Coming soon
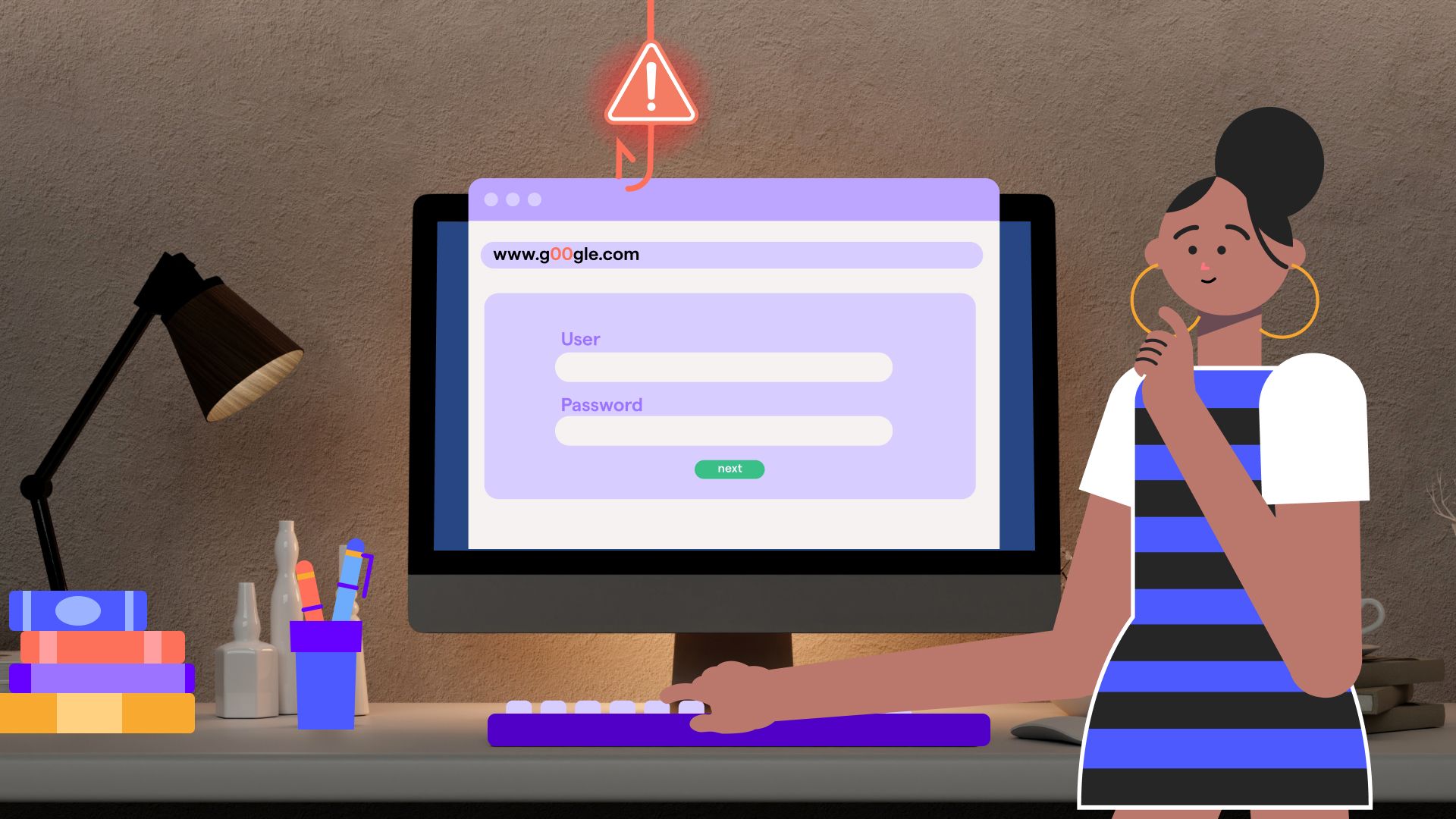
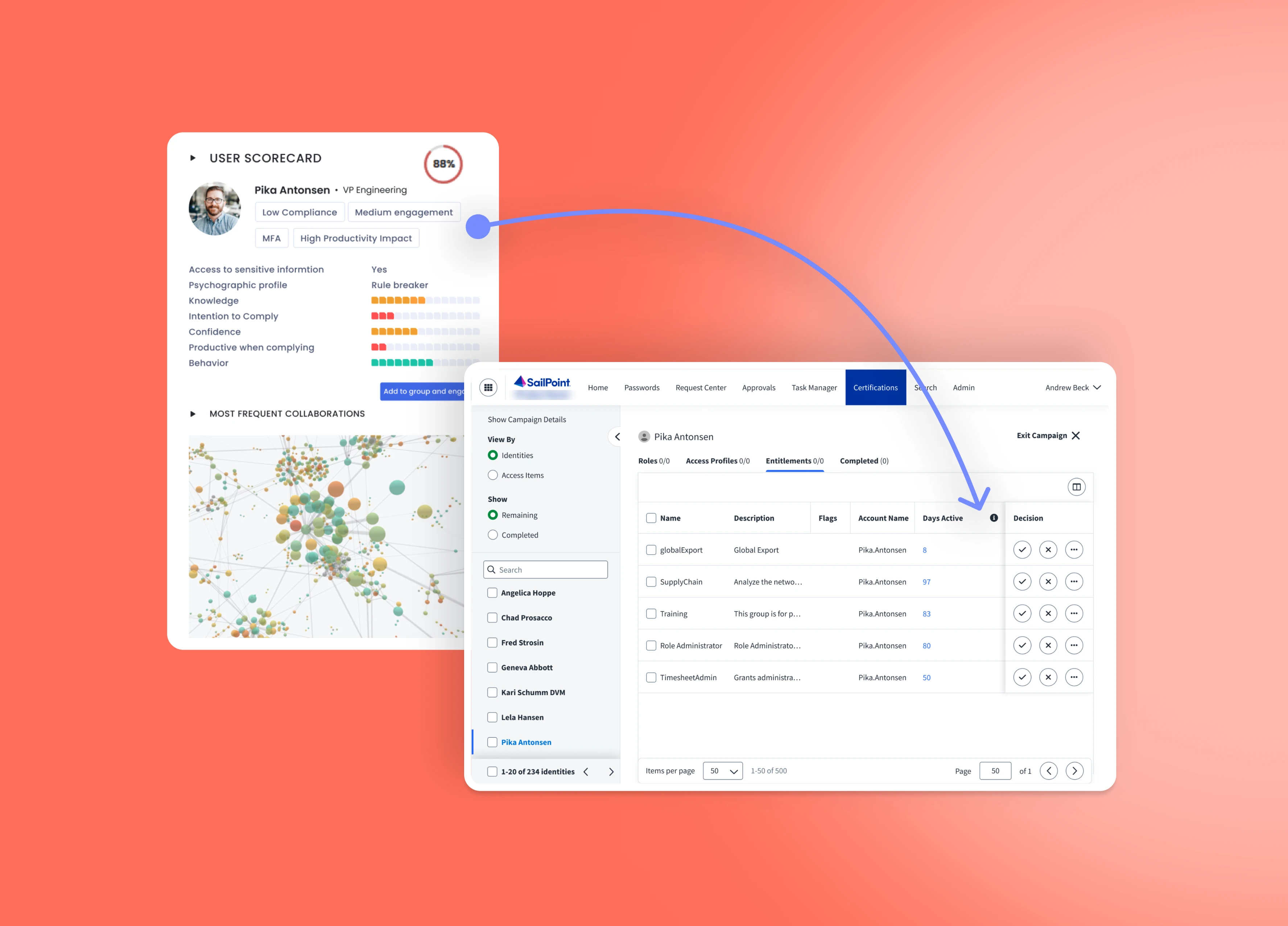
No two users are the same so there’s no reason to treat them the same. Prevent human-initiated security incidents with strict, automated conditional access rules based on real cyber risk intelligence.
