Table of contents
Introduction
Chief Information Security Officers (CISOs) have long grappled with the daunting task of safeguarding their organizations while balancing risk and reward. They must ensure that policies, processes, and technologies not only protect against threats but also empower employees to drive business goals, achieve revenue targets, and foster annual net profit growth.
A Gartner poll conducted in the summer of 20241 revealed a startling statistic: only 14% of security leaders feel confident in their ability to secure data while supporting business objectives. This leaves many organizations vulnerable to cyber threats, regulatory penalties, and operational inefficiencies, ultimately jeopardizing their competitive edge and stakeholder trust.
It is evident that CISOs and security teams who master this delicate balance – implementing robust policies to mitigate risks within acceptable tolerances and engaging employees in understanding risk, adhering to these policies and encouraging collaboration with security – emerge as the most efficient and profitable organizations.
This report aims to quantify the impact of achieving such a balance and explores how security teams can best equip themselves to engage employees and minimize human risks through training and technology, all while sustaining year-on-year revenue growth. Leveraging OutThink data, we present key approaches and recommendations for CISOs and security teams to replicate these successful strategies within their own organizations.
Key findings
- 68% of security breaches start with the human factor.
- Enterprise organizations where employees understand security policy and collaborate with the security team are 32% more profitable than enterprises where they don’t.
- 27% of employees with privileged access admit to not intending to fully comply with security policy. This drops to just 6% in the most collaborative enterprise organizations.
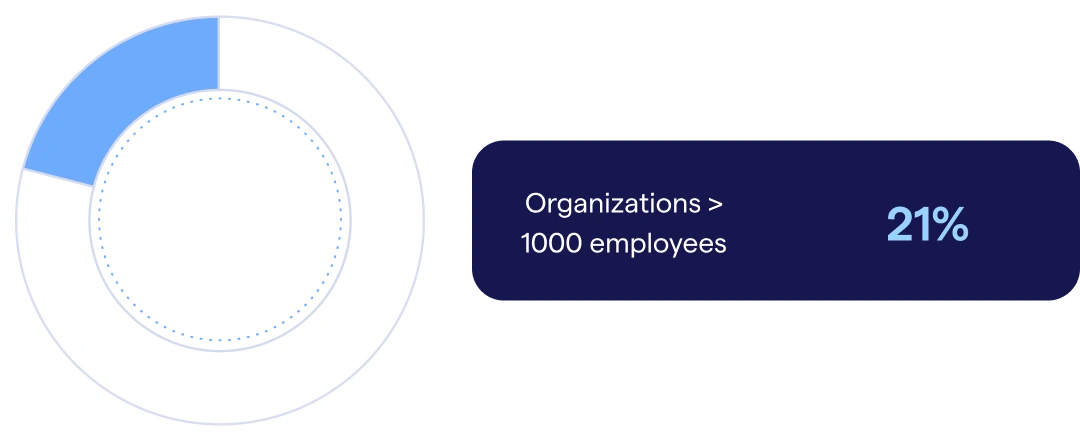
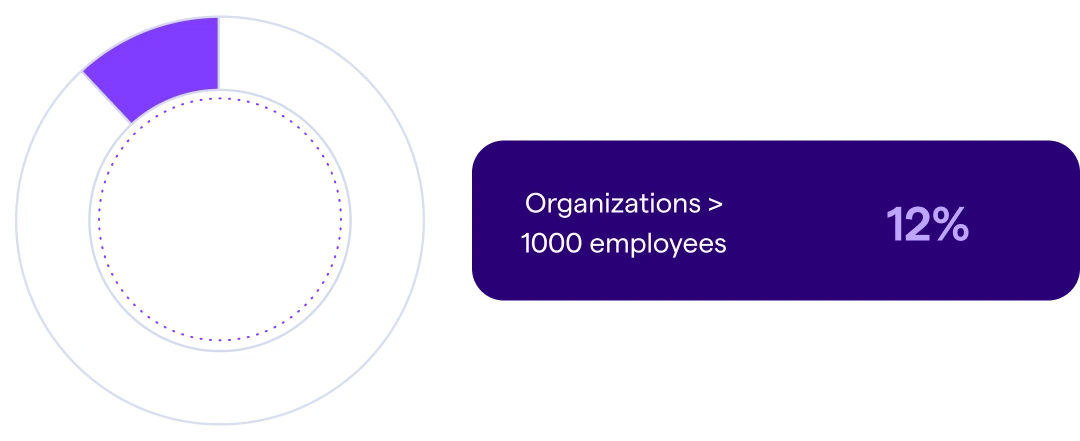
- 21% of employees are cyber champions in the most security engaged enterprise organizations, with only 12% displaying those characteristics in less engaged organizations.
