Human Risk Intelligence & Conditional Access
Quantify your organization’s cybersecurity human risk and take action to protect and succeed.
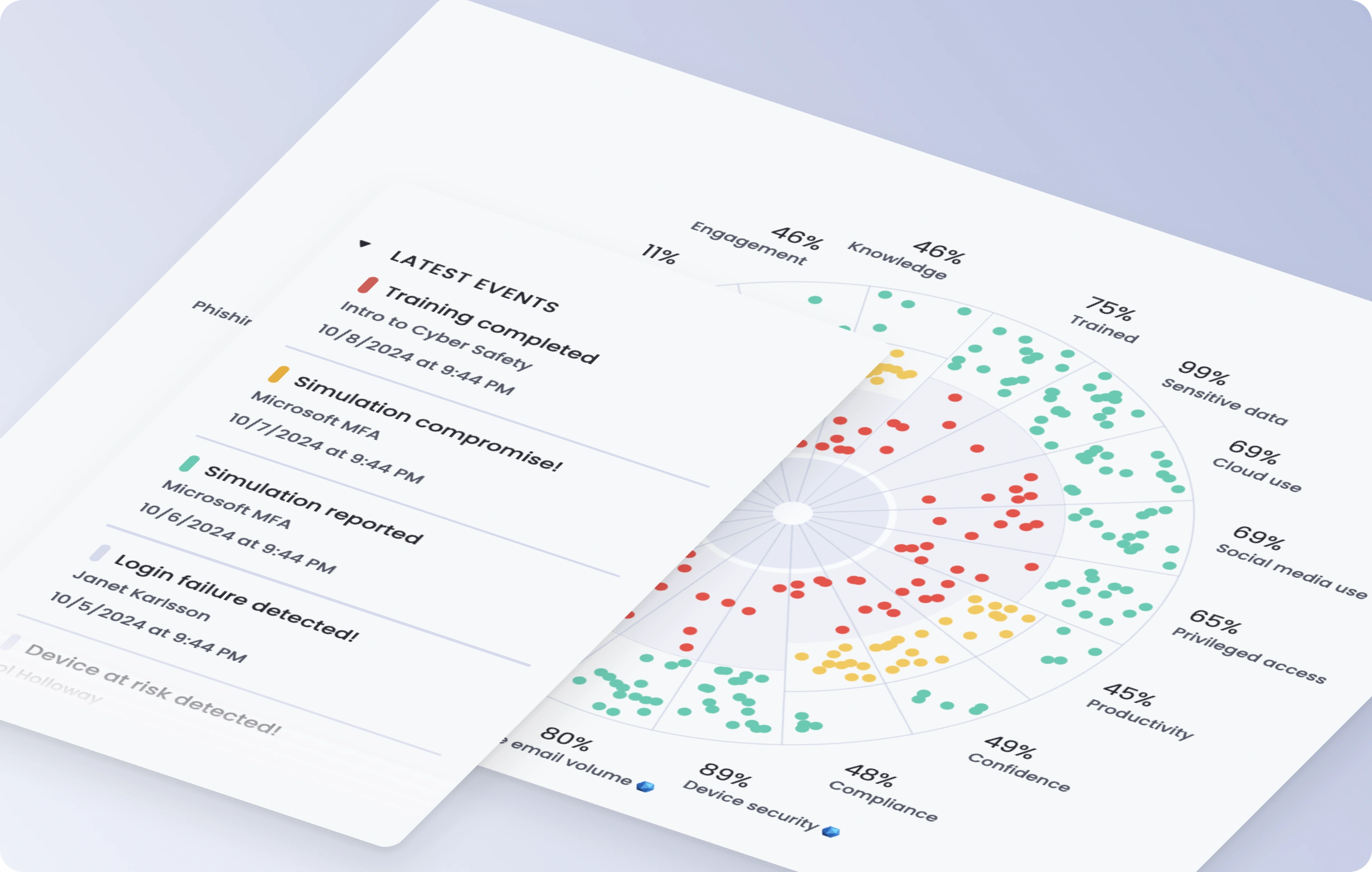
Know what your users are up against
Build a 360 degree view of your users’ cyber human risk vulnerability.
