Table of contents
- Cybersecurity Human Risk Management: Data Sources and Methodology →
- Human Risk Management: Context and Academic Sources →
- The Behavioral Segmentation Grid for Human Risk Management →
- Tracking Engagement in Security Awareness Training →
- Security-Business Alignment: Practical Insights →
- Cybersecurity Risks in Alignment Uncertainty →
- Security Confidence and Alignment Among Learners →
- Behavioral Improvements: Low-Hanging Fruit in Human Risk Management →
- Phishing Simulation Insights: Why We Click →
- Understanding Learner Behavior in Phishing Simulations →
- Reporting Trends in Phishing Simulations: Realism Matters →
- Cybersecurity Human Risk Management: Summary of Key Takeaways →
Data Sources and Collection Methodology
OutThink runs security awareness training as the starting point of its Cybersecurity Human Risk Management platform. The data pulled from the OutThink CHRM platform is stored in a data layer, for use by the content allocation engine and as the kernel of the OutThink Human Risk Quantification engine.
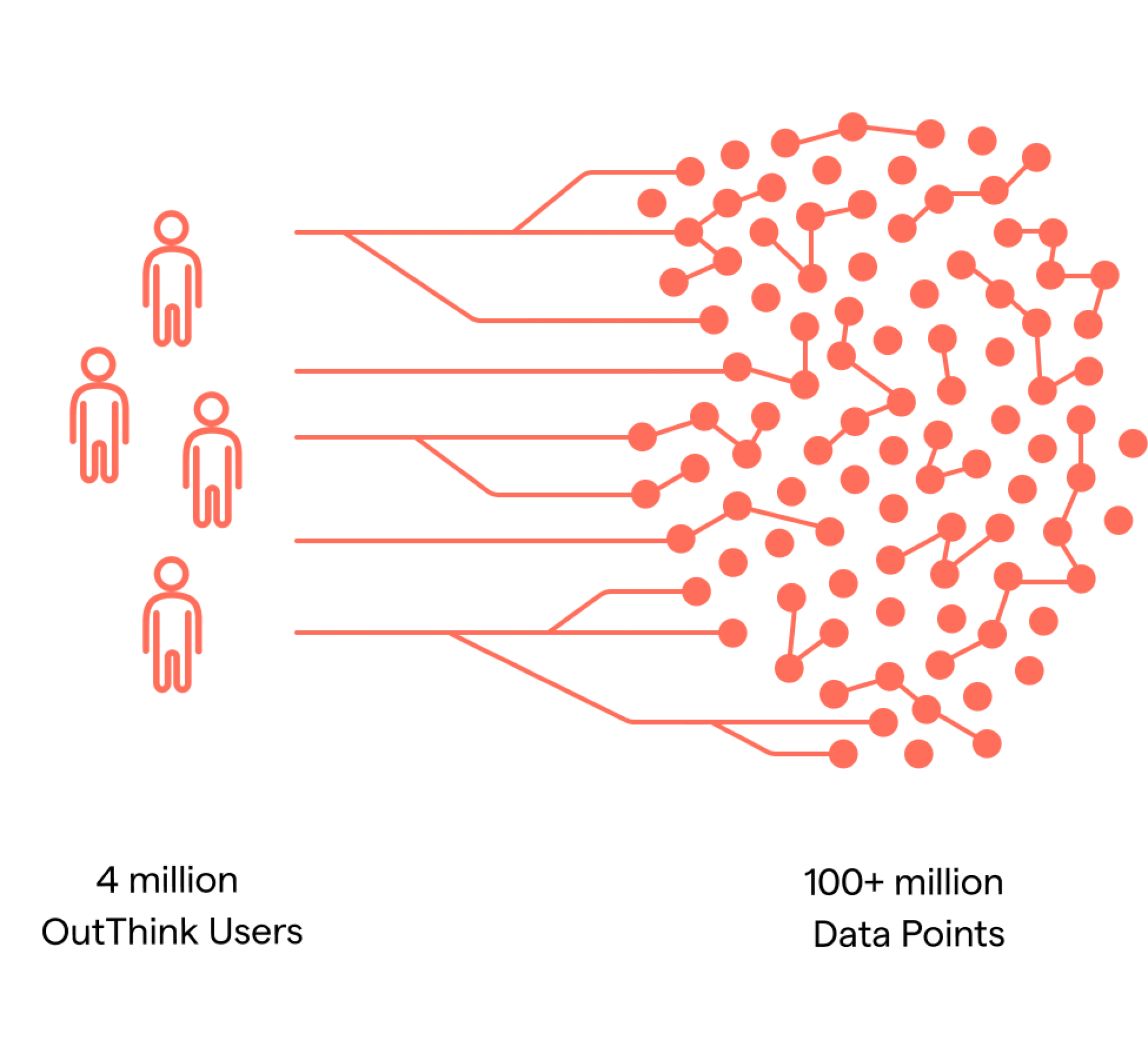
The data points collected in this report come directly out of the OutThink platform repository and are based on user responses inside the awareness training. OutThink was training approximately four million users at the time of the research, constituting about 100 million learning interaction data points.
