Human Risk Management in Cybersecurity
Bridge the gap in your cybersecurity human risk understanding and power your human risk management program. Manage, reduce and mitigate human risk factors.
Build a 360° understanding of your cybersecurity human risk
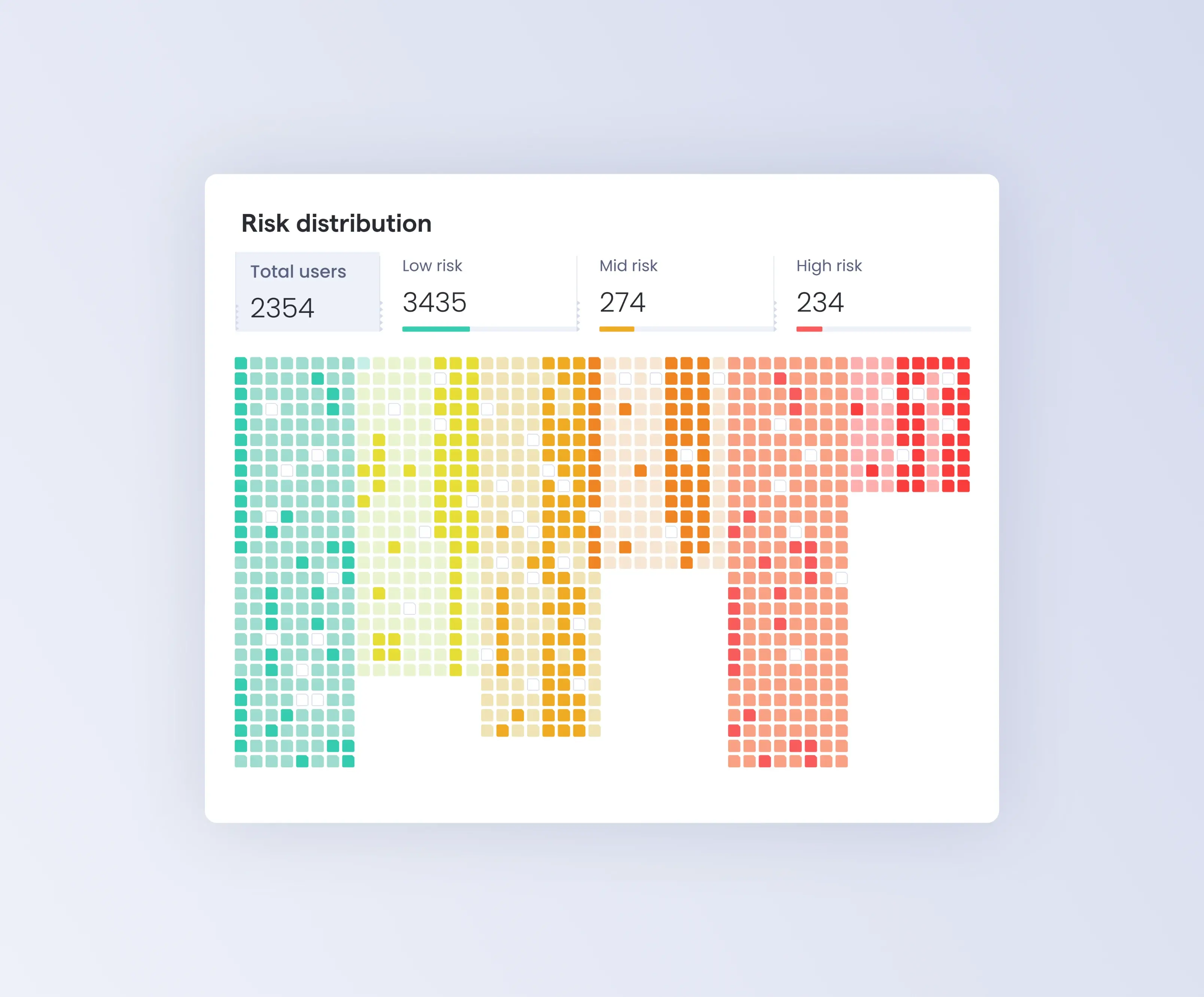
Human risk intelligence
Bring unprecedented visibility to your organization’s cybersecurity human risk and related attributes from learning experiences and connected applications. Provide your security team focus to quickly identify and address your highest risk users.