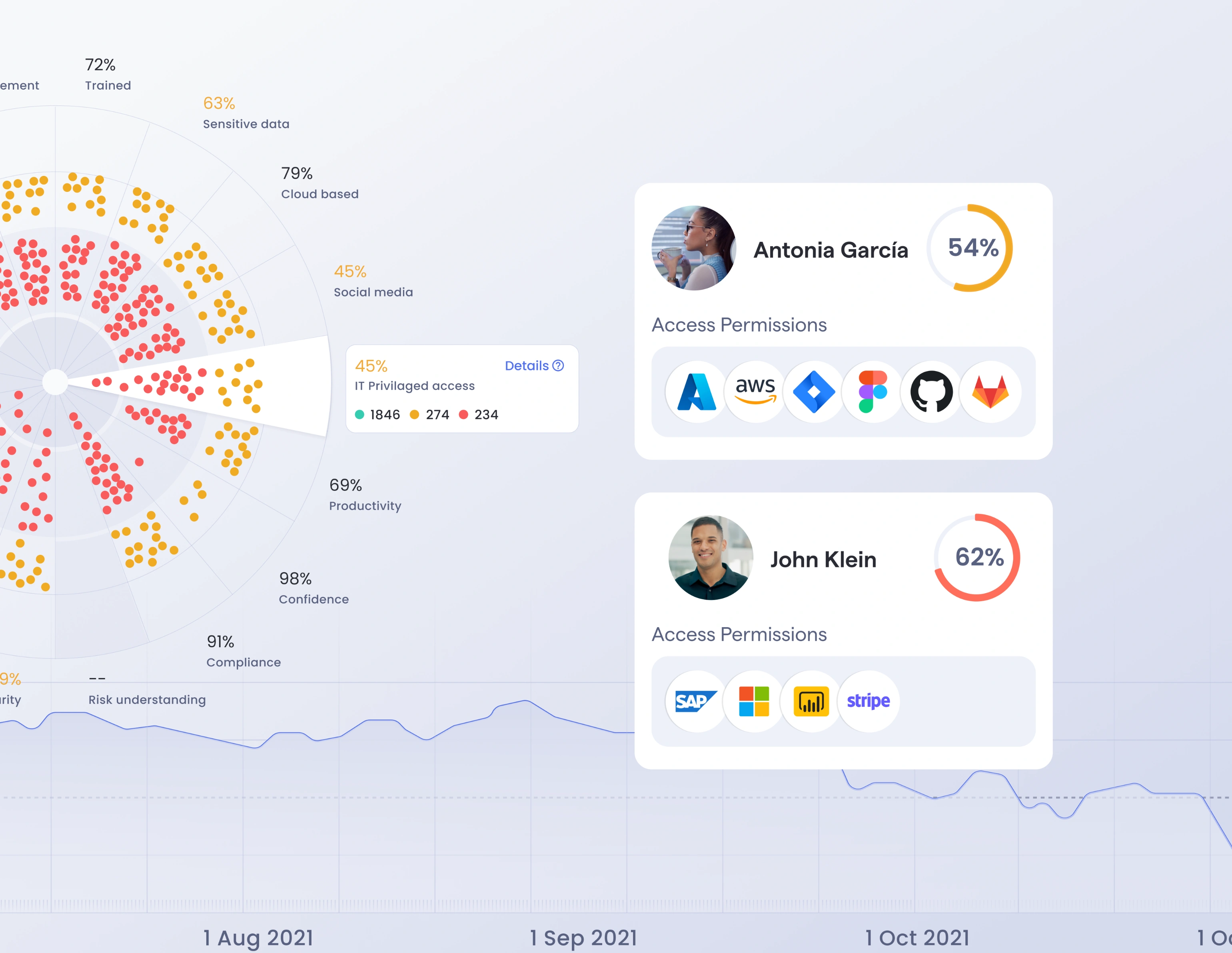
Granular threat and risk scorecards
Gain insight to each user’s role, performance, and engagement in adaptive security awareness training and phishing simulations. Address behaviors which require most attention.