Distribution of Users
Consumer Services: 17.8%
Financials: 56.7%
Industrials: 25.5%
Human Risk Management: Context and Academic Sources
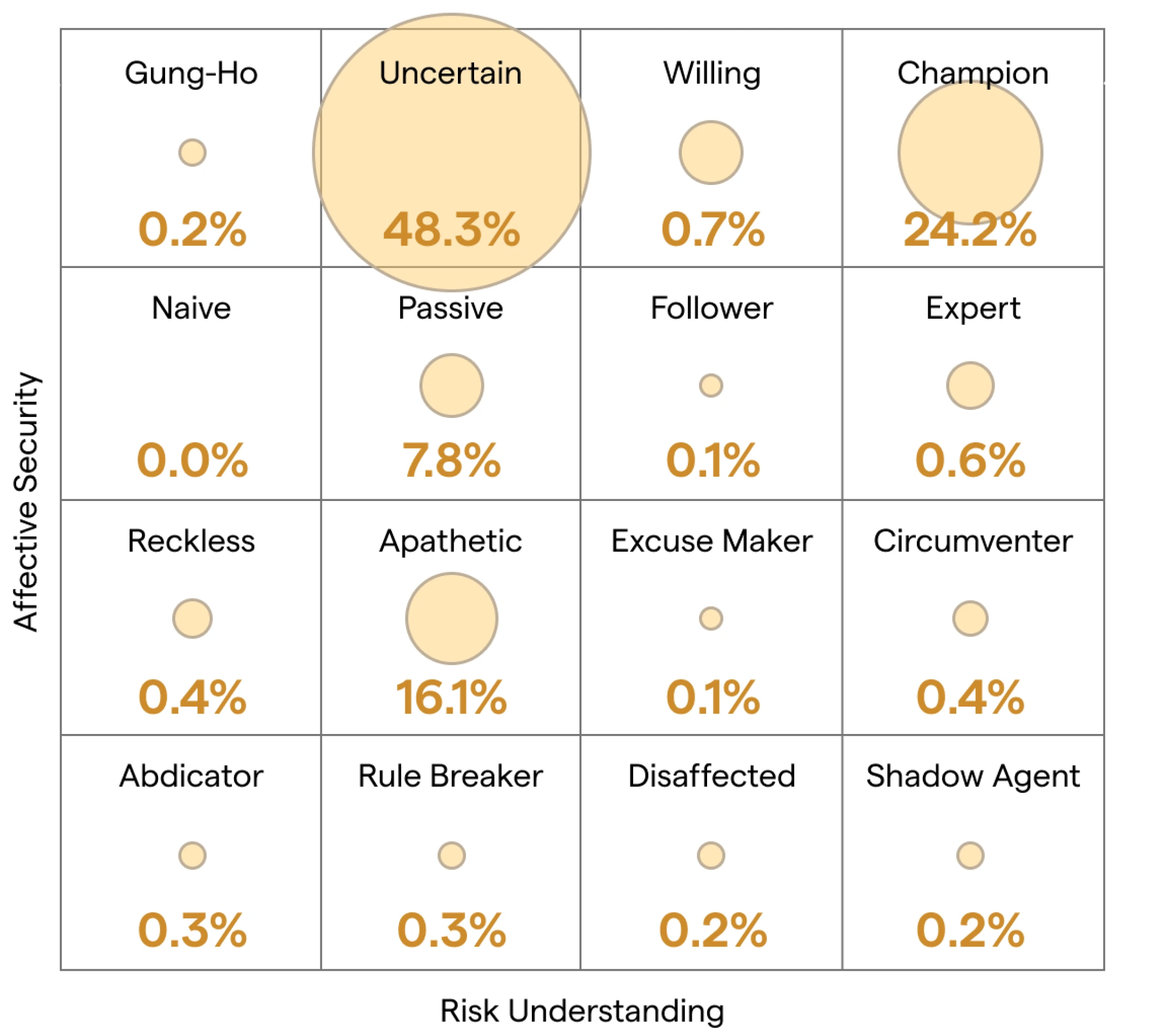
The Behavioral Segmentation Grid (BSG) was developed by a research team at University College London, led by Dr. Angela Sasse. The grid segments individuals along two dimensions:
Affective Security: The extent to which the individual is bought into secure behavior.
Risk Understanding: The level of awareness the individual has regarding security risks.
Using these two axes, the researchers are able to establish 16 zones of behavior that constitute differing segments. Each segment has specific behavioral characteristics informing us about its users’ ability to digest and appreciate security-related content.
Though this research was initially published in 2015, it continues to be cited and utilized extensively, and the behavioral fundamentals it is predicated upon are current in 2024.
For more on the foundational research, see the full study on Human-Centered Security Behaviors.
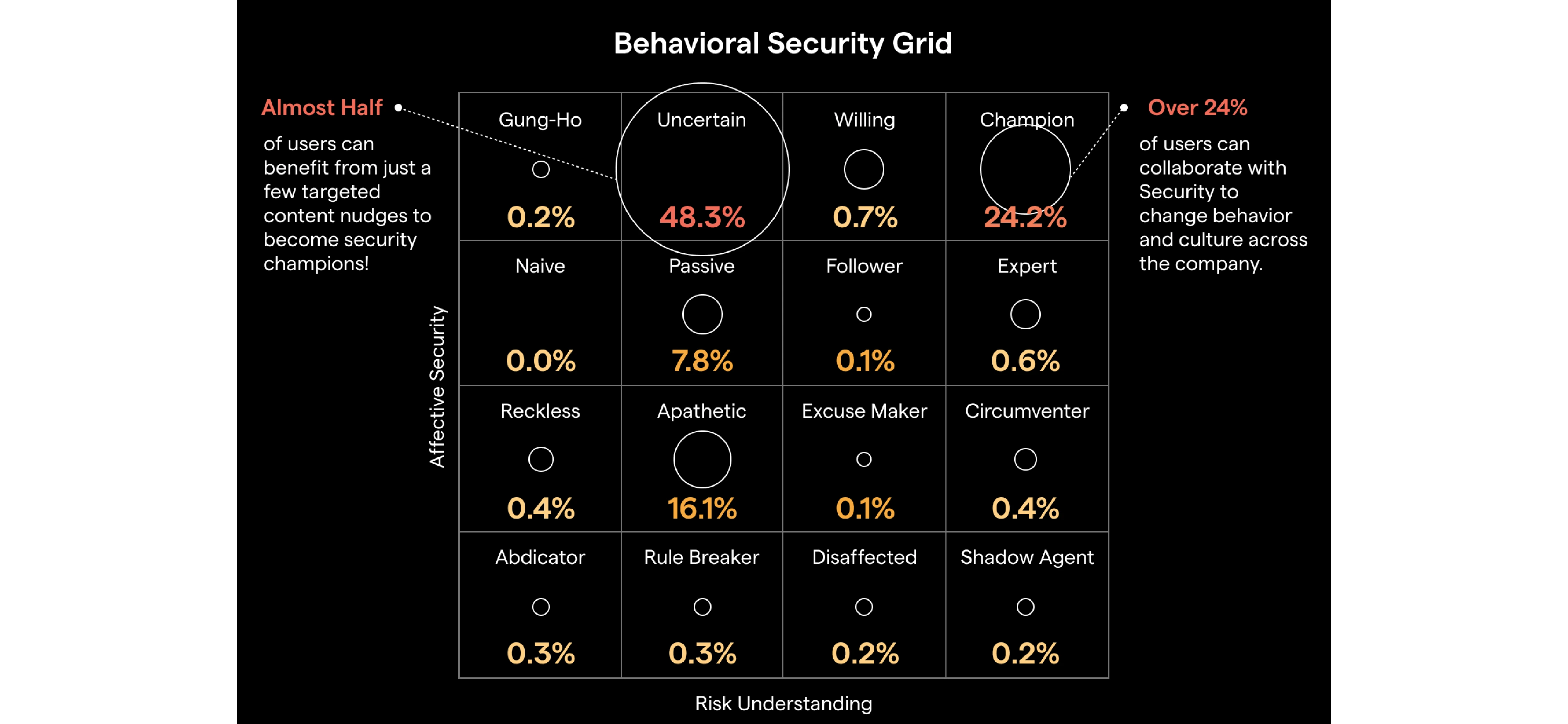
You can't treat all learners the same way!

