Wouldn’t it be nice to know what all your users think about your security policy, your security controls or even the Security team overall? Well, we believe it’s not just nice to have, but a must-have. The first step of engaging your users in cybersecurity is listening to them. The next step is speaking with them about topics THEY care about, provide better guidance around security policy, and determine which policy exceptions make the most sense. Dealing in the messy realm of humans, people engage when they feel heard and they are being talked to, rather than talked DOWN to. This builds a culture of trust and engagement between Security and employees at large.
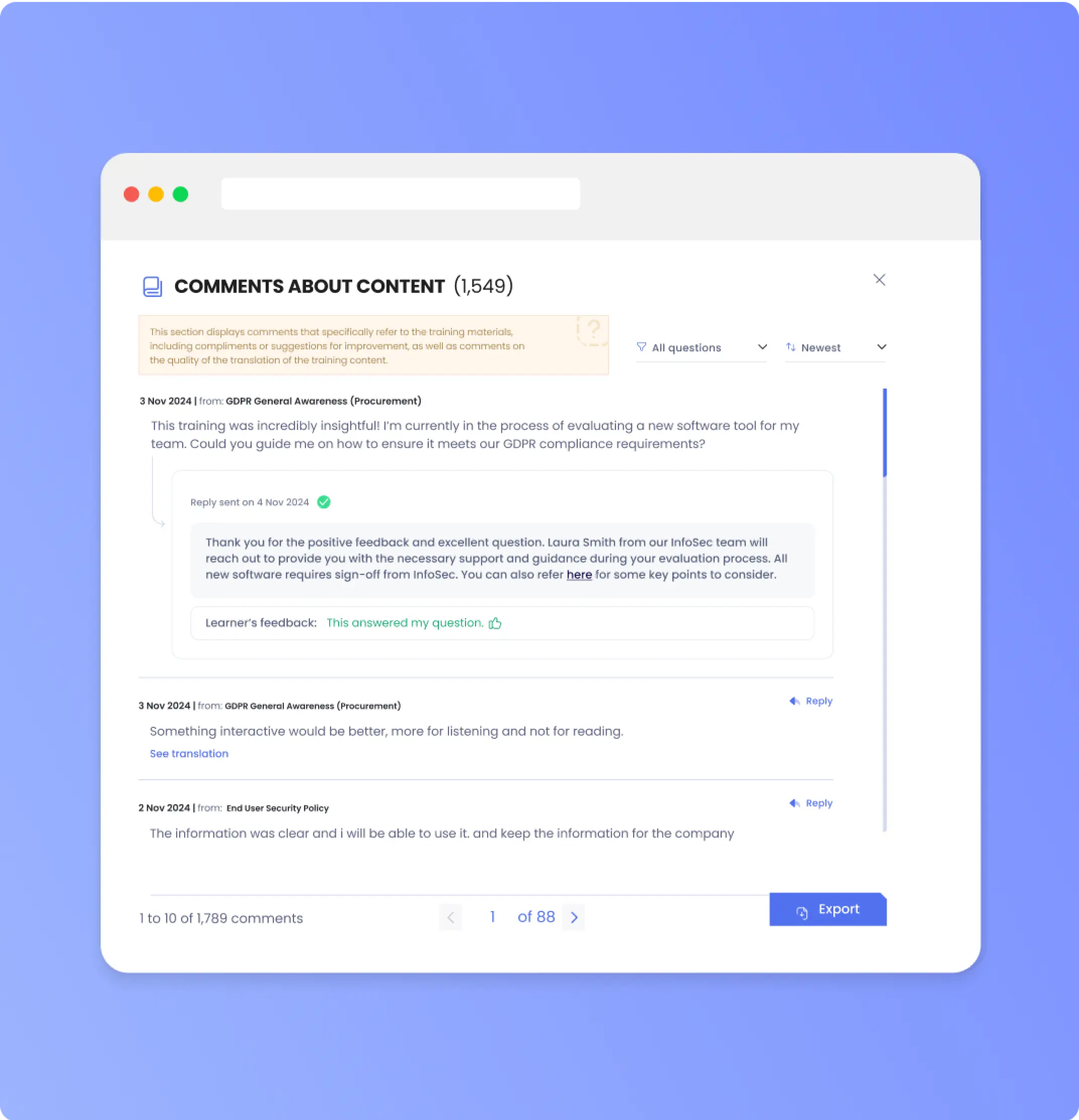
We believe in fundamentally engaging users, learning about them, from them, and reflecting that knowledge back into security policy and the execution of security controls. OutThink's Cybersecurity Human Risk Management platform was built from the ground up on these beliefs, so it should come as no surprise that every user interaction comes with the opportunity for users to provide input. Our platform summarizes multiple clusters of user input using an LLM-based engine, surfaces key insights and then lets the Security team answer users' concerns directly. As we're launching this feature, we decided to take some time to analyze past user input to showcase useful insights for Security teams. Not every one of our 4 million users on the platform provided input, but many have. This paper documents are findings, so far.