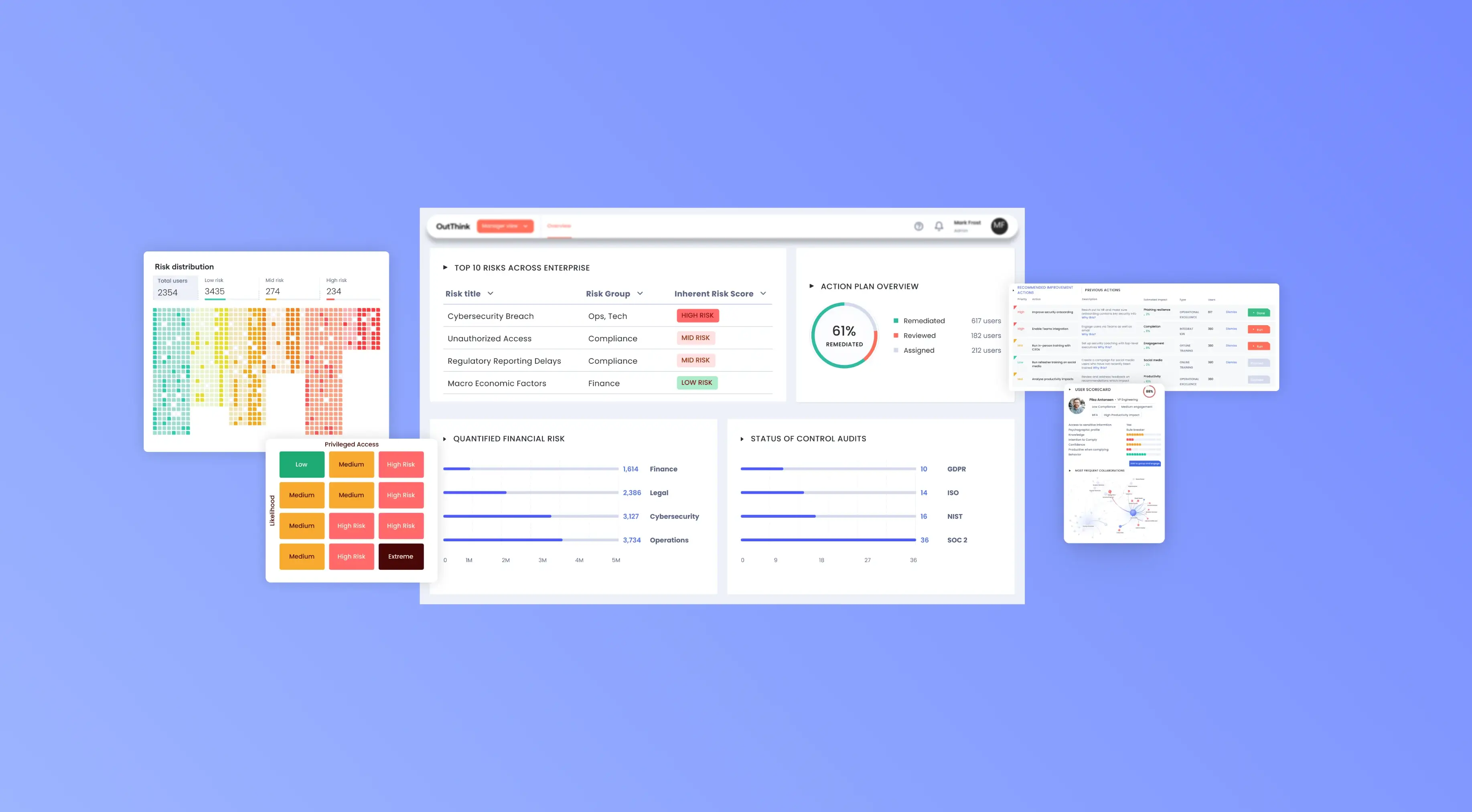
Elevate your risk assessments
People, process, technology. Your risk assessments are incomplete without an understanding of cybersecurity human risk. Ingest OutThink human risk insights to take your GRC assessments to the next level.