- There is a strong correlation between the high engagement of line managers with cybersecurity and that of their teams, with correlation coefficient of 0.78.
Why is employee understanding of cybersecurity risk and collaboration with security teams important for increased business profitability?
Human risk remains one of the most formidable challenges for CISOs and their security teams in their quest to secure organizations. The 2024 Verizon DBIR Report again highlighted that the human factor was the leading cause of breaches, accounting for 68% of incidents.
Moreover, a Gartner survey revealed that 69% of employees admitted to knowingly bypassing their organization’s cybersecurity guidance in the previous 12 months, with 74% saying they would be willing to do so if it helped them or their team achieve a business objective.
Clearly, better engagement with employees and enhancing their risk perception are crucial. By fostering an understanding of the importance of cybersecurity policies and collaborating to ensure these policies still enable business goals to be met, organizations can significantly boost their cyber resilience while maximizing profitability.
- The policy is genuinely over-restrictive and preventing them from meeting their objectives, increasing the chance they will bypass it.
- The policy is appropriate, but the employee doesn’t fully appreciate the balance of risk versus reward and is overly critical of the safeguards that are in place.
To address the former and improve the balance between data security and business support, Gartner recommend CISOs and security leaders should try to ease governance-related friction by co-creating data security policies and standards with input and feedback from end users across the business1. This advice stems from their summer 2024 poll of security leaders, which revealed that only 14% feel confident in securing their data while supporting business goals. Consequently, many organizations face increased vulnerability to cyber threats, regulatory penalties and operational inefficiencies, ultimately risking their competitive edge and stakeholder trust.
For the latter, effectively engaging employees to increase their understanding of the importance and necessity of security policy is crucial. Consider airport security as an example. While it would be much faster if passengers could head straight to their departure gates on arrival at an airport without any security checks, this approach is never advocated. Passengers inherently understand the risks and consequences of bypassing identity checks and baggage searches. They accept this necessary friction and plan accordingly, allowing extra time to get to departure gates so as to ensure their safe arrival at their final destination.
The goal should be the same for cybersecurity in businesses – engaging employees so they understand how their role and behaviors contribute to the cyber resilience of their organization, and the relationship between compliance with policies and the security of the organization despite the frictions they might cause.
In the event of a breach, the average organization loses $1.47m in business due to the resulting reputational damage, along with an average of $3.41m in post-breach costs, covering detection and escalation, setting up credit monitoring services for customers and providing the necessary notifications4. Additionally, 70% of businesses suffer significant disruption in the event of a breach, with 75% organizations taking more than 100 days to recover, and 35% more than 150 days.
The reputational impact also has long-term effects – 33% of consumers report having stopped doing business with a company whose customer information was compromised5. Sixty percent of consumers would stop shopping with a retailer post- breach, and 83% would consider abandoning finance apps if their data was compromised6. Furthermore, 47% would blame the financial institution rather than the company responsible for developing the app, underscoring the importance of why organizations should scrutinize the cybersecurity of their supply chain.
Enterprise organizations are increasingly incorporating cybersecurity risk assessments as part of their new vendor risk evaluations. Many industries such as finance and healthcare require vendors to adhere to security frameworks like ISO 27001, SOC 2, or NIST, all of which include assessment of human risk factors such as security awareness training and control policies. For businesses aiming to sell to enterprise organizations (deals that typically represent higher revenues), being able to demonstrate compliance is crucial to driving bigger profit growth.