People engage when they feel heard...
not talked down to
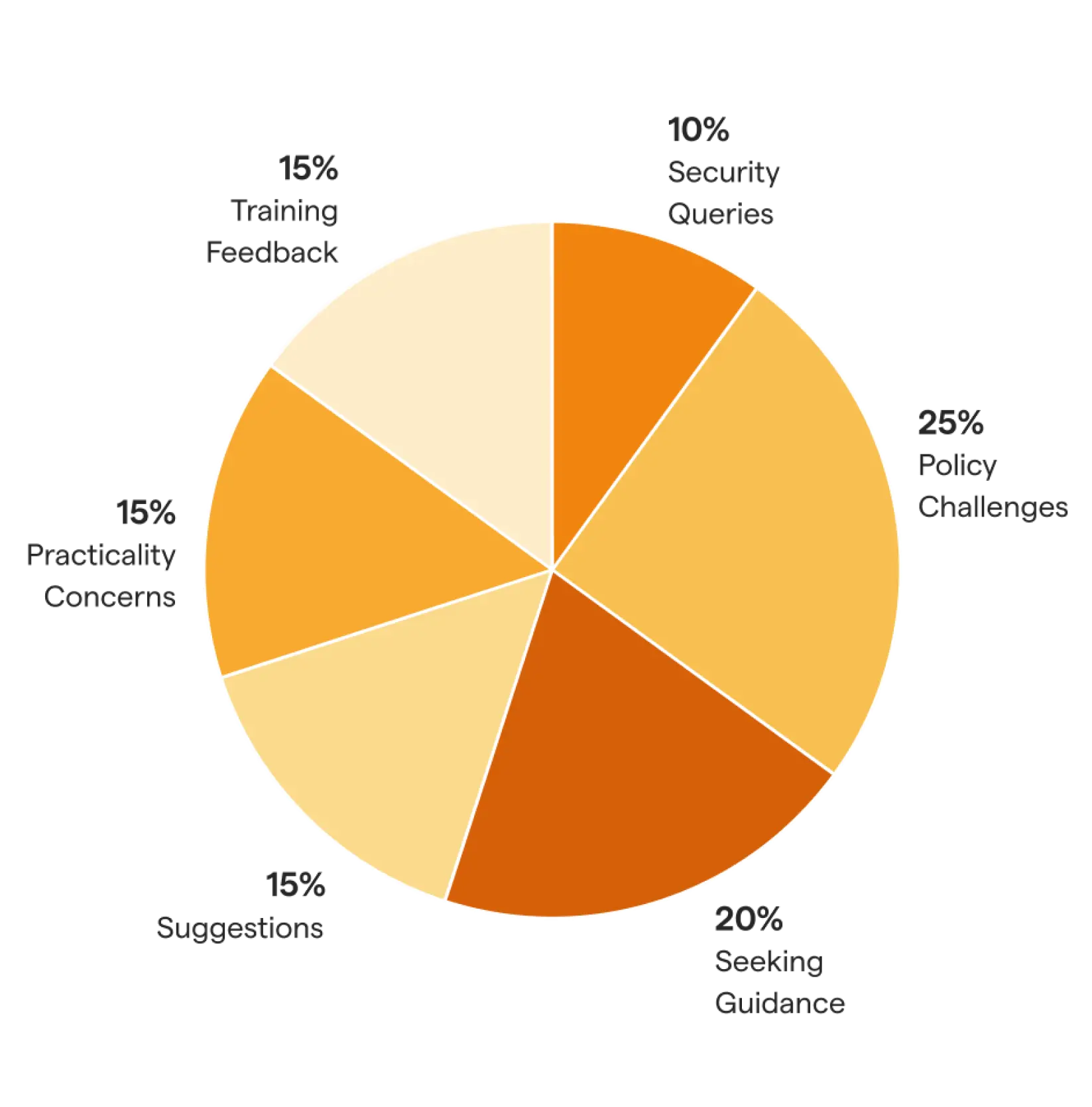
1. Policy and Security Feedback – by Category
The comments in the OutThink's Cybersecurity Human Risk Management platform can be categorized into several main themes. Here is a breakdown with example comments and approximate percentages for each category:
1. a. Policy and Technical Challenges (25%)
Comments regarding difficulties with security policies or specific technical security controls such as password complexity requirements and VPN issues.
“Our ridiculous password complexity requirements are working against our company’s security. Why can’t we use a password manager?”
“I’ve been getting conflicting guidance regarding VPN. Which solution are we supposed to use and how do I install it?”
“The Clickshare conference screen casting system currently used in Canada is a security risk…”
These comments present valuable opportunities to further engage with users and address security elements that get in the way of secure behavior. Just like the common refrain that “there’s no such thing as a bad question”, seeing the same queries from a subset of users points to questions that exist on many people’s minds. The highly engaged among your users can point to specific issues that may be widespread enough to pose significant risks.
Queries from engaged users point to unspoken issues that are widespread.
1. b. Seeking Guidance
Comments seeking clearer explanations on security procedures or policy details, often requesting step-by-step instructions or further elaboration on certain topics.
“Please explain how we can encrypt e-mail attachments containing confidential information.”
“How do I know if my antivirus is up to date? Am I responsible for all updates on my computer?”
Much like the comments shows in section 1 of this document, these queries point to far more widespread questions among employees. In the first example, we can see that even for employees who know they should encrypt data, it’s unclear how to do it. The Security team can either roll out a tool for users with frequent email DLP issues or the overall employee base, with some clear guidance around email attachment encryption mechanics.
1. c. Suggestions (15%)
Suggestions to enhance security processes, bridge knowledge gaps, or make system adjustments, including requests for tools.
“I struggle to transfer large files externally using Sharepoint. Is wetransfer allowed? If not, then why not?”
“It would be great to train a security ‘expert’ in every department who can provide preventive advice to his colleagues.”
Requests for process improvements coming from employees in a certain area of the business can provide impetus and aircover to the Security team in proactively addressing potential vulnerabilities. Knowing the process suggestion came from inside the department might motivate others to accept or even embrace the new process more easily.
Ability to reference business user input adds aircover to new policies.
1. d. Practicality Concerns (15%)
Comments indicating dissatisfaction with security policy or questioning its applicability to daily tasks, including complaints about redundant or overly general information.