Decrease your organization’s aggregated cybersecurity human risk exposure
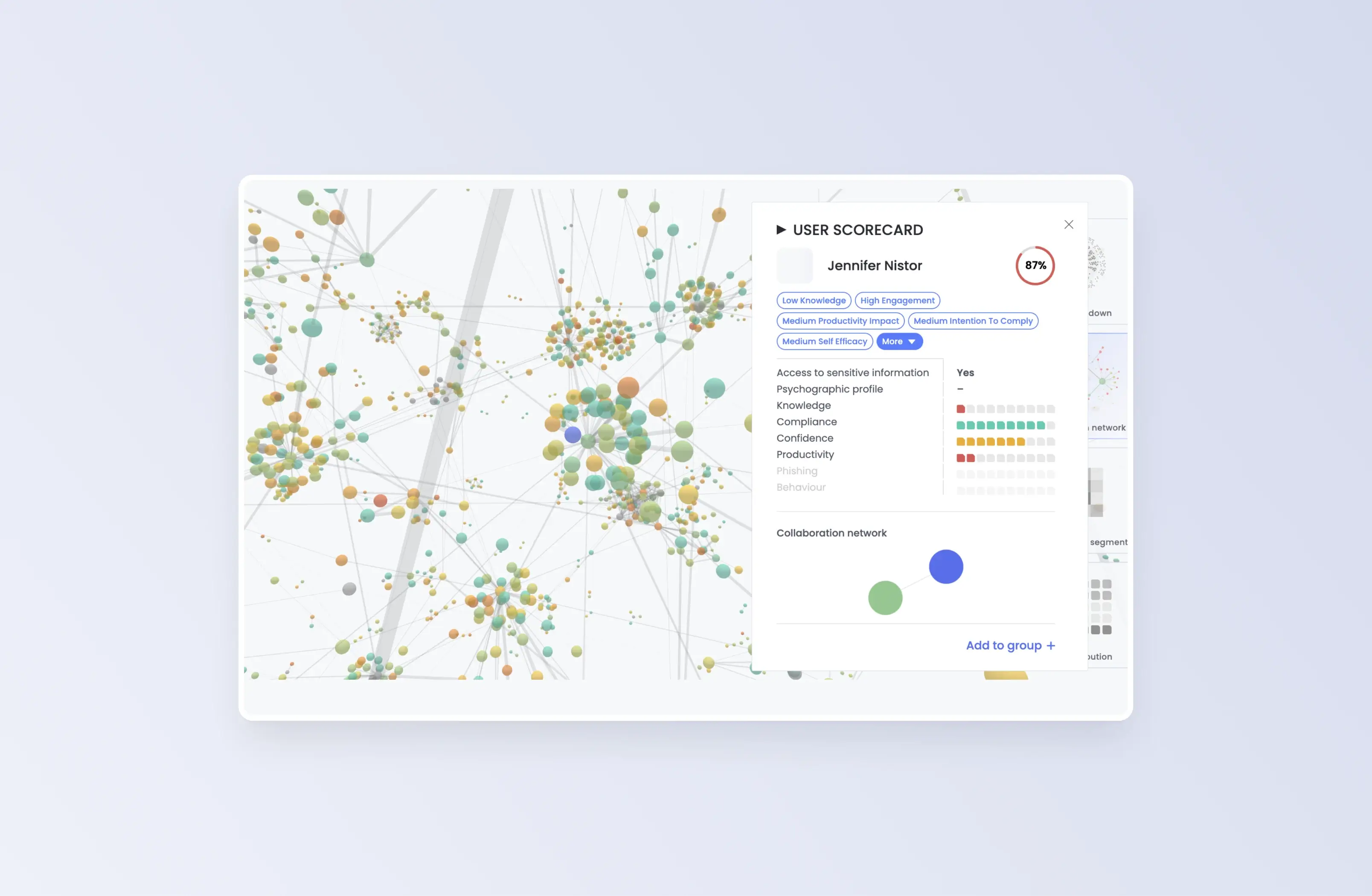
Human lateral movement analysis
Identify high-risk individuals linked closely to users with privileged access, thereby extending risk exposure through relational connections.