Robust cybersecurity policies empower organizations to drive innovation. By mitigating risks upfront, secure enterprises can focus on agility and innovation, ensuring that a resilient cybersecurity framework supports their digital transformation initiatives7. This approach allows businesses to remain competitive in fast-evolving markets. In fact, 61% of CEOs and senior executives in technology companies view security as a strategic function and a potential competitive advantage8.
Impact of collaboration on profitability – the results:
The analysis in this report was, unless otherwise stated, produced using aggregated OutThink data, collected across 1.05m unique employee campaign results generated by 417,000 employees. The data was collected from January 2020 to December 2024.
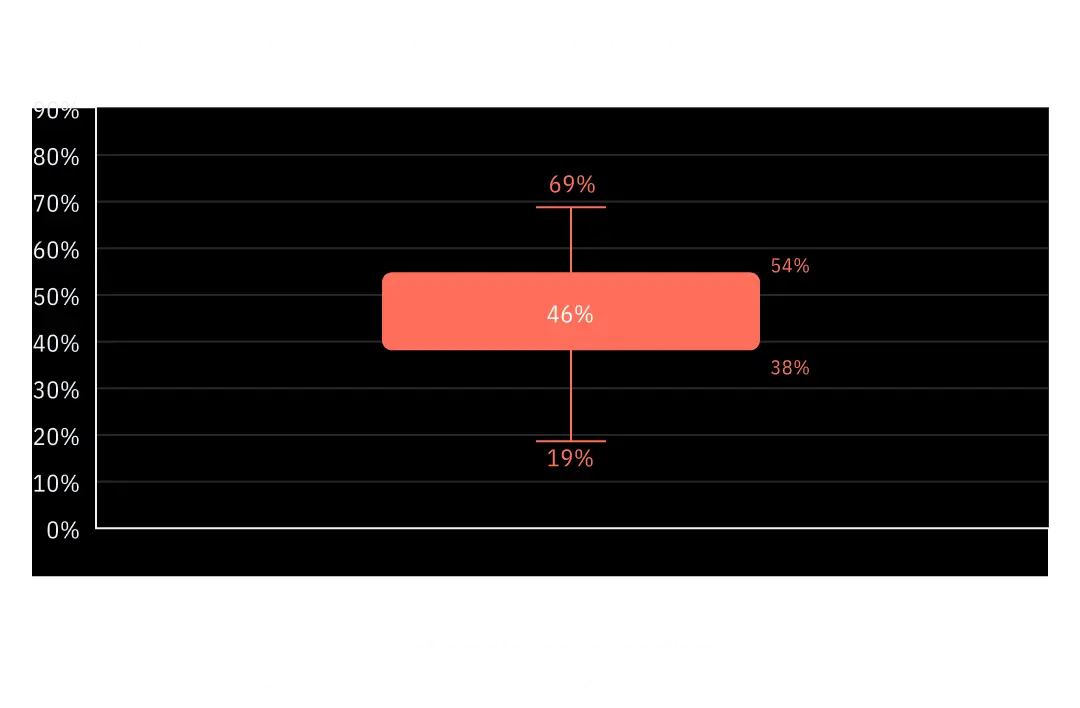
OutThink data supports Gartner’s recommendations that security teams should develop policies and standards with input and feedback from end users to ensure the security of data whilst supporting business goals. During the security awareness training process, OutThink gathers employee insights on their organization’s security policies, and asks employees to rate the impact these policies have on their productivity in their role. On average, across all OutThink customers, 46% of an organization’s employees report some degree of friction caused by cyber policies affecting their ability to fulfil their business roles.