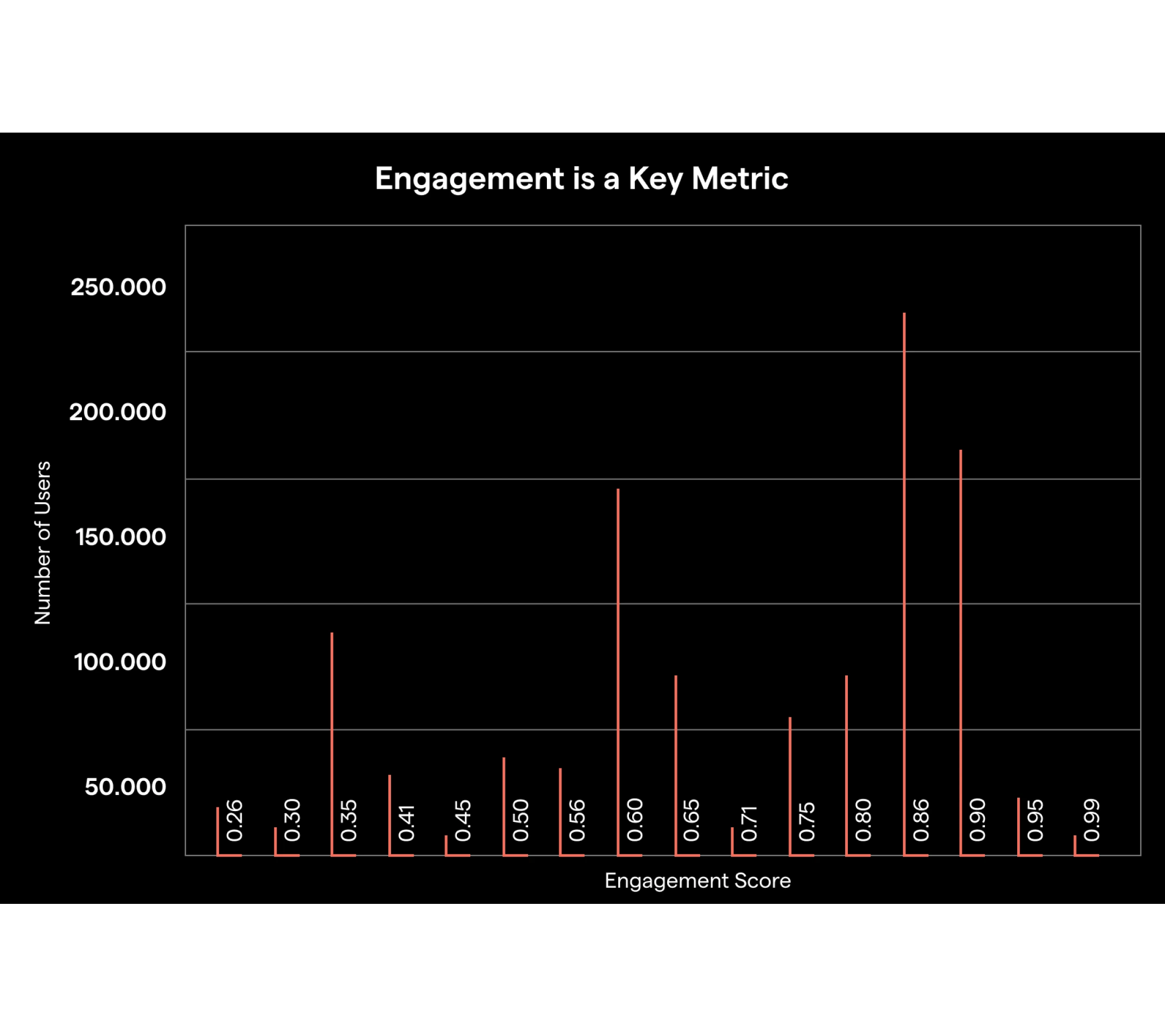
Security Awareness Training: Engagement is a Journey
When users get started with OutThink, they are trained by past security awareness experiences to just click through to the painful end. OutThink is built on engagement at its core. Engagement is a key metric to track for ensuring that actual learning is taking place, not just completions. At the outset, engagement might be low but will increase as adaptive training becomes the norm in the organization.
Supporting Insights:
- Most users fall between 25%-75% engagement, with spikes toward higher engagement levels.
- The key is to measure engagement and look for patterns in the data that show which departments, roles, or content modules underperform, so as to formulate a tailored strategy to bring up all pockets of engagement.
...Paved With Good Intentions
In general, employees want to follow recommended cybersecurity processes and are well-appraised of the danger of potential cybersecurity breaches. A significant minority, however, report that following the processes as described will impact their ability to get work done. This concern is more pronounced for managers, perhaps suggesting that senior employees are working with more sensitive data and processes.
78% of users intend to fully comply with all cybersecurity processes
The remaining 22% fall into categories of non-compliance.
