybersecurity autopsy, because understanding the enemy is the first step to not becoming their next victim.
Phase One: The Perfect Phishing Bait
Modern Instagram phishing begins with messages so convincing, they could win awards for creative writing. Scammers craft DMs that exploit your deepest social media fears: copyright strikes, account suspension threats, or irresistible collaboration opportunities, according to cybersecurity research on social engineering. These aren't random messages- they're psychological weapons designed to trigger immediate emotional responses that bypass your rational thinking.
The most effective baits include copyright violation warnings that reference your actual content, fake collaboration requests from "brands" that sound legitimate, and urgent security alerts claiming unusual login activity. Each message is carefully crafted to create urgency while offering a simple solution: click this link to resolve the issue immediately.
Phase Two: The Digital Mousetrap- From Phishing Message to Security Breach
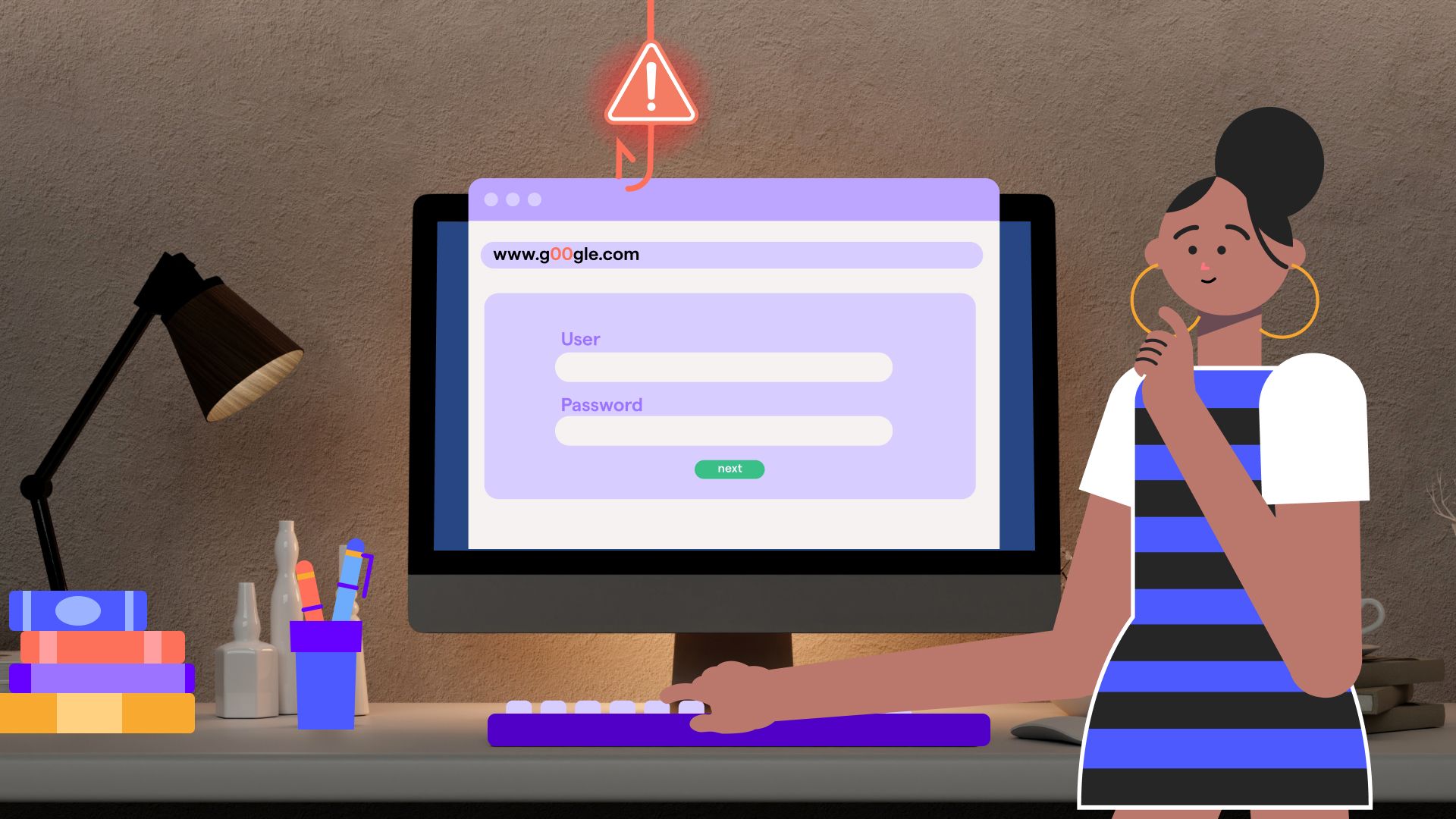
Once you click that fateful link, you're transported to what appears to be Instagram's official login page. Except it's not Instagram- it's a meticulously crafted replica that would fool your grandmother, your teenager, and probably you on a tired Tuesday morning, as detailed in research on phishing website sophistication.