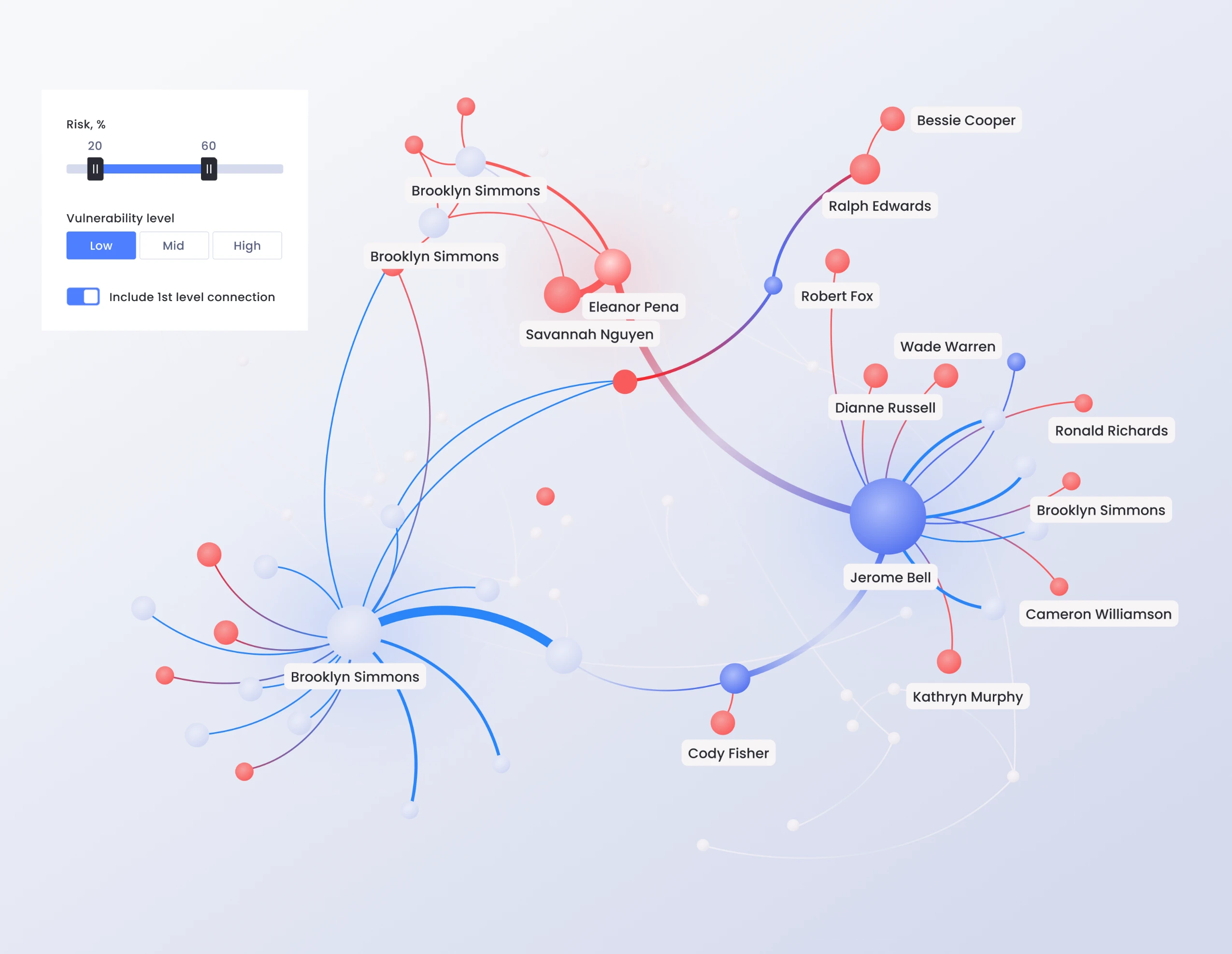
Don’t wait for high risk users to change behaviors
On average 8% of users cause 80% of human-initiated security incidents, out of which 2.7% have privileged access, handle sensitive data and are high risk. Get laser focused on high risk users to protect your organization.