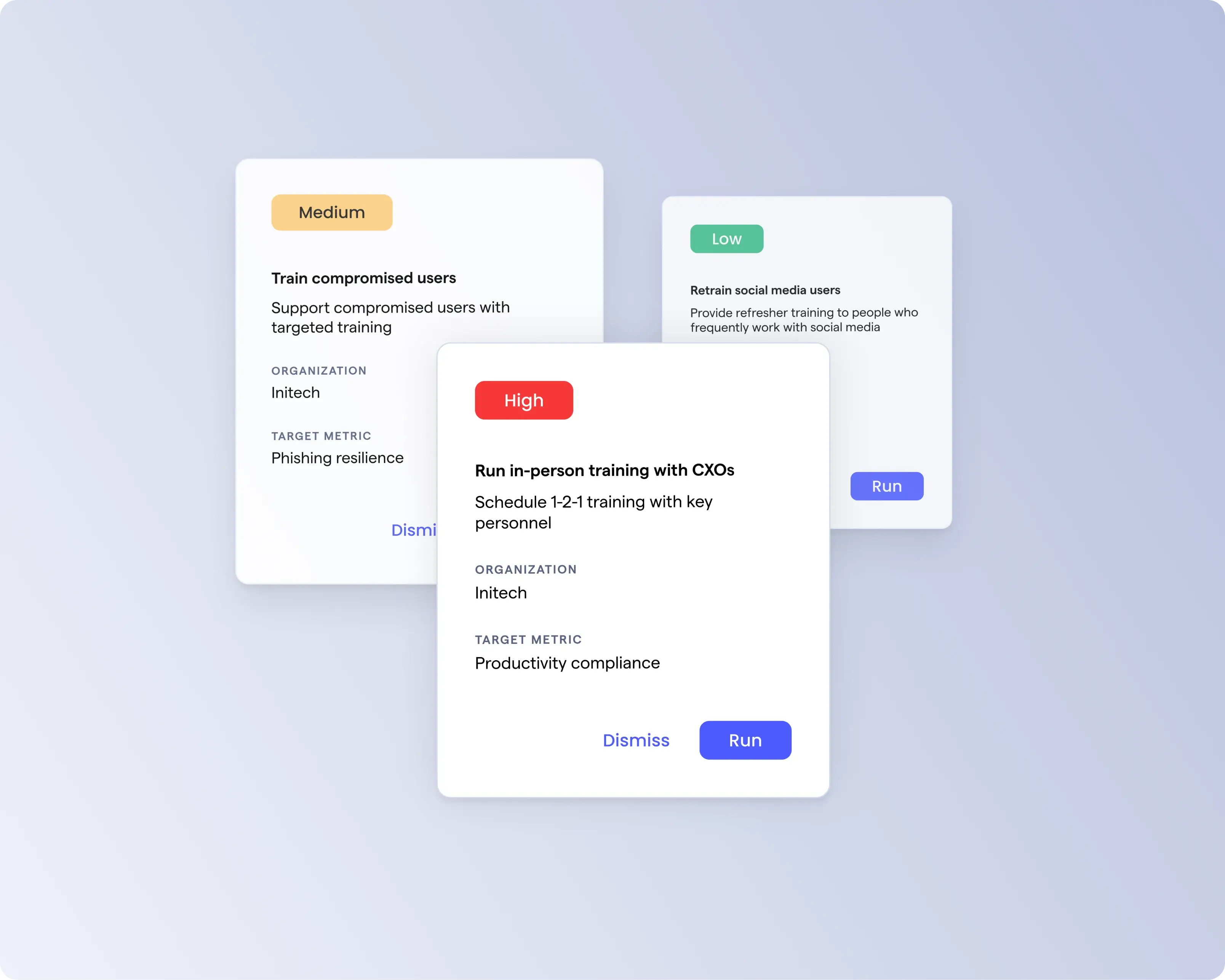
Recommended improvement actions
Let the OutThink platform handle the heavy lifting by identifying high-risk actions and providing insights and recommendations, so you can focus on high-impact activities.