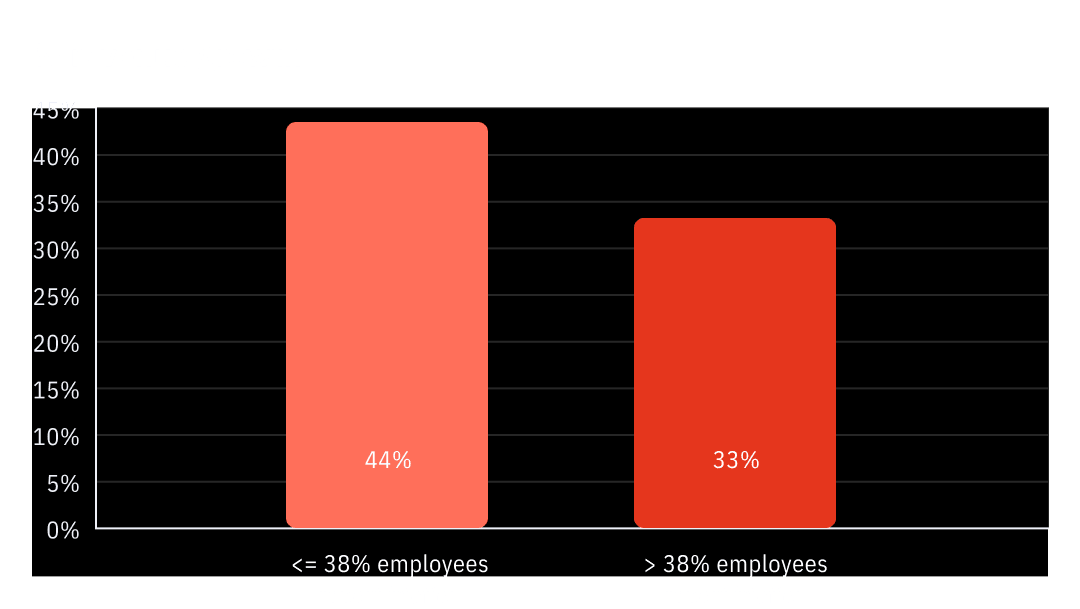
By combining that data with publicly available financial performance information, it was observed that organizations where 38% of fewer employees (i.e. the lower quartile) report friction between business productivity and security policy saw annual profits increase by an average of 44% between 2020 and 2024. In contrast, organizations with more than 38% of employees reporting friction experienced an average annual profit increase of only 33% during the same period, representing a more than 10% reduction in growth over the 5-year span.
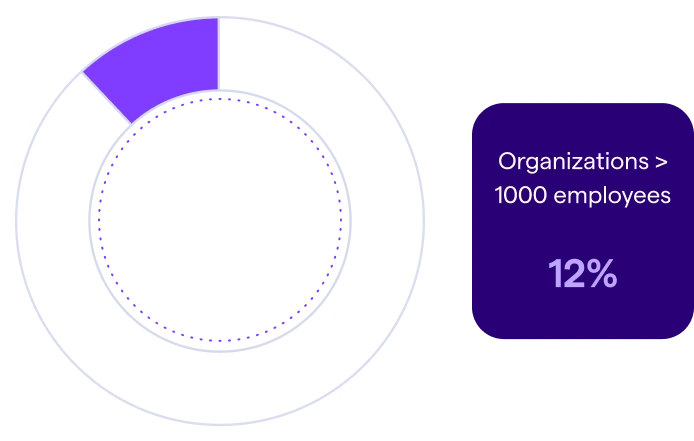
The difference in growth became even more pronounced for organizations with more than 1000 employees (“enterprise”). Those with fewer employees reporting friction saw an average 67% profit increase between 2020 and 2024, compared to only a 35% profit increase for those with higher levels of reported friction.