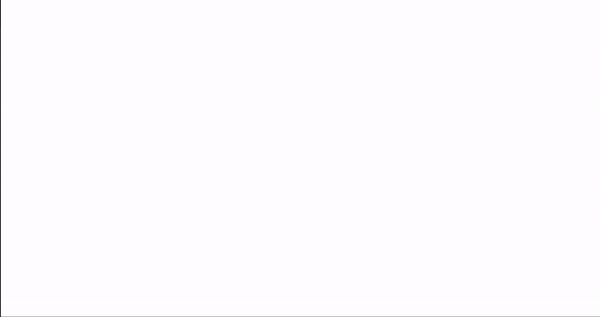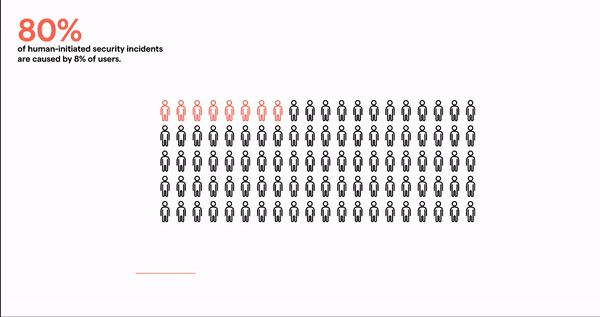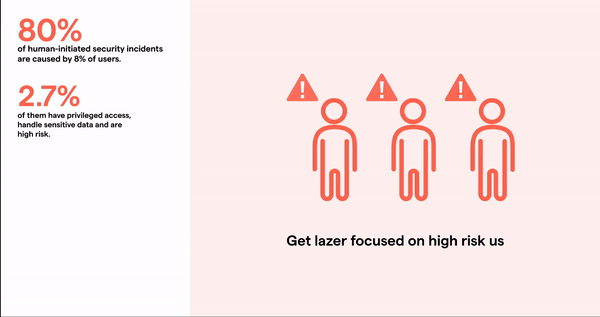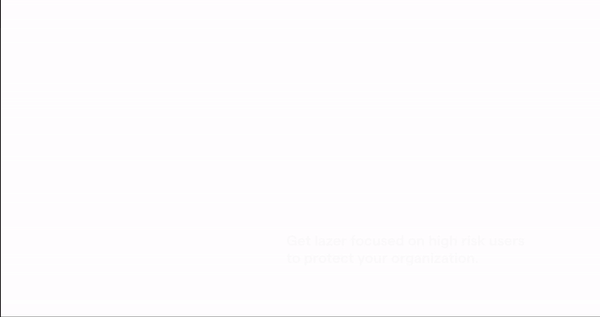
Prevent human-initiated security incidents
Utilize a set of powerful outbound actions to automate conditional access across identity platforms for users based on observed attitudes, behaviors, and real security events. Enforce actions such as frequent re-authentication, relog-ins and session management to protect your organization.
No two users are the same so there’s no reason to treat them the same
Prevent human-initiated security incidents with strict, automated conditional access rules based on real cyber risk intelligence.
Great tool. I've used a few of these and this is the first platform that has a strong vision to accompany the technology. There's plenty of smart features that can increase security, but it's the overall mission of the company that I find quite compelling, especially compared to others.

OutThink is a representative vendor in the Human Risk Management category
Forrester has Recognized OutThink as a Leading Vendor in the the Human Risk Management Solutions Category.
