Human Risk Management API
Save time and reduce costs. Integrate OutThink with other security applications and workflows to further personalize your cybersecurity human risk management approach.
Build adaptive security
Push custom security events and behavioral data related to user-specific risks to and from OutThink. Track unique industry-specific threats and behaviors to enhance user performance and inform conditional access configurations.
Learn more about
Drive external reporting from OutThink
Extract data from OutThink to create custom dashboards and reports, integrating with your multiple internal systems. Use existing Business Intelligence (BI) tools or a Security Information Event Manager (SIEM) for enterprise-wide compliance, KPI, and risk dashboards.

OutThink’s valuable integration capabilities allowed us to merge our diverse data sources into a unified system. The robust dashboards and reporting features offered by OutThink have significantly enhanced our ability to monitor and improve our cybersecurity practices.

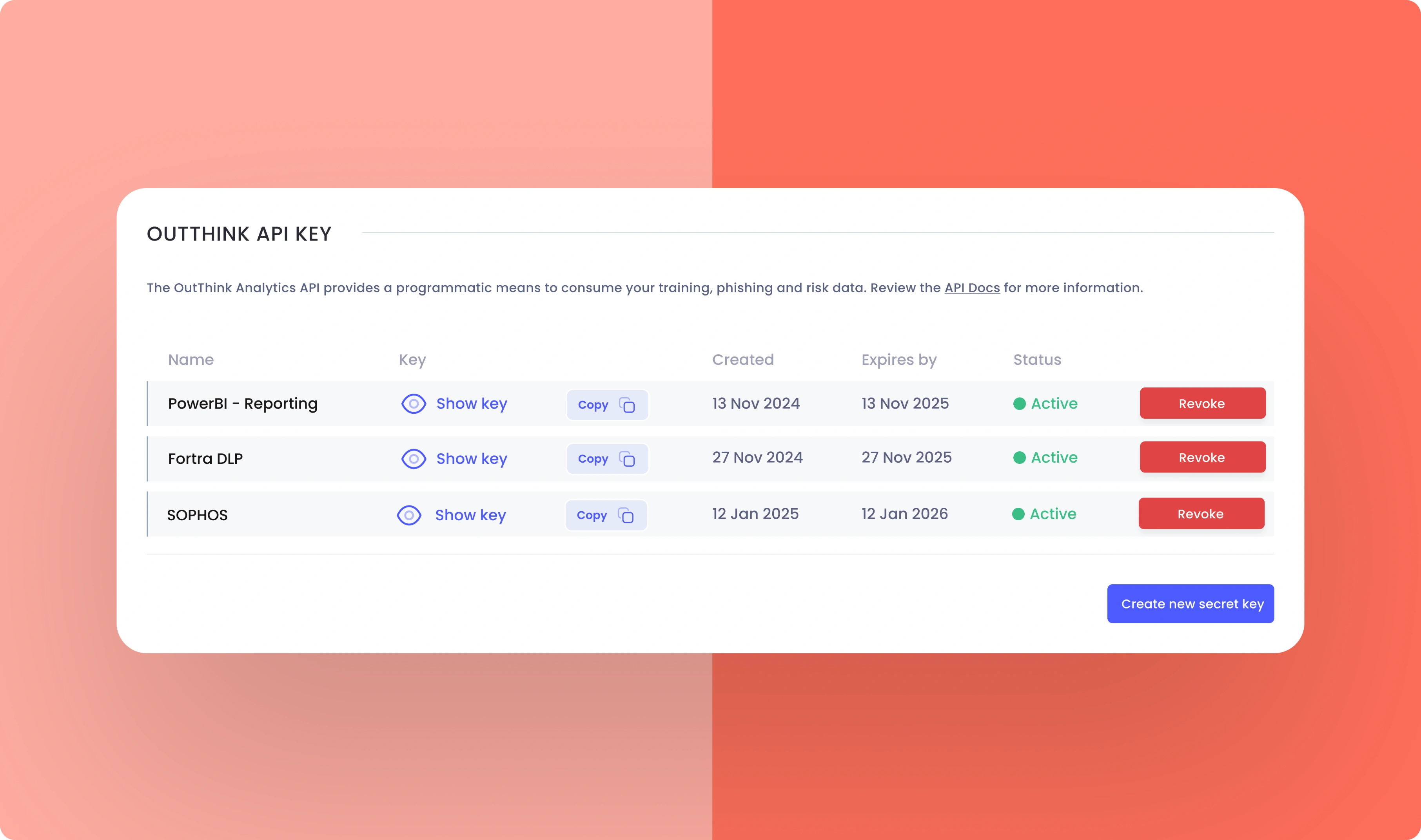
Configurable, secure and documented API keys
Built on the popular REST architectural style, OutThink's API is easy to implement, configure, and use. Security and authentication can be managed by your platform administrators, with the ability to granularly scope, grant and revoke permissions for applications as needed.And with robust API documentation, you and your team can get up and running quickly.
The APIs are versatile enough to pull a multi-dimensional view across all employees, departments and roles. A lot of depth in the data, allowing for new levels of insights from a human risk and overall security risk standpoint.