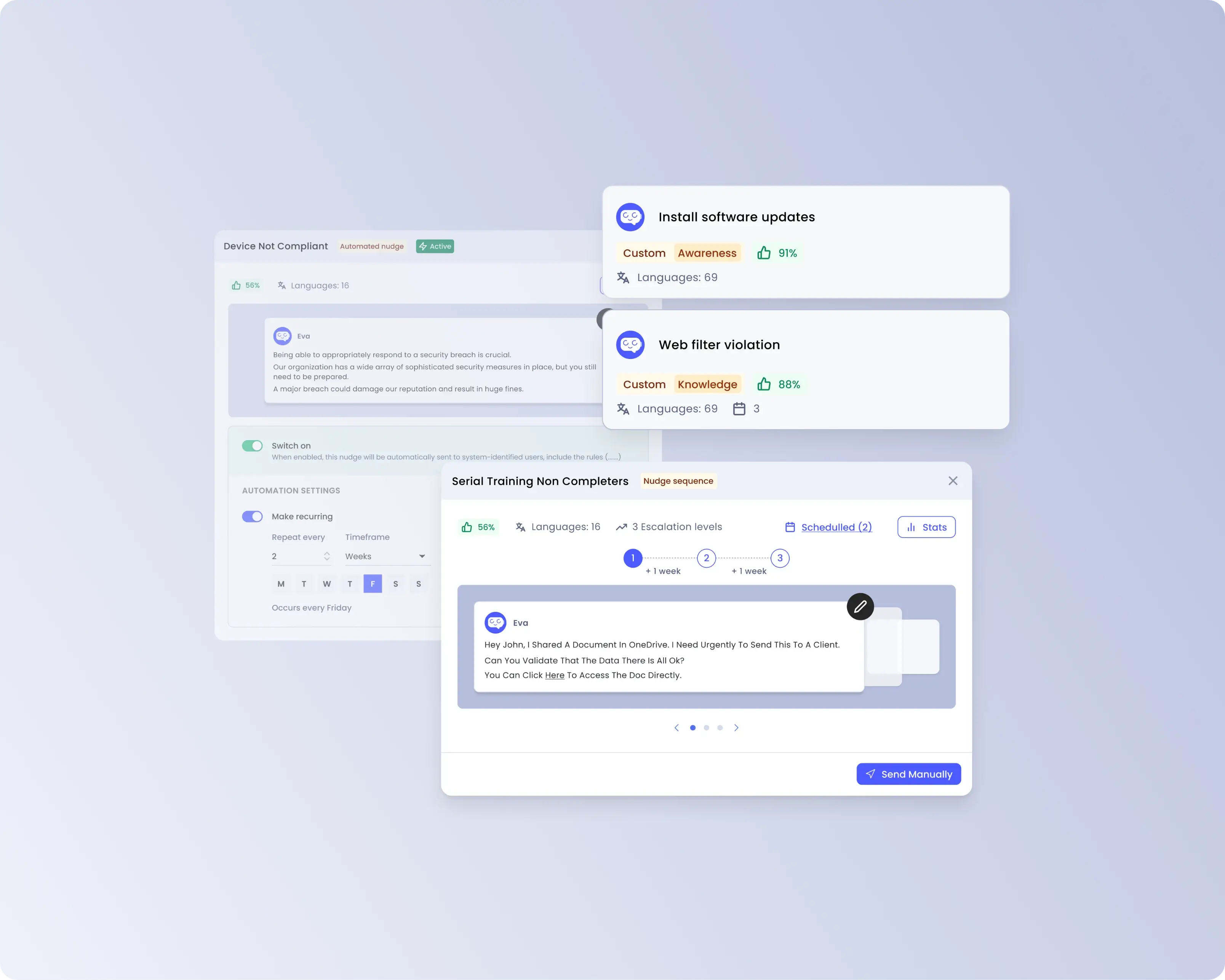
Just-in-time nudges
Offer your users positive reinforcement as well as timely information when specific risks arise.
Adaptive security at your fingertips
Security teams are stretched thin. Triage incidents based on criticality, avoid privilege creep, and ensure your users always have appropriate security and access permissions.