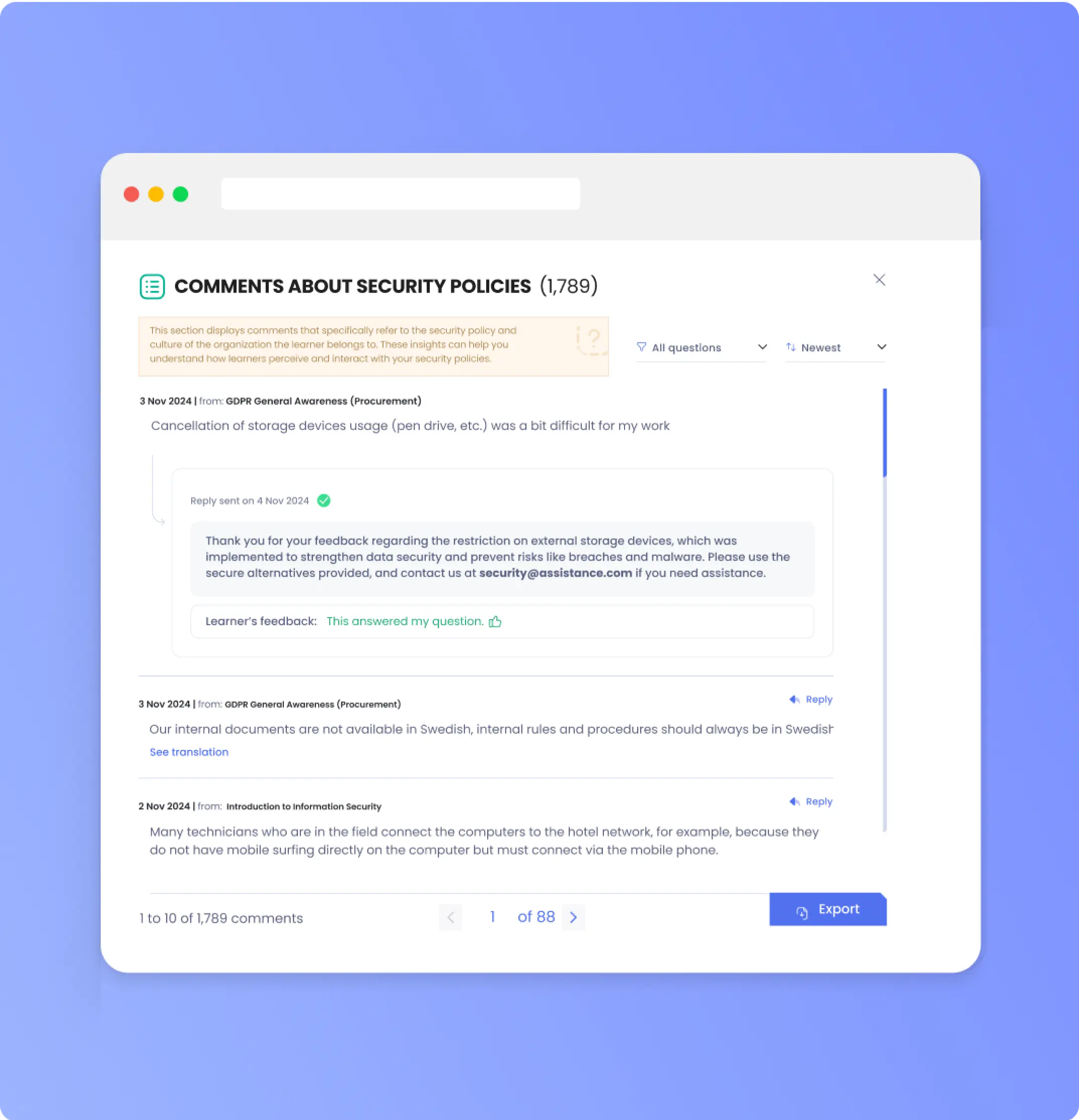
“The biggest difficulty are incoming emails impersonating external suppliers. Is it possible for IT to have a list of our supplier URLs so the verification can happen automatically?”
“It is actually impossible for us to hover over a link in an email and verify if the link looks correct. I think our links are re-written by some security tool?”