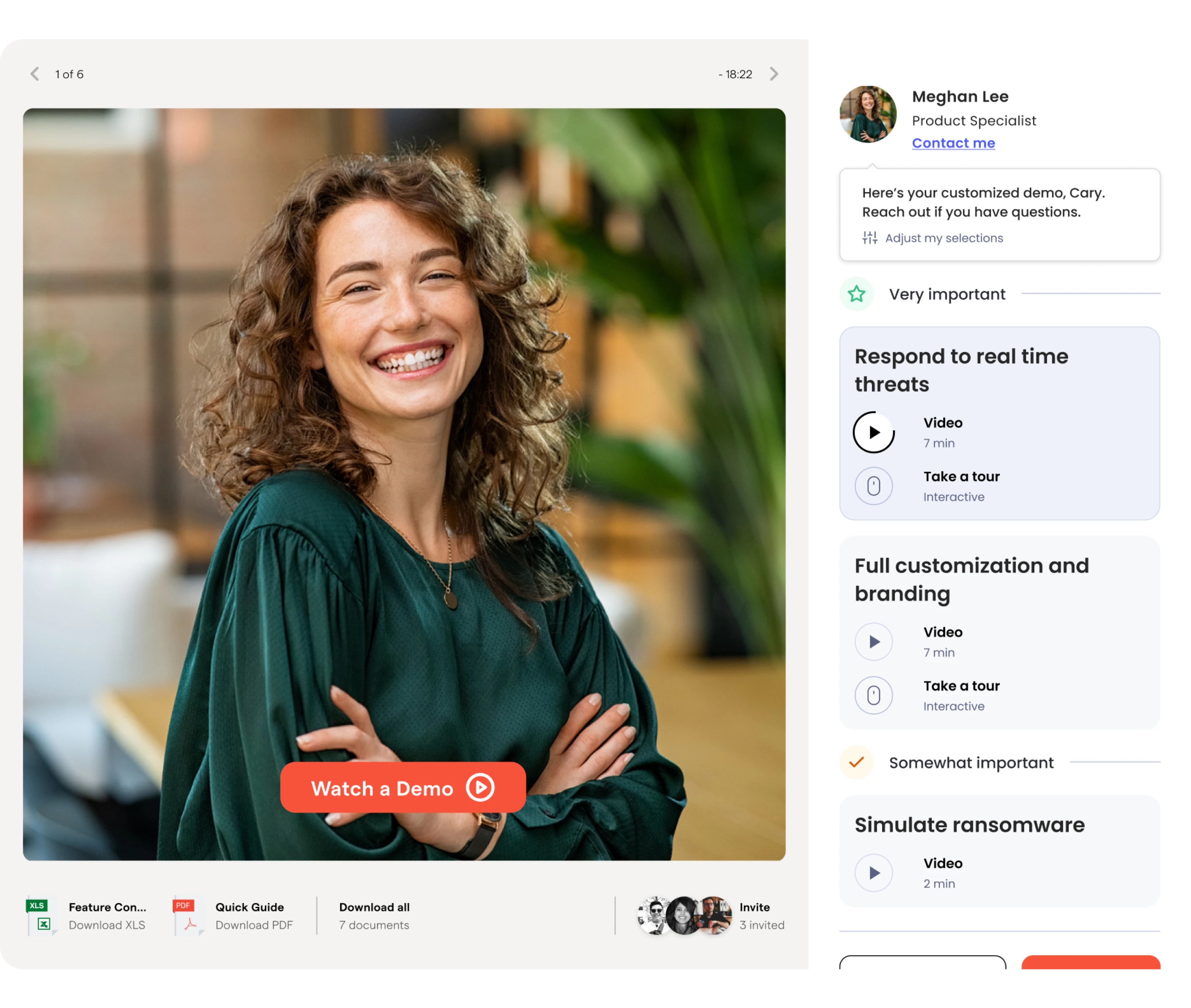
Explore other use cases
Explore OutThink products