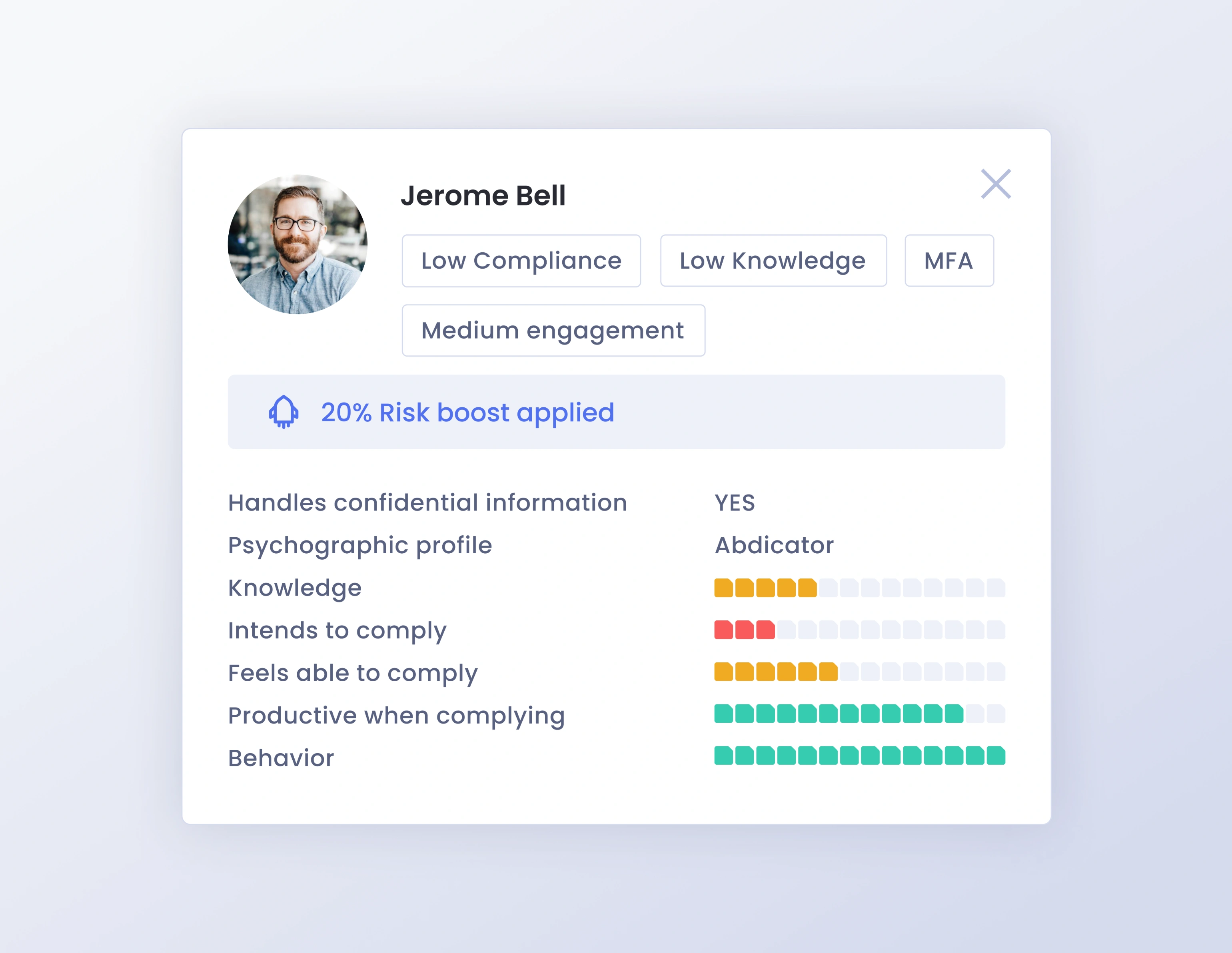
Real-world behavior insights
Integrate with your security systems to enrich understanding of how your people behave in real-world scenarios. Gain a more precise view of each user’s vulnerabilities and progress over time.
See the forest for the trees
Cybersecurity human risk is not uniform across users and different groups face varying threats based on their roles, functions and public exposure. Get a comprehensive, drillable view of your organization’s cyber human risk, backed by decades of cybersecurity experience and scientific research.

Risk Breakdown
Gain a bird’s eye view of your organization’s cybersecurity human risk.