The modules with the lowest intent to comply include:
- PCI DSS & Payment Physical Security
- Cybersecurity in the factory
- Physical Security in the factory
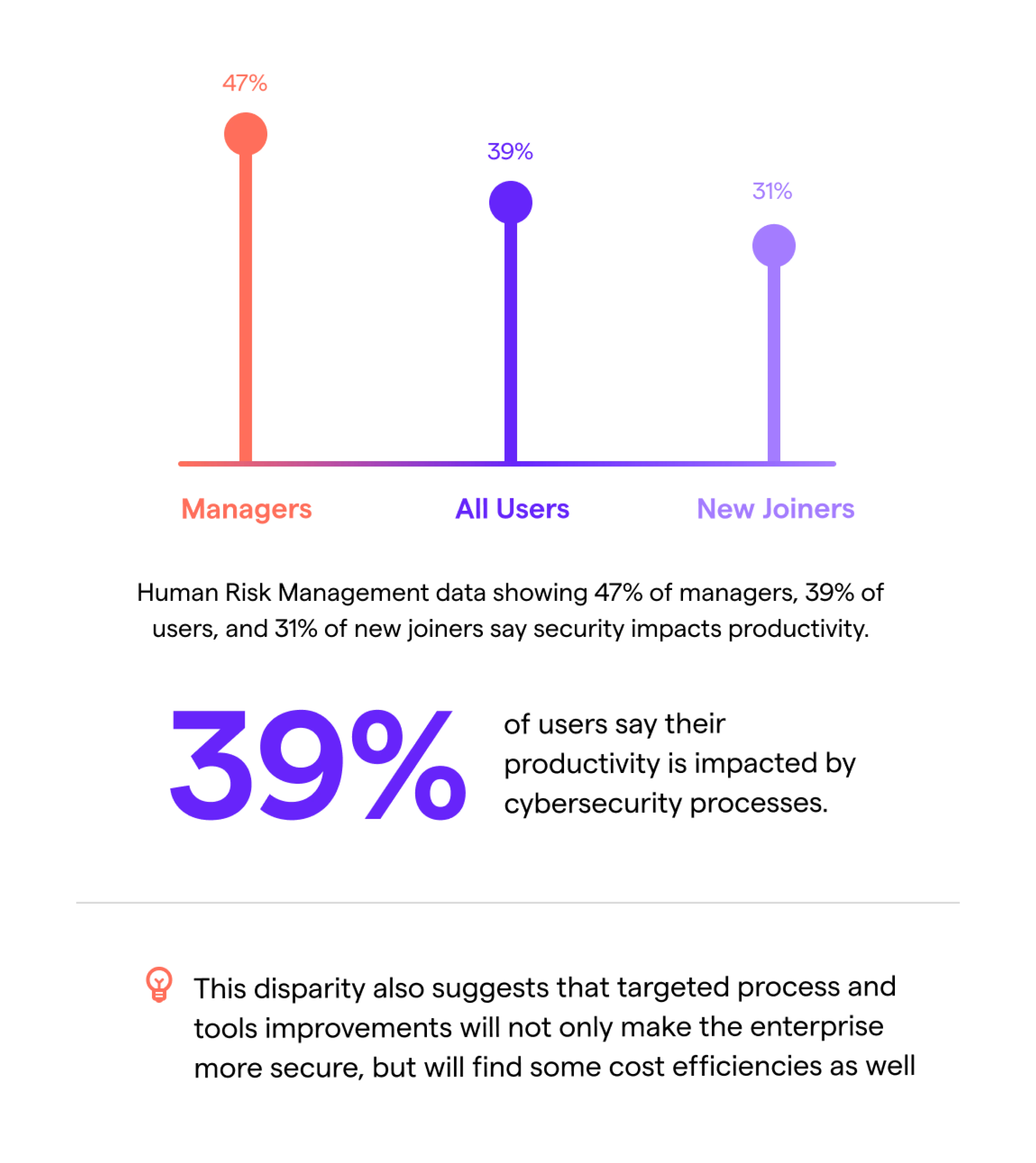
This disparity also suggests that targeted process and tools improvements will not only make the enterprise more secure, but will find some cost efficiencies as well
Unparalleled support
This disparity also suggests that targeted process and tools improvements will not only make the enterprise more secure, but will find some cost efficiencies as well
Build cybersecurity organically into business processes, or it becomes death by a thousand cuts

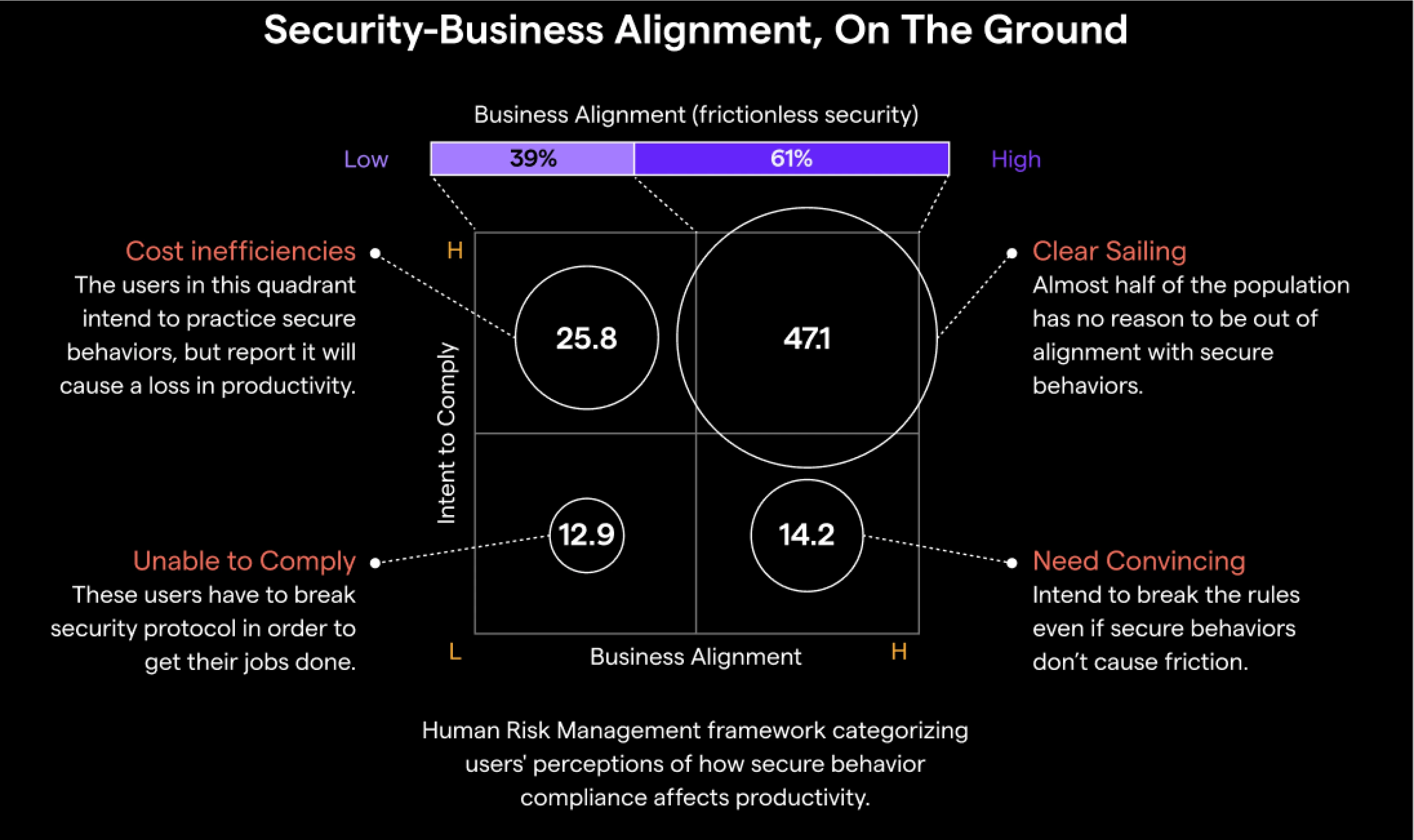
Cybersecurity Risks in Alignment Uncertainty
A detailed breakdown of Business Alignment (frictionless security) versus user metrics like engagement, knowledge, and self-efficacy.