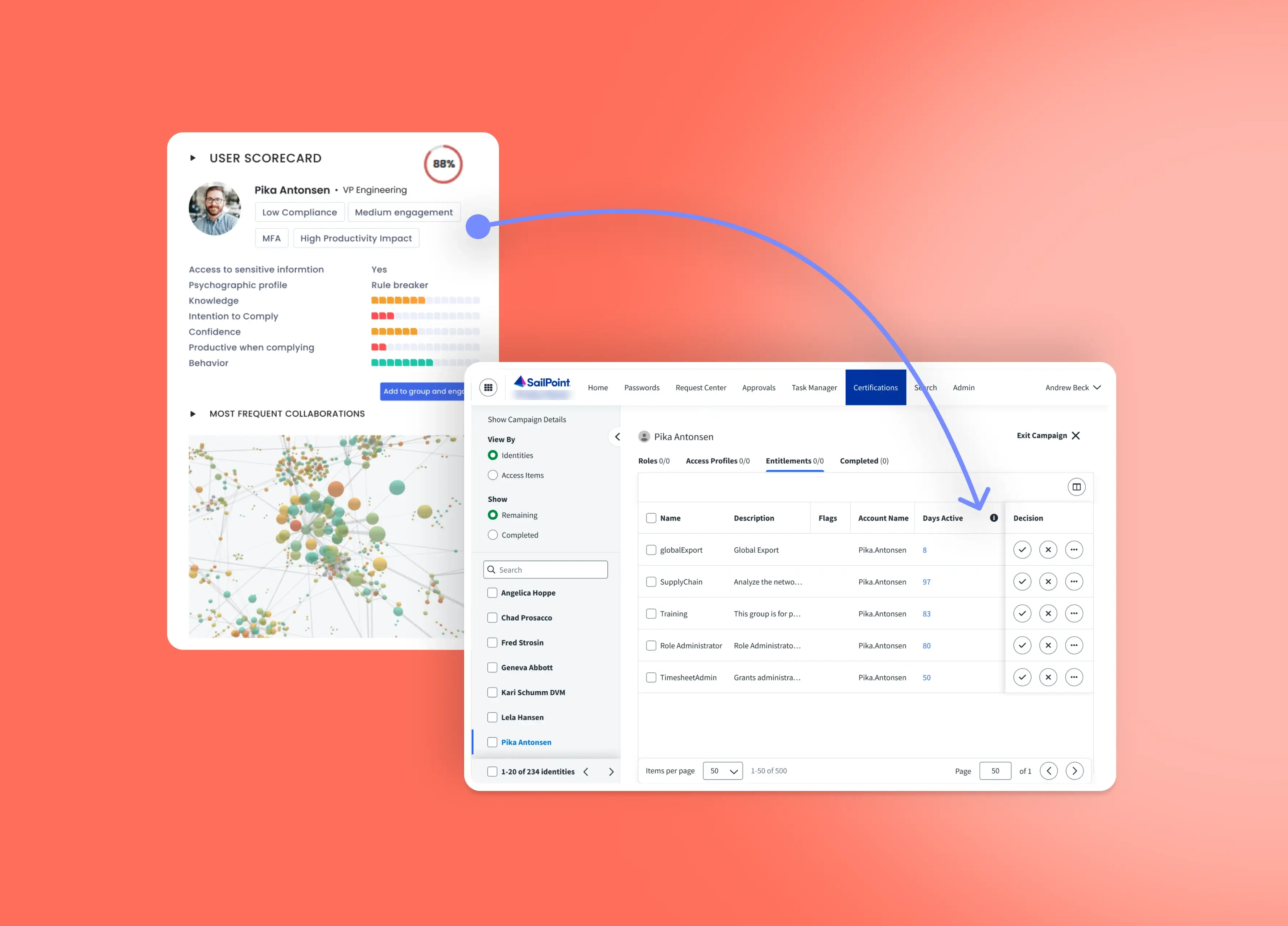
Adaptive, risk-based user permissionsCOMING SOON
Adhere to principle of least privilege with adaptive user access to critical systems. Also approve download requests, and policy exceptions based on data-driven insights on users’ cyber risk portraits
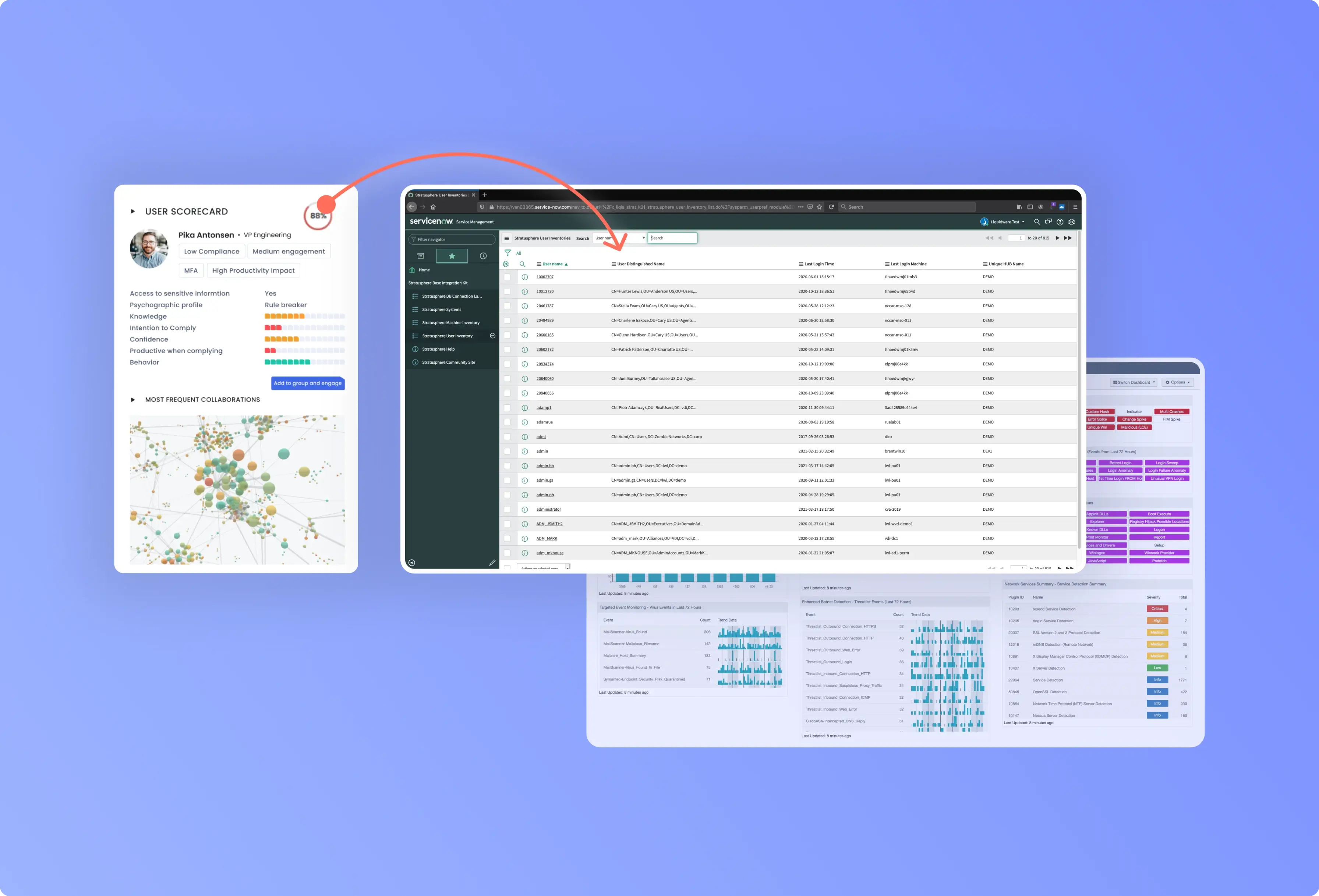
Prioritize incident triagingCOMING SOON
SOC and IT teams are overwhelmed with alerts. Integrate a deep understanding of users' cyber risk portraits into your workflows to prioritize incident triage