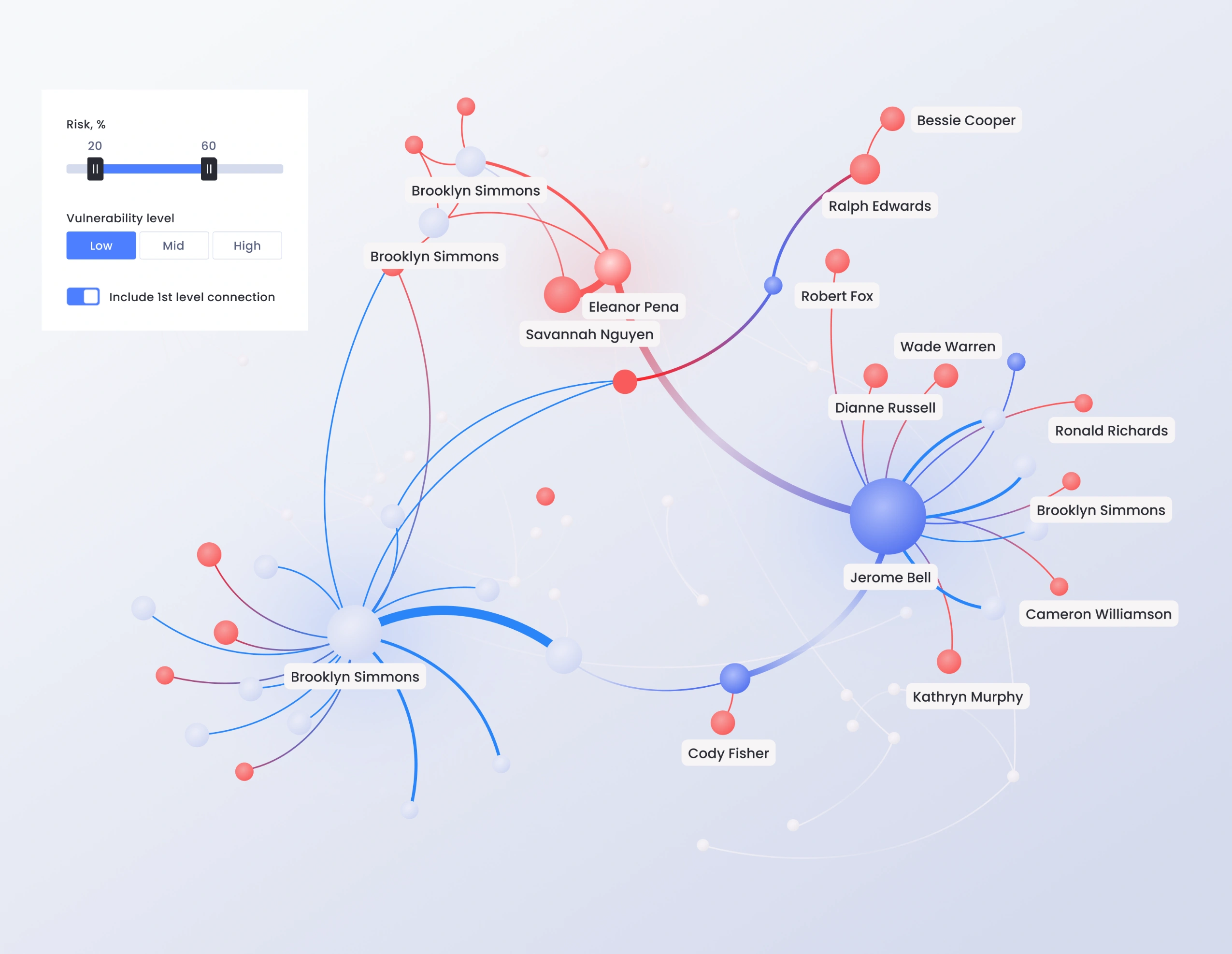
Collaboration Network
Identify high-risk users working closely with vulnerable stakeholders. Implement targeted actions to mitigate these risks.

View risk through behavioral psychology
Designed with the pioneering work of our Chief Scientific Advisor, Professor Angela Sasse (FREng), founder of the Research Institute in Science of Cyber Security at University College London.