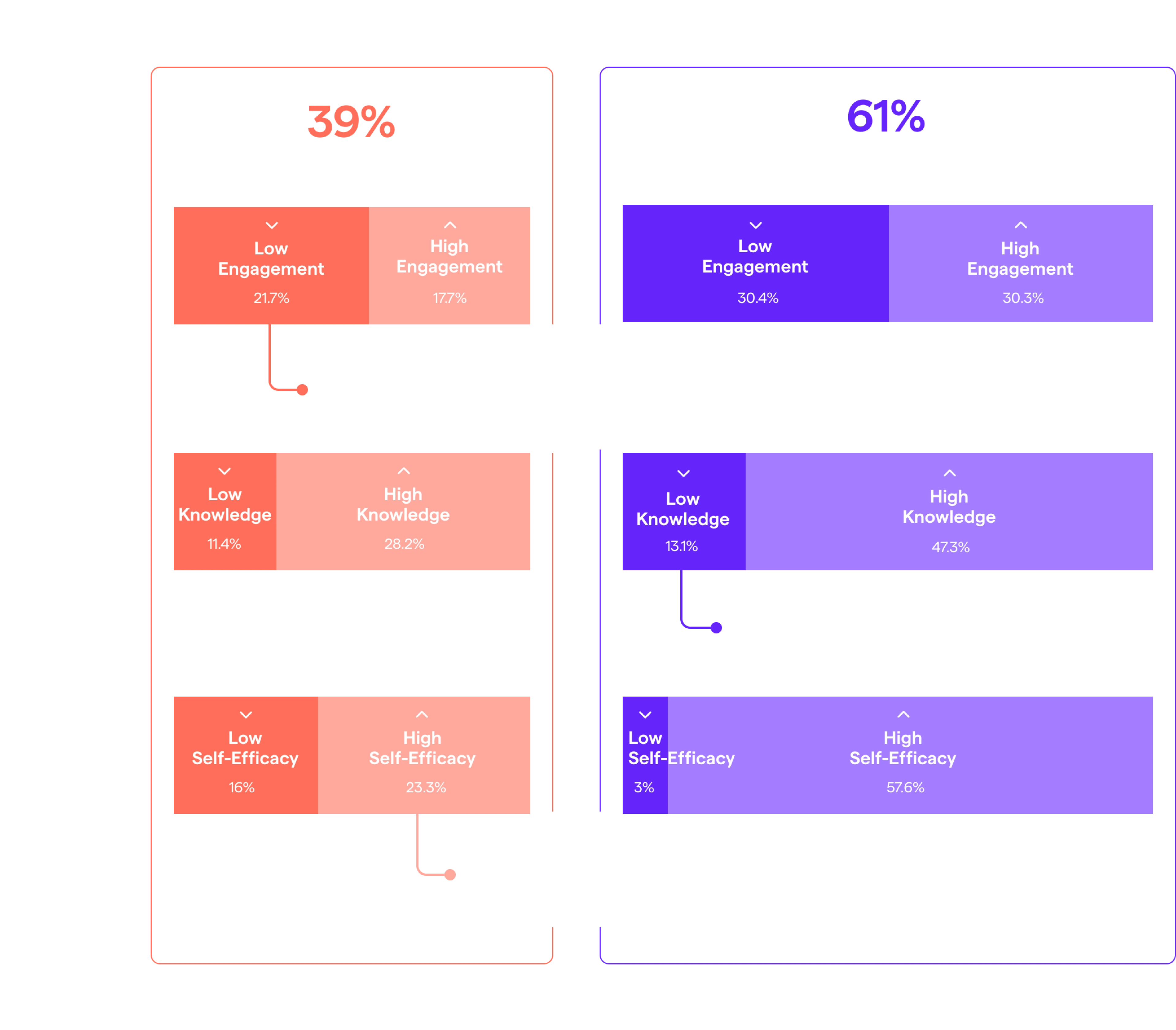
Overall, process friction is reported by Gartner to be the biggest obstacle to effective security. Looking at it through additional lenses helps tease out audiences requiring special treatment.