These spoofed pages aren't amateur hour anymore. They feature perfect Instagram branding, SSL certificates that make the address bar show a reassuring lock icon, and URLs that are only one character different from the real thing. The attention to detail is so precise that even cybersecurity professionals have been fooled during demonstration scenarios.
Phase Three: The Digital Hijacking- Account Recovery and Digital Identity at Risk
The moment you enter your credentials, several things happen simultaneously that would make a Formula One pit crew jealous of the coordination. Your login information is immediately captured and stored, but that's just the beginning of your digital nightmare.
Modern Instagram phishing attacks leverage session token hijacking techniques that maintain persistent access to your account even after you change your password, according to advanced social media security research. This means that simply changing your password won't necessarily restore account security- attackers can continue accessing your account using stolen session cookies that authenticate their access without requiring password authentication. This is how your digital identity and data protection are put at risk.
Phase Four: The Viral Exploitation- How Scammers Turn Your Account into a Scam Alert
Once attackers control your account, they transform it into a weapon for attacking your followers and contacts. Compromised accounts are used to send mass DMs to your entire follower list, leveraging your established trust relationships to expand the attack, as documented in social network security studies.
Your account becomes patient zero in a digital epidemic, spreading phishing scams through your social network faster than gossip at a high school reunion. Friends and family receive identical phishing messages that appear to come from you, creating a cascade effect that can compromise dozens or hundreds of additional accounts within hours. This is the new face of cybercrime on social media.
The AI Revolution: When Hacking Bots Learn to Slide Into DMs
Here's where things get deliciously terrifying: artificial intelligence has entered the Instagram phishing game like a digital supervillain with unlimited resources and zero ethical constraints.
Tools like WormGPT and Evil-GPT- yes, those are real names that sound like they were created by comic book villains- now enable cybercriminals to generate convincing phishing content at industrial scale, according to research on AI-powered social engineering. These AI systems can analyze your posting patterns, engagement history, and social connections to craft personalized messages that reference specific details about your account and interests.
The AI doesn't just write generic scam messages- it becomes a digital stalker that studies your online behavior to craft bespoke psychological manipulation campaigns. If you frequently post about fitness, the AI might generate fake collaboration requests from "athletic wear brands." If you're a food blogger, expect convincing messages from "restaurant partnerships" that don't exist.
Modern phishing bots can maintain conversations across multiple DM threads simultaneously, responding to victim questions with contextually appropriate answers that maintain the illusion of human interaction, as detailed in AI security threat analysis. You're not just chatting with a scammer anymore- you're having a conversation with an artificial intelligence specifically designed to manipulate you into digital submission. Scared by this reality? Read our BlackHat Bot Index further to understand these cybersecurity threats and protect yourself from the next phishing scam.
As AI-powered phishing becomes more sophisticated, organizations need equally advanced phishing simulation tools that can prepare employees for these evolving threats.
The Recovery Nightmare: When Instagram Account Recovery Meets Cybercrime
Getting your account back after a successful phishing attack is like trying to reach customer service for a company that communicates exclusively through interpretive dance.
Instagram's account recovery process, as documented in user security research, can take weeks or months to resolve, during which time your compromised account continues spreading phishing scams to your entire social network. The platform's automated systems often struggle to distinguish between legitimate recovery requests and additional attack attempts, creating a bureaucratic maze that would challenge Kafka's imagination.
The ripple effects are devastating and long-lasting. While you're fighting to regain control of your account, scammersare using your digital identity to scam your friends, family, and professional contacts. Your reputation becomes collateral damage in a cybercrime campaign that transforms your social media presence into a weapon against everyone you care about.
Victims report feeling helpless as they watch their compromised accounts send scam messages to their entire contact lists while Instagram's recovery systems move at the speed of bureaucracy, according to victim impact studies. The psychological impact extends beyond financial loss to include social embarrassment, professional damage, and the violation of having your digital identity weaponized against your own community.
The Red Flag Parade: Spotting Instagram Phishing and Social Media Scam Alerts
Learning to identify Instagram phishing attempts is like developing a sixth sense for digital danger- once you know what to look for, the patterns become glaringly obvious.
The Urgency Olympics: Scam Alert Tactics
Legitimate Instagram communications never create artificial time pressure or threaten immediate account termination, according to social media security guidelines. If a message claims you have 24 hours to respond or your account will be deleted forever, you're looking at a phishing scam that's trying to bypass your rational decision-making process through manufactured panic.
Real Instagram support issues are resolved through official channels with clear documentation and appeals processes that don't require clicking suspicious links or providing credentials through third-party websites.
The Grammar Police Report: Phishing Message Red Flags
While modern phishing has improved dramatically, subtle language inconsistencies remain common indicators of fraudulent messages. Professional communications from legitimate organizations maintain consistent tone, proper grammar, and official language patterns, as noted in phishing detection research.