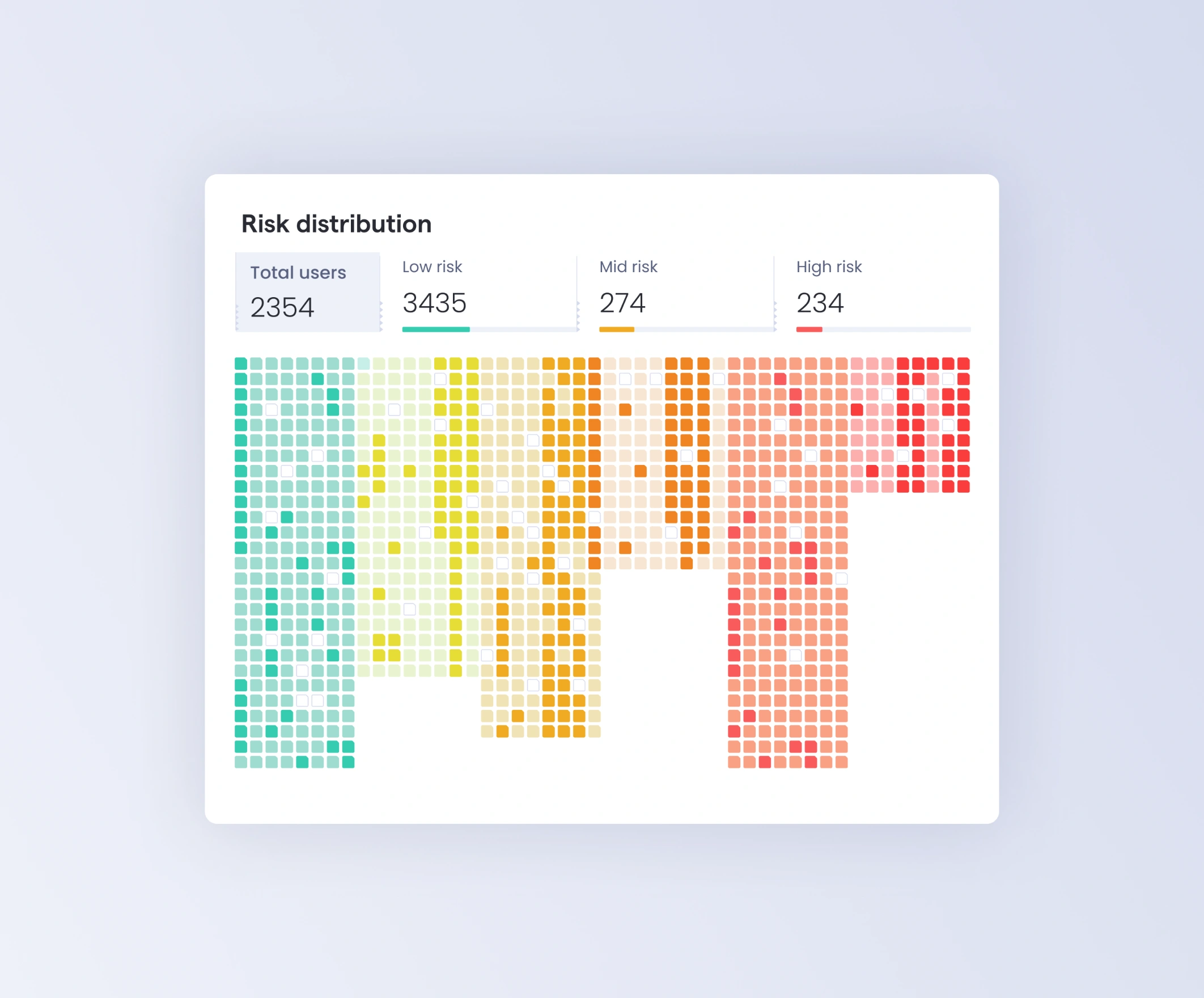
Risk Distribution
Understand higher risk areas of the organization to unlock targeted risk mitigation.
OutThink's human risk intelligence approach has been a real standout for us. It goes beyond just training. This helps us understand employee behavior and tailor content to address specific risks.

Effortlessly address multi-layered human risk challenges
Organizations are complex, and security teams are stretched thin.