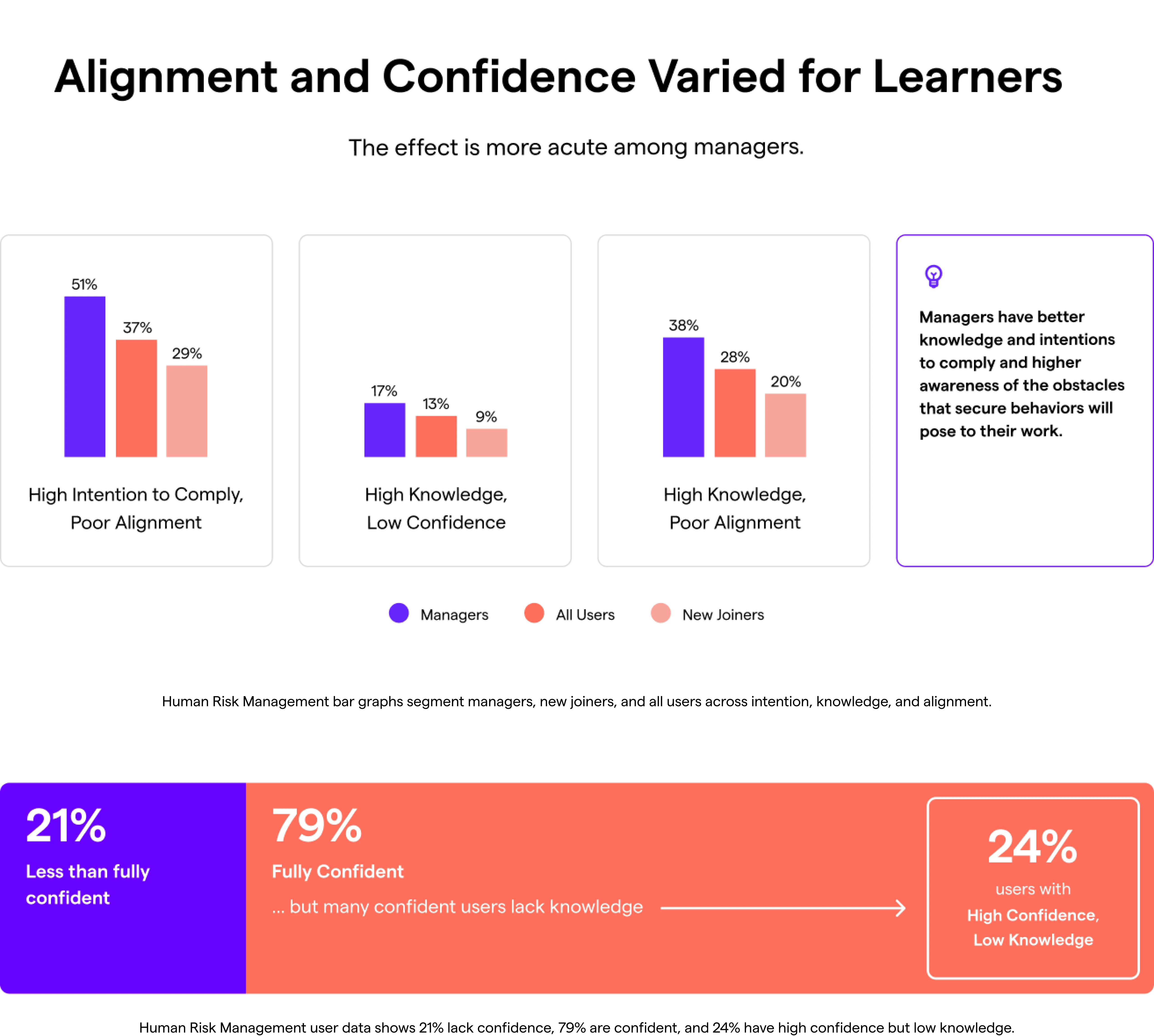
Improvement Opportunities: Low-Hanging Fruit in Human Risk Management
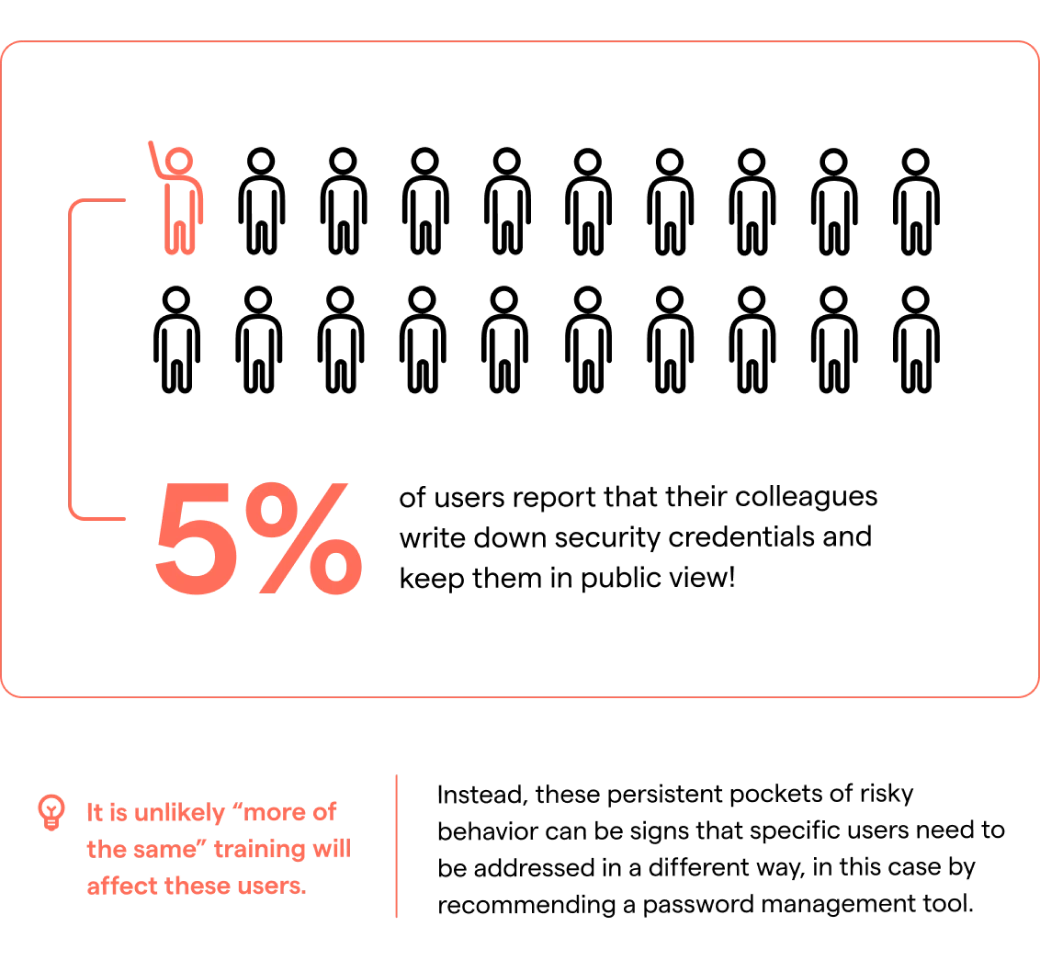
Persistence of Risky Behavior:
It is easy to spend so much time on training and protecting against sophisticated attacks like AI-powered spear phishing that we forget about the persistence of risky behaviors that security professionals have been warning about for decades.
