NIST Recommends New Guidelines for Password Security
Nov 11

Experience OutThink
Why password guidelines matter now more than ever
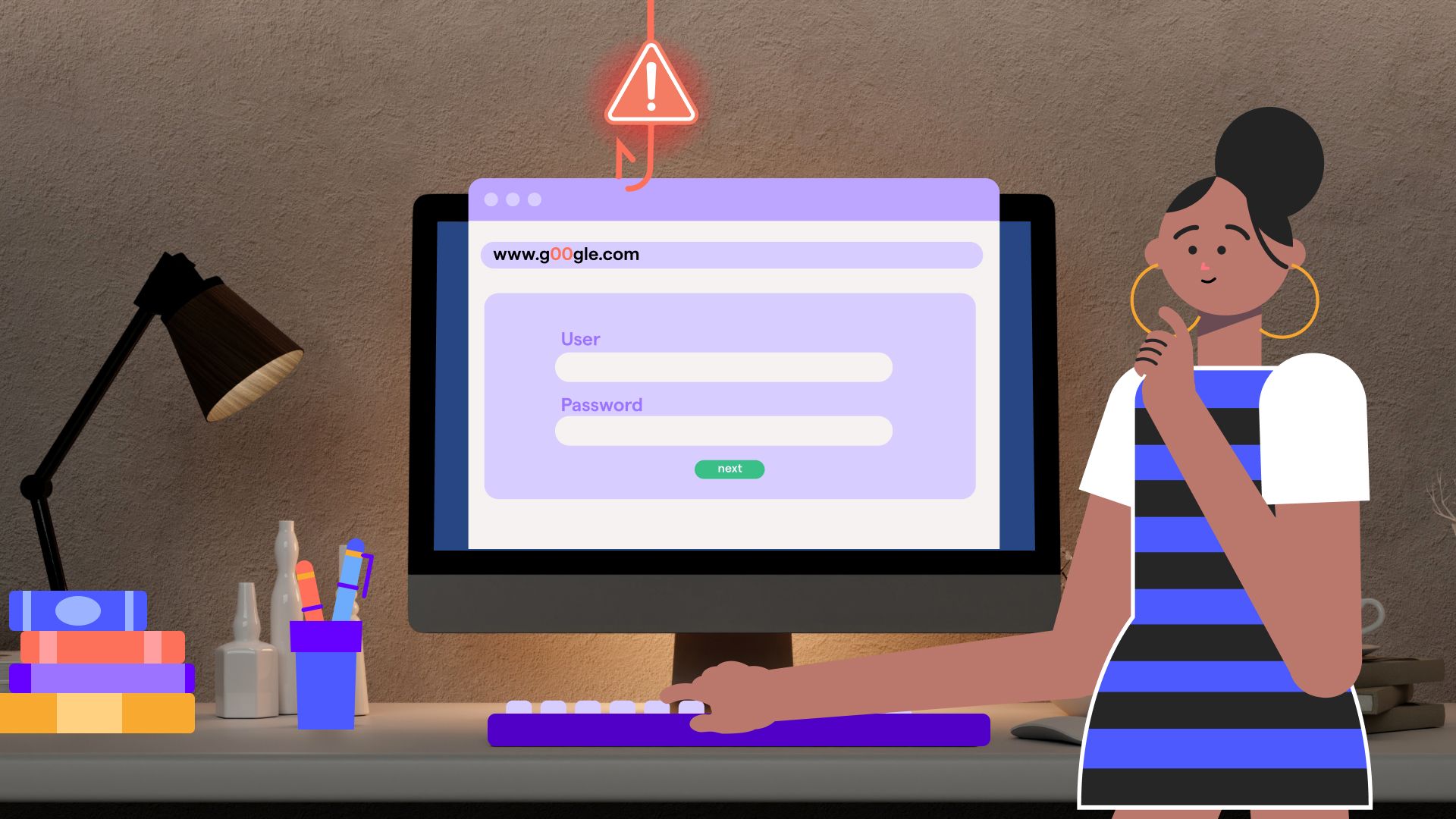
In today's rapidly evolving digital landscape, password security remains one of the most important aspects of protecting sensitive information. Traditional password rules, however, can often feel like more of a burden than a benefit. That’s why the National Institute of Standards and Technology (NIST) has introduced significant updates in its latest guidelines, NIST Special Publication (SP) 800-63-4, aimed at addressing these challenges.
The 5 Key NIST Changes
1. Goodbye to Mandatory Password Resets
One of the most welcomed changes is the elimination of mandatory password changes. In the past, users were often required to reset their passwords at regular intervals. This policy, while well-intended, often resulted in weaker passwords as users would revert to simpler, more predictable choices. Under the new NIST password guidelines, users are only required to change their passwords when there is evidence of a compromise, not on a routine schedule.
What this means for you: You’ll spend less time managing passwords and more time ensuring they are secure from the start. Strong, unique passwords that remain unchanged are far more effective than weak passwords frequently reset.
2. Simplified Password Composition
Gone are the days of forcing users to include a confusing mix of uppercase, lowercase, numbers, and symbols. NIST password guidelines now recommend a focus on length over complexity. Passwords should be at least 8 characters, with an ideal length of 15 or more, and can include any combination of ASCII and Unicode characters - even spaces!
What this means for you: You can now create memorable, user-friendly passphrases that are both secure and easier to remember. Imagine a password like "SunnyDayInParis!" - easy to type, hard to guess.
3. No More Security Questions
Security questions like “What is your mother’s maiden name?” or “What was your first car?” have long been a weak point in authentication processes. NIST password guidelines recommend eliminating knowledge-based authentication altogether, as these answers can often be guessed or obtained through social engineering.
What this means for you: No more worrying about whether your high school mascot is a secure recovery option! Instead, focus on using multifactor authentication (MFA) or stronger account recovery methods.
4. Password Length and Acceptance
Another vital update is the removal of limitations on password length. NIST password guidelines recommend supporting passwords of up to 64 characters. Systems should also allow users to include Unicode characters and spaces in their passwords, providing much more flexibility.
What this means for you: Your passwords can be longer, more diverse, and far more secure. With Unicode support, you can even use non-English characters to strengthen your passwords.
5. Better Verification Practices
Lastly, NIST password guidelines advise against password truncation I.E. the practice of only checking the first few characters of a password. Instead, the entire password should be verified to ensure maximum security.
What this means for you: Truncation creates exploitable loopholes. A focus on comprehensive security checks will help protect your accounts from brute-force attacks and other vulnerabilities.
What This Means for Human-Centric Security
These changes align perfectly with a modern, adaptive approach to cybersecurity that place the user experience at the center of security strategy. Platforms like OutThink, which pioneered Cybersecurity Human Risk Management (CHRM), are already applying these principles through:
- Adaptive training tailored to user behavior
- Risk-based access controls
- Seamless, low-friction security workflows
Embrace the Change
The latest NIST guidelines mark a significant shift toward more user-friendly and effective password management that makes people its priority. By adopting these new practices, organizations can reduce the burden on users while improving overall security.
At OutThink, we are committed to promoting security practices that are not only effective but also practical for everyday use. The changes outlined in NIST SP 800-63-4 are a big step in the right direction, making security more accessible without compromising its integrity.
The latest NIST guidelines reduce friction without compromising on protection. For companies using OutThink, these updates underscore the importance of adaptive, user-aware cybersecurity practices. If you haven’t updated your password policy (or if you’re still relying on outdated awareness training) it’s time to get with the program.
Ready to upgrade your security policies and training? Explore OutThink's Adaptive Security Awareness Training and CHRM platform.