It’s good to know when security policy misses the mark for certain users, so you can update your guidance and follow-up with people on the specific issues they have raised. Either the user’s environment can then be updated by IT, or the policies can be changed.
1. e. Training Feedback (15%)
Either positive feedback about the effectiveness or relevance of the training and security policies, or criticism of training format or delivery.
“Good Training. I have not been targeted to social engineering deceiving attacks; it is good to be alert.”
“Lack of option to do a test and skip training is frustrating.”
“I like the cyber challenges – this really made me think!”
1. f. Security Queries (10%)
Inquiries about specific security aspects or potential threats, particularly around phishing, data protection, and network security.
“How risky is it to use my mobile phone as a hotspot for laptop connectivity? Can someone hijack the connection?”
“Could you recommend the right way to secure my home router?“
These are usually questions from highly-engaged users. The added benefit is once they are trained on the topics of concern to them, these engaged users will go around their teams to share the new knowledge as well. A clear force multiplier for the Security team.
User input is often underutilized by security teams. Some teams are able to at least collect feedback on their training, which is useful for the awareness team and certainly better than not knowing how their content is perceived. Getting the full range of input at the detailed policy level is useful to the entire Security team, however, and allows the CISO and other security leaders to see the gaps in their controls. Any security team that’s not paying attention to this kind of user input is flying blind – at least partially.
Legacy SAT with one-way communication leaves a lot of missed opportunity to fundamentally engage and secure the organization. At the very least, Adaptive Security Awareness Training enables two-way communication and an opportunity for users to share their experience with specific security policies. Taken to its logical conclusion, beyond simply informing security policy, this input should lead to specific actions to show users that Security is listening and build trust between the Security team and employees for a more effective, sustainable posture.
Taking it a step further, a careful at user input look shows opportunities for Security to partner with the business to design security into business processes. There is a real 1 + 1 = 3 aspect to this feedback – a silent call from “the business” to the Security team. Input from users can sometimes point to digital process improvements and ways Security can come to the table. This can be incredibly rich and useful beyond closing some prosaic gaps in cybersecurity posture. We discuss some of the more salient examples in the section below.
Engaged providers of input can be turned into a force multiplier.

2. Collective Wisdom – How to be a Business Enabler
Reading through these comments and trying to classify them made us realize there’s an intangible here. Some people really put thought into the inputs they’re sharing, adding color and role-specific context . While many comments simply express opportunities to improve security, or remove certain blanket, block-all, security policies, these insights are useful, but not as meaningful or strategic.
The value of user input can go well beyond the identification of weak security controls. Collectively users know the business. They ARE the business. They know how security policy intersects with their business process. Many CISOs aspire to be business enablers. The user input contains all sorts of little gems from all segments of business, hidden in plain sight. Paying close attention, the smart CISO can learn directly from the front line how to engage better and become a better enabler.
This aspect of user input was harder to quantify by category, but we want to highlight and demonstrate by picking some good examples. We picked some of the better examples that clients found transformative for their business relationships.
Hidden in plain sight, secure business process gems from users can become transformative.
3. Business Obstacles and Opportunities
This user is stating a problem that presents an opportunity for the Security team to partner with the business in a proactive way. If people start heeding security advice, that has impact on the business model of this BU. Perhaps the Security team can help redesign the process for the security-aware digital age.
“I work in a part of the bank where we call customers on outbound campaigns - I'm sorry to see that you recommend customers to hang up and then call back - since that will very soon make me unemployed since my KPIs are to talk to as many customers as possible to have them take a meeting with an adviser.”
Opportunities abound to involve Security stakeholders in process design.
These comments are flagging a potential GDPR issue that could be raised by an audit. It’s an opportunity to get ahead of the auditors and avoid stiff EU penalties.
“Unfortunately, this implementation is not possible in [company]. Data records (customers, for example) cannot be completely deleted. Not even at the customer's request. Deletion is currently only possible for contact details. Can this be adjusted for the future, please?”