Figure 2: Average revenue growth 2020-24 for OutThink Customers
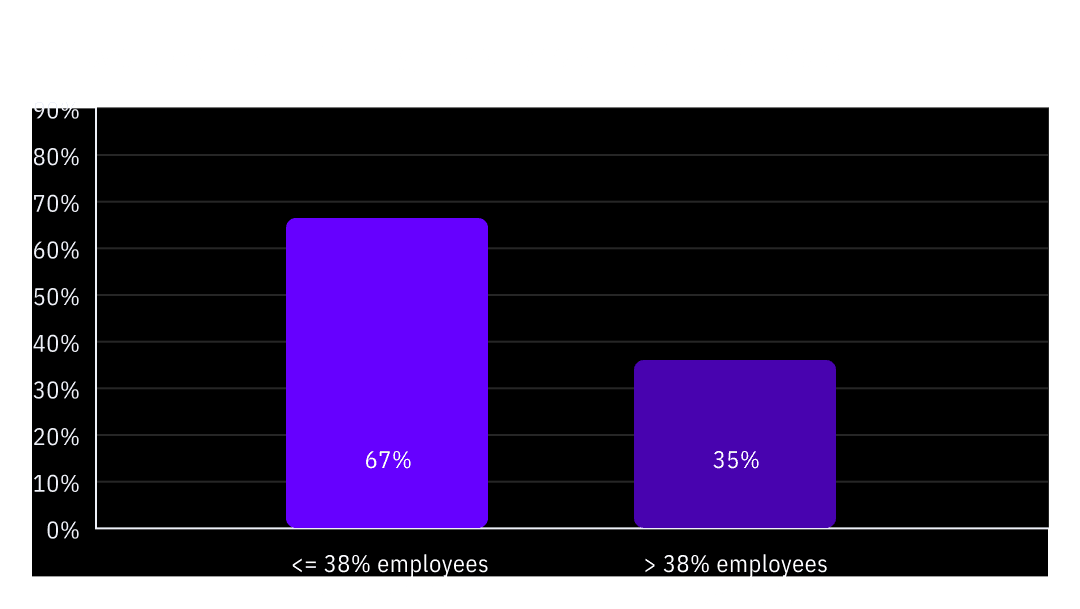
This data supports the hypothesis that the less friction introduced by security policy, or the less perceived friction, the more efficient and ultimately profitable the organization can become.
In the previous section, we discussed how friction in the security process can impact profit. According to a Gartner survey, the majority of employees admit to knowingly bypassing their organization’s cybersecurity guidance, with 74% willing to do so if it helps them or their team achieve a business objective3. This behavior introduces a heightened risk of breaches, which can significantly eat into profits when responding to incidents.
As part of its training campaigns, OutThink asks employees whether they intend to comply with their organization’s policies. By combining this data with information on which employees hold privileged access rights to perform their role, we can identify those who could pose the highest risk in the event of compromise due to their access levels and are openly communicating their intention not to follow policy.