Reduce cyber human risk through security advocacy
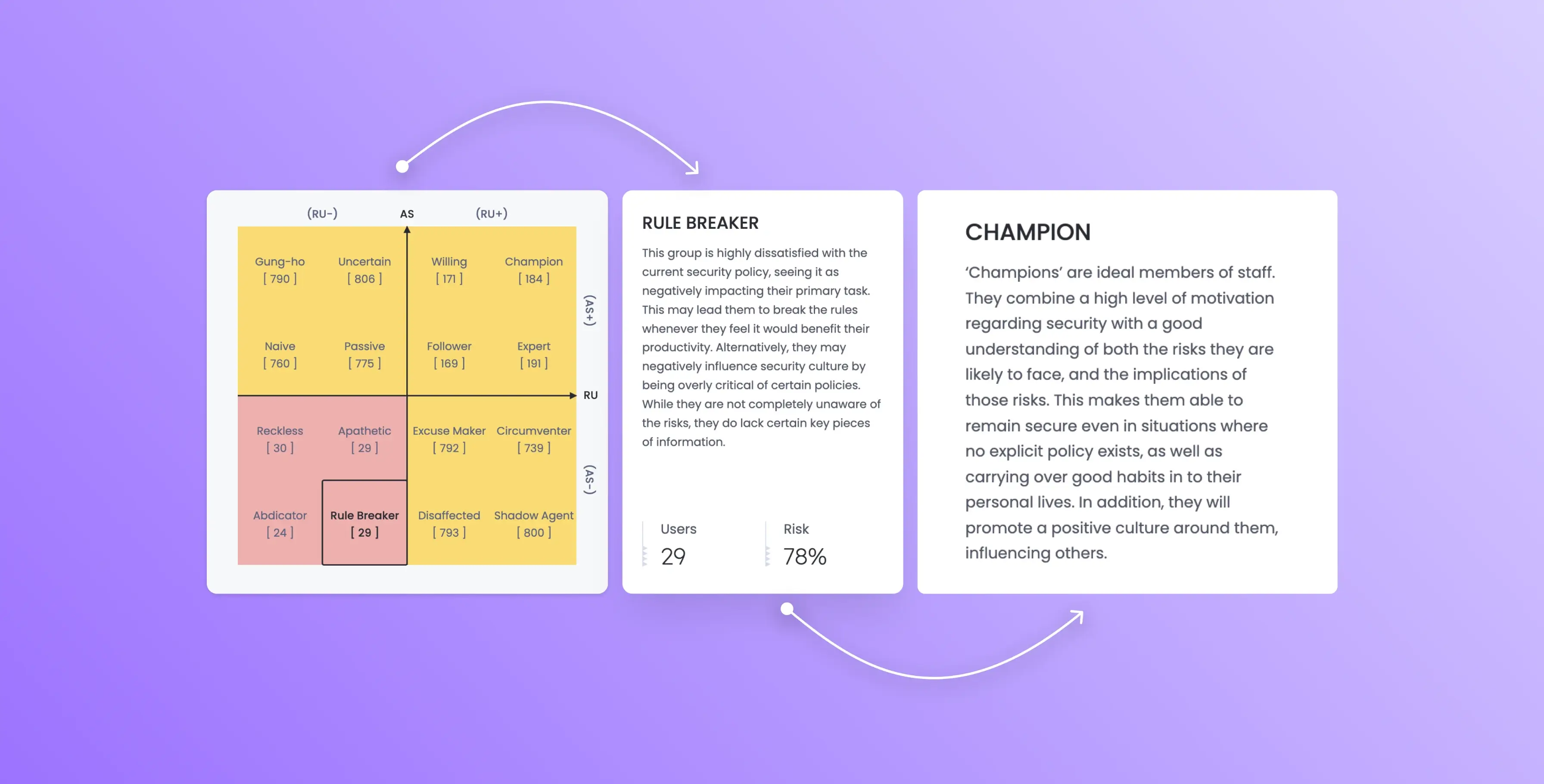
Psychographic segmentation: Based on the pioneering work of our Chief Scientific Advisor, Professor Angela Sasse (FREng). Angela is the founder of the Research Institute in Science of Cyber Security at University College London. Using the “Johari window” paradigm developed in behavioral psychology, this chart divides your user population into 16 psychographic segments.
One of the standout features is Human Risk intelligence, which provides insights about high-risk employees. This, coupled with the ability to organize employees into groups, is highly valuable in planning ..and imparting knowledge about today's cyber and information security threats.

OutThink is a representative vendor in the Human Risk Management category
Forrester has Recognized OutThink as a Leading Vendor in the the Human Risk Management Solutions Category.
Explore other use cases
Explore OutThink products