Why We Click on Phishing Simulations
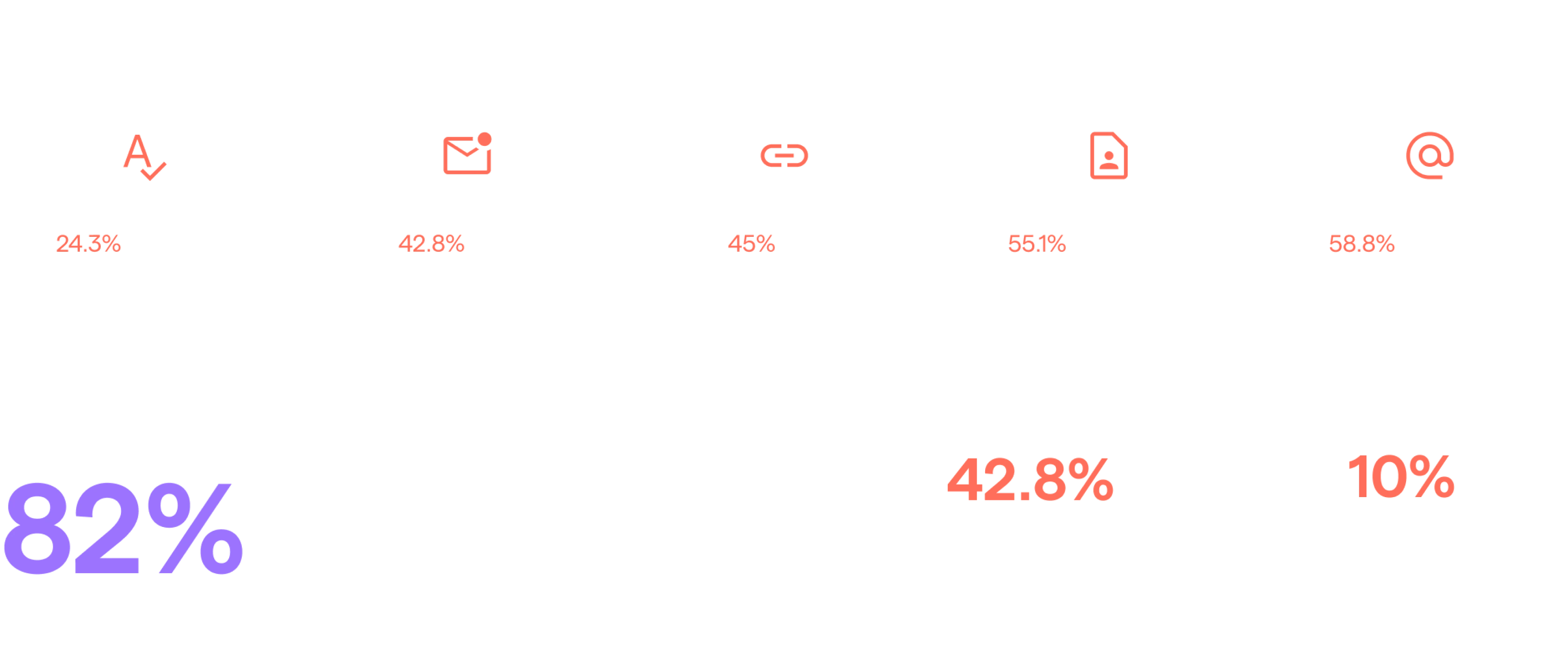
Core Insights:
When offered the chance to explain why they clicked on a phishing simulation, the most common reasons given are related to the identity of the sender.
Despite sender identity being a core element of cybersecurity advice and best practice:
82% of reporting compromised users say they did not make elementary efforts to verify the sender of the message.
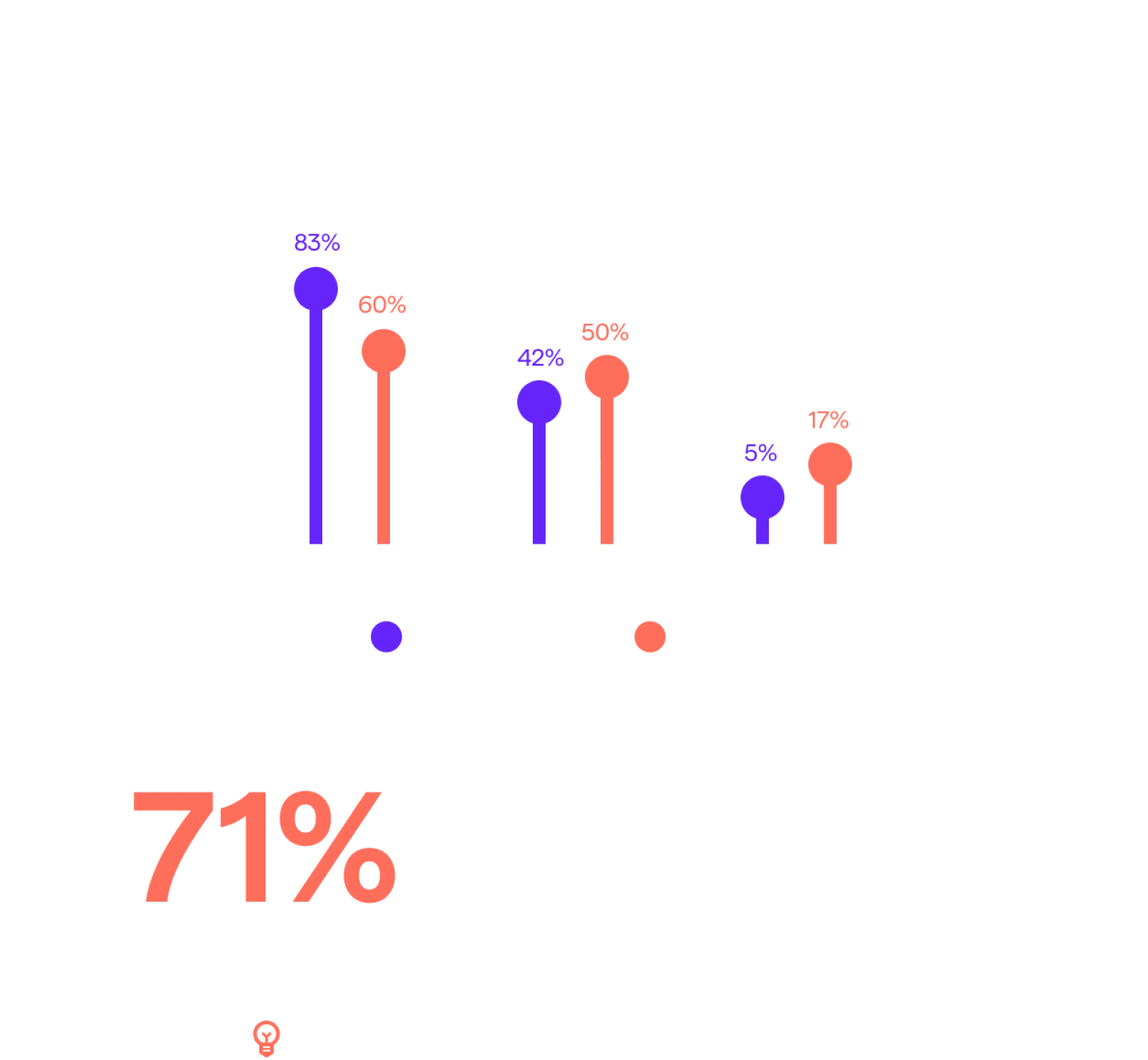
Variations in User Responses to Phishing Simulations
Senior users display markedly different behavior in phishing simulations compared to the average user.