Looking across all customer organizations, on average 27% of those users who declare holding privilege access also state that they won’t fully comply with the policies included in their training courses. In the most extreme case, 83% of those with privilege don’t intend to fully comply. These results pose significant risk for their organizations and OutThink recommends that these customers take steps to understand this data further, such as drilling down to determine if certain roles or business units are most impacted. Additionally, they should engage with the leaders of the relevant teams to discover and collaborate as to why policies are causing so much friction and determine if these policies could be tweaked or how the security team can better communicate the potential impacts of non-compliance to the given audiences.
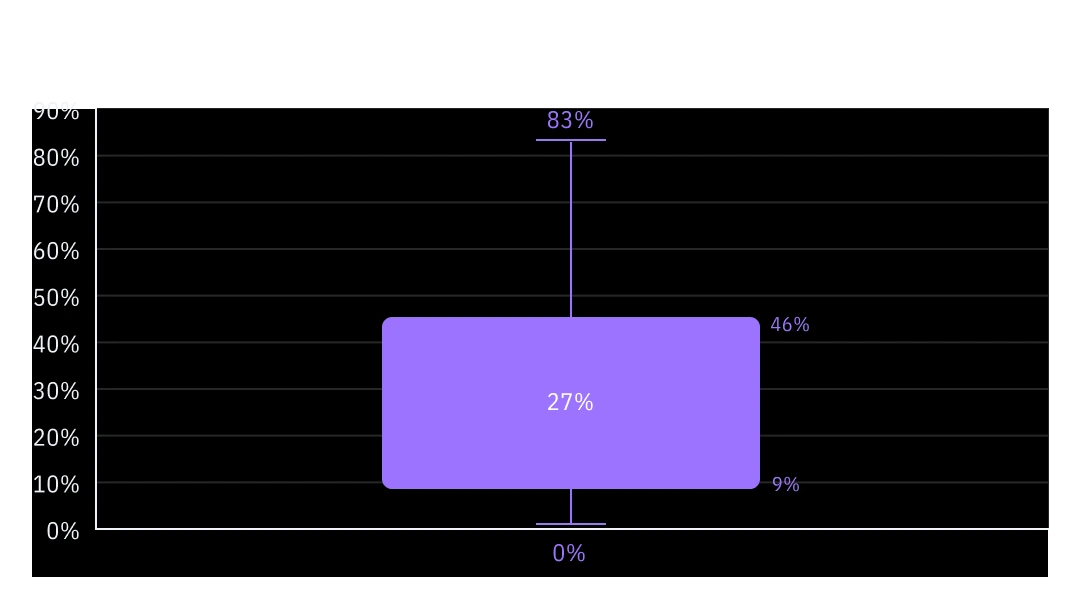
Figure 3: Percentage of users with privileged access who communicated that they don't intend to fully comply with security policy
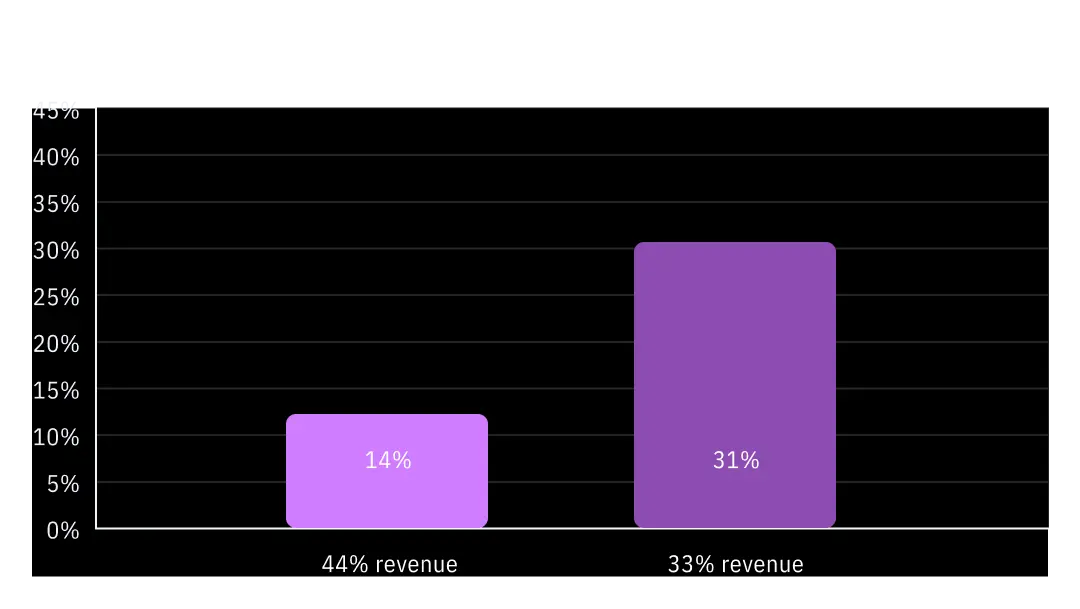
When combining the results with the financial performance of the organizations over the 5-year period, it again corroborates the result that compliance and healthy cyber culture support stronger business performance.