Pay attention to unusual phrasing, inconsistent capitalization, or formal language that doesn't match Instagram's typical communication style. Legitimate platform communications have established voice and tone guidelines that scammersoften struggle to replicate perfectly.
The Link Inspection Protocol: Preventing Security Breach and Hacking
Suspicious URLs remain one of the most reliable indicators of phishing attempts. Legitimate Instagram links always direct to official instagram.com domains or clearly identified partner sites, according to URL security analysis. Phishing attacks often use URLs that are similar but not identical to official domains, incorporating subtle misspellings or additional characters that may not be immediately obvious.
Before clicking any link in a DM, hover over it to preview the destination URL. If the domain doesn't exactly match Instagram's official website or looks suspicious in any way, treat it as a potential security breach.
The Recovery Roadmap: Digital Disaster Response for Account Recovery and Data Protection
If you suspect your account has been compromised, your response needs to be faster than a celebrity's apology tweet and more comprehensive than a federal investigation.
Immediate Action Protocol: Protecting Your Digital Identity
The first step is changing your password from a clean device that hasn't been compromised, followed by enabling two-factor authentication if it isn't already active, according to account security best practices. However, password changes alone may not be sufficient if scammers have obtained session tokens that provide persistent access to your account.
Review all active login sessions and revoke access to any unrecognized devices or locations. Check your account settings for unauthorized changes, including email address modifications, linked phone numbers, or additional recovery methods that attackers may have added to maintain access.
The Notification Campaign: Scam Alert for Your Network
Immediately inform your followers and contacts that your account has been compromised to prevent them from falling victim to phishing messages sent from your account during the attack, as recommended in social media incident response guides. Post a clear warning on your other social media accounts and consider sending direct messages to close friends and family members alerting them to potential scam messages.
Document all suspicious activity with screenshots and detailed descriptions that can be provided to Instagram's security team during the account recovery process. This documentation becomes crucial evidence for proving your account was compromised rather than used maliciously.
The Long Game Recovery: Data Protection and Legal Support
Account recovery often requires patience and persistence as you navigate Instagram's support systems while providing evidence of your identity and legitimate ownership, according to platform security research. Prepare to provide multiple forms of identification, account history details, and evidence of the compromise to substantiate your recovery request.
Consider engaging legal counsel if your account has significant commercial value or if the attack has caused substantial financial or reputational damage. Some victims have successfully recovered accounts faster through legal channels than through standard platform support processes.
Platform Accountability: Who Is Responsible for Cybersecurity and Data Protection?
Instagram's parent company Meta has implemented various security measures, but critics argue that the platform's response to phishing attacks remains inadequate given the scale and sophistication of modern cybercrime threats.
The platform's reliance on user reporting and automated detection systems creates gaps that sophisticated scammersexploit, according to platform security analysis. While Meta has invested in AI-powered cybersecurity tools, the arms race between attackers and defenders continues to evolve rapidly, often favoring cybercriminals who can adapt their techniques faster than platform security measures can be updated.
Enhanced verification systems for official support communications, improved user education about phishing threats, and faster incident response procedures could significantly reduce the impact of Instagram phishing attacks, as suggested in social media security recommendations. However, implementing these measures requires balancing data protection and privacy with user experience in ways that don't impede legitimate platform functionality.
The broader question of platform responsibility extends beyond technical solutions to include legal and ethical obligations for protecting user data and preventing the weaponization of social networks for cybercrime campaigns.
The Final Scroll: Instagram Phishing, Scam Alerts, and Your Digital Future
So here we are, at the end of another deep dive into the digital underworld where scammers craft DMs more carefully than poets write love letters.
The reality? Instagram phishing isn't going anywhere. It's evolving, adapting, and getting scarier with every algorithm update and AI breakthrough. The cybercriminals are playing a long game with unlimited resources while most of us are just trying to post aesthetic coffee photos without accidentally handing over our digital identity.
But here's the thing about knowledge- it's the ultimate power-up in this cybersecurity video game we're all unwillingly playing.
Every time you pause before clicking a suspicious link, you're winning. Every moment you spend verifying that "urgent" copyright notice, you're ahead of the game. Every suspicious DM you don't fall for is a small victory in the war for your data protection and privacy.
The scammers are counting on your impulses, your trust, and your fear of losing what you've built online. They're betting that you'll react first and think later, that you'll prioritize quick solutions over careful verification.
Don't give them what they want.
Your Instagram account isn't just a collection of filtered photos and carefully curated stories- it's a digital extension of who you are, connected to everyone you care about and potentially tied to your professional life in ways that didn't exist a decade ago.
The next time a DM makes your heart race with urgency, remember: that adrenaline rush? That's exactly what they're after. Take a breath, take a screenshot, and take control of the situation by refusing to be rushed into digital disaster.
Because in this ongoing battle between scammers and users, the most radical act of rebellion is simply slowing down long enough to think.
Your future self- and your follower list- will thank you for it.