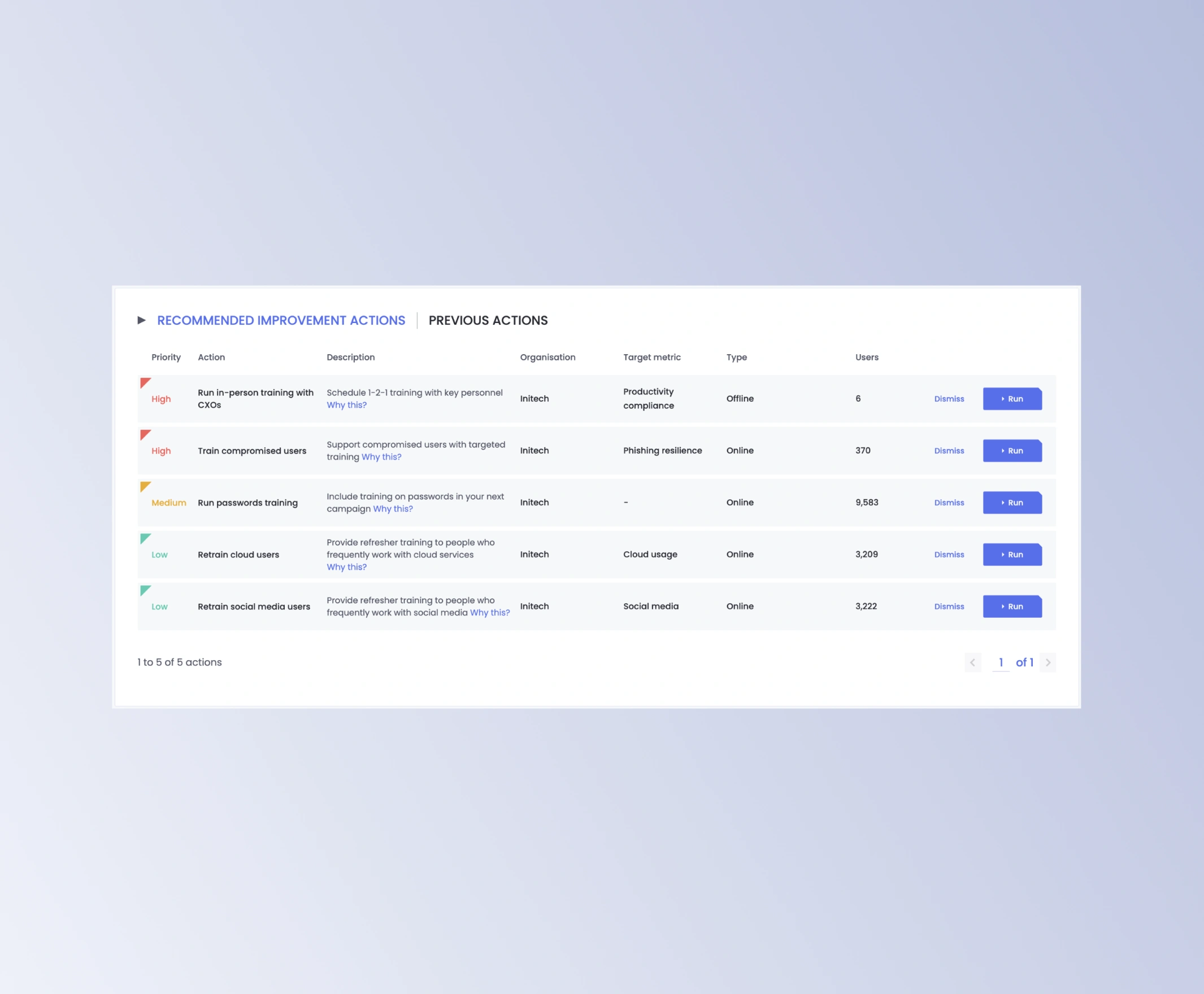
Let the OutThink platform handle the heavy lifting by identifying high-risk actions and providing insights and recommendations, so you can focus on engagement with further high-impact security activities.
Utilize a set of powerful outbound actions to automate conditional access across identity platforms for users based on observed attitudes, behaviors, and real security events. Enforce actions such as frequent re-authentication, relog-ins and session management to protect your organization.
Adhere to principle of least privilege with adaptive user access to critical systems. Also approve download requests, and policy exceptions based on data-driven insights on users’ cyber risk portraits
OutThink is recognized as a representative vendor in Security Awareness and Human Risk Management
Gartner has Recognized OutThink as a Leading Representative Provider in the Security Behavior and Culture Programs (SBCP) Category.
Forrester has recognized OutThink as a Leading Vendor in the the Human Risk Management Solutions Category.