They are more likely to ignore a phishing message and less likely to click a link.
Interestingly, they are no more likely to report a phishing simulation than their average colleague.
For those users who clicked on a phishing simulation and gave a reason why:
Senior users stood out because they were more likely to cite “did not know the sender” as a reason.
This suggests seniority may elicit a sense of responsibility to investigate "cold call"-type messages that a more junior colleague might just ignore.
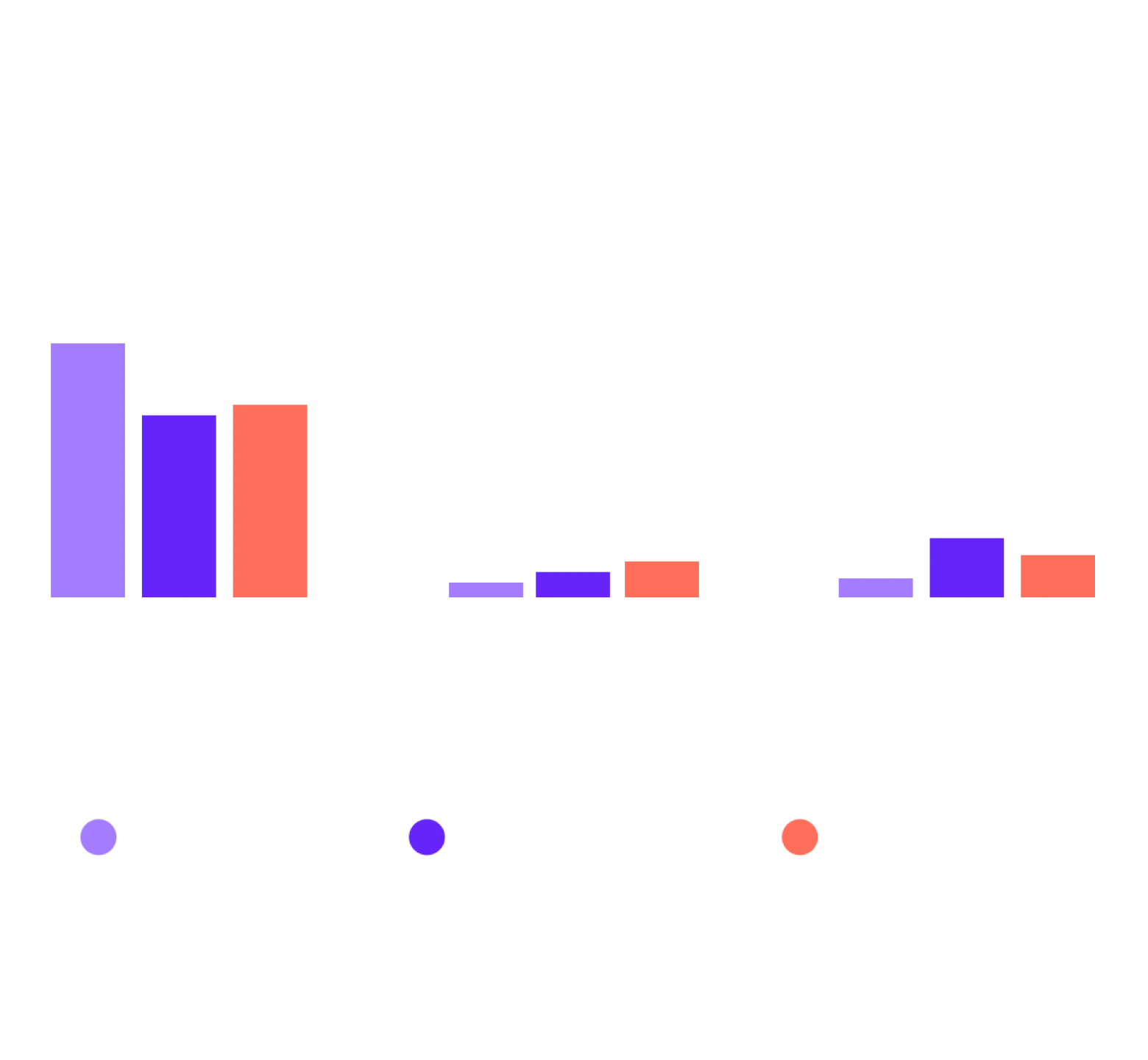
More Realistic Phishing Simulations Are More Often Reported
Users receive phishing messages at a range of difficulty levels:
Easier messages contain obvious mistakes in spelling, grammar, or formatting.
Observations:
- Easy simulations: Most ignored and least clicked.
- Hard simulations: More likely to be reported. This suggests that users who understand phishing risks view these messages as a bigger threat and feel a greater responsibility to report them.
Human Risk Management: Summary of Key Takeaways
Almost 40% of users report security friction in their primary business function.
According to Gartner, one of the primary reasons people break security protocol is that compliance gets in the way of their job.
Almost 80% of users are confident they can fulfill security behaviors.
But 24% of those with high confidence have low knowledge of what constitutes secure behavior.
OutThink’s data demonstrates that behaviorally segmented training, paired with actionable insights, is critical to improving cybersecurity engagement and reducing human risk.
By focusing on targeted nudges, adaptive training, and aligning security processes with business objectives, organizations can foster a security-first culture.
Ready to move beyond compliance and tackle human risk management at its core? Explore how OutThink’s CHRM platform can turn insights into strategies, driving measurable improvements in your organization’s security posture.