“Who do I turn to physically if I believe we have a problem related to the GDPR?”
These comments show an opportunity to get ahead of a transformation project where involvement from the Security team can be a big win.
“The VPN requirements in our policy will likely interfere with implementation of the new customer care system we’re designing as part of CSX-2025, as many CSRs are now working remotely.”
“Our new system will require users to download and send customer account data, containing PII in XLS format over email. Won’t that trigger some policy alerts from the security team?”
4. Physical Problems that Cause Vulnerabilities
These are issues impossible for the Security team to spot without a site visit or audit. By listening to this input, Security can remotely address areas of unnecessary attack surface.
“The printing solution our office was migrated to in May does not wait for authentication before printing the job, and the only working printer is located on another floor, making it highly impractical to never leave printed documents unattended. Fortunately, I rarely if ever need to print sensitive information. But I know others on my floor do use that printer.”
“Our problem in the warehouse is that we are not always staffed enough to handle the flow of customers. Very often I am in the process of handling a customer’s goods but at the same time there is a computer station on the other side of the counter where it becomes vulnerable if I’m occupied with customers.”
5. Suggested ways to better secure business processes
There is an opportunity to make the customer authentication process safer.
“Verify identity of incoming phone calls that need access to sensitive information via an identification token generated in the [company] secured app. Much better than any “personal detail” such as date of birth that anyone could know…”
In this case, the bounds of what is sensitive information are unclear. Very likely a question many other users have too.
“Not all information sent by email is confidential, but there needs to be guidelines as to what is sensitive. Some things are obvious such as confidential financial information. But what about a query as to how a meeting with an external vendor had gone?”
These two comments highlight flaws with password management, visible to an app owner and an end user, but wouldn’t be immediately apparent to the Security team:
“In DB2 we can only use a password which is 8 characters long, otherwise we get an error. I personally had a string of at least 16 characters but due to this stupid DB2-problem I changed to 8 characters which is risky but due to how the system works it seems like we do not have a choice? Why is there no password policy and solution in place for this?”
The Security team can jump ahead and lead the business in designing safe Digital experiences.
“I see an issue with passwords. When I have to log on to my PC I type the same code 3 times. First to open my laptop, then cisco/authenticator and finally my desktop. It often happens from the train. Here it will be somewhat safer to write the code only 1 time, so that fellow passengers can not so easily spot the code.”
6. Directional Input Based on Business Context
These are future-looking comments, based on knowledge of business processes, to point out how the Security team can do its job effectively as business evolves.
“As the Internet of Things (IoT) continues to grow in our field facilities, what are the unique security challenges associated with connected devices, and what measures can be taken to secure them across both consumer and industrial business lines?”
“Consider strategies such as verification questions that allow you to confirm that calls or requests are legitimate. Beware of the names of people or dependencies to verify that callers or emails are legitimate.”
There is a magic confluence in this kind of input between business proximity and an understanding of security issues and requirements. The individuals offering these advanced insights are all but certain to be security champions. They understand how data and the company can become more secure, but they are also in the business lines so they know the details of current processes, the physical environment, and how all those elements are likely to evolve.
Whereas the first section describes all the potential improvements in security posture that could be attained by seeing end-user input, the latter portion shows how users can enable the Security team to connect to the business. To get ahead so Security can keep up with pace of business and the company can keep up with the demands of the evolving cyber marketplace.
In depth knowledge of business processes can only come from business users.
OutThink’s data demonstrates that behaviorally segmented training, paired with actionable insights, is critical to improving cybersecurity engagement and reducing human risk.
By focusing on targeted nudges, adaptive training, and aligning security processes with business objectives, organizations can foster a security-first culture.
Ready to move beyond compliance and tackle human risk management at its core? Explore how OutThink’s CHRM platform can turn insights into strategies, driving measurable improvements in your organization’s security posture.