Figure 4: % of privileged users who don't intend to fully comply with security policy
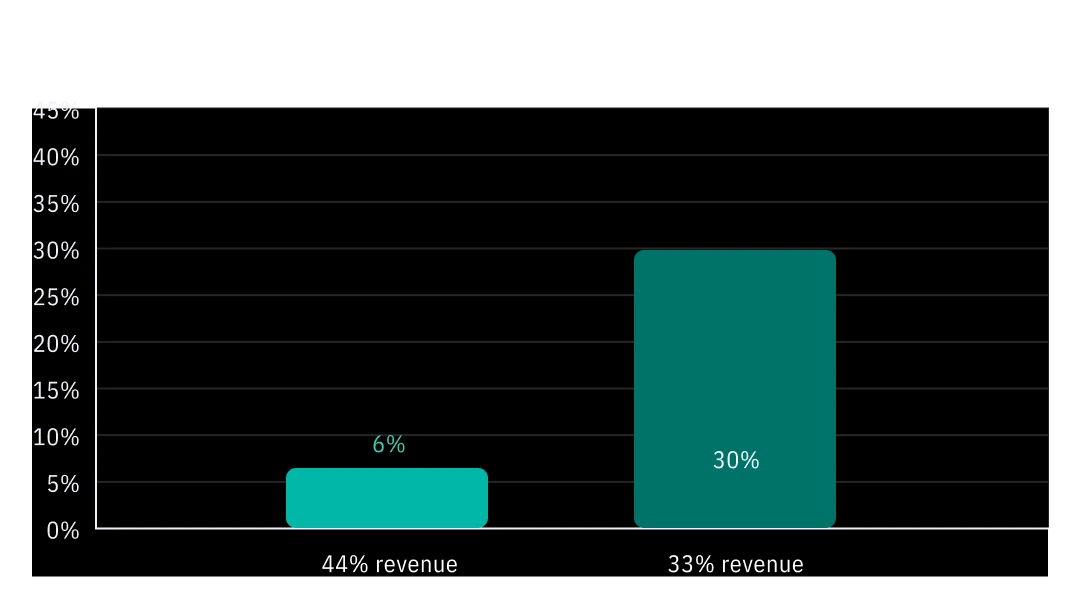
The best opportunity to reduce friction, or perceived friction, and associated risks of non-compliance or misunderstanding among employees is through continuous engagement. OutThink measures the level of engagement employees demonstrate when undertaking their security awareness training: do they spend enough time consuming content suggesting they are reading it rather than just clicking through? Do employees offer feedback or ask questions when given the opportunity? How quickly do employees undertake their training when a campaign is launched – do they complete it on the first day or wait until the deadline is approaching?
Within this population of the most engaged employees, OutThink define “security champions” to be employees who combine high levels of motivation regarding security with a good understanding of both the risks they are likely to face, and the implications of those risks. This makes them able to remain secure even in situations where no explicit policy exists, as well as carrying over good habits into their personal lives. In addition, they will promote a positive culture around them, influencing others. These are the employees who will be instrumental in supporting security teams in developing policies whilst enabling business goals and growth. When comparing customers, it was observed that significantly more security champions exist in organizations with higher-than-average levels of engagement compared with lower than average.
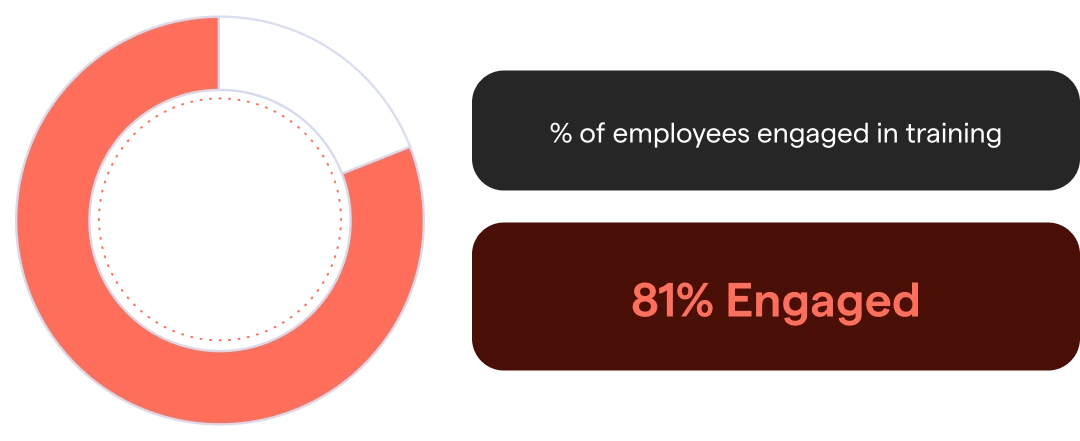
Figure 5: On average, the proportion of employees highly engaged during their security awareness training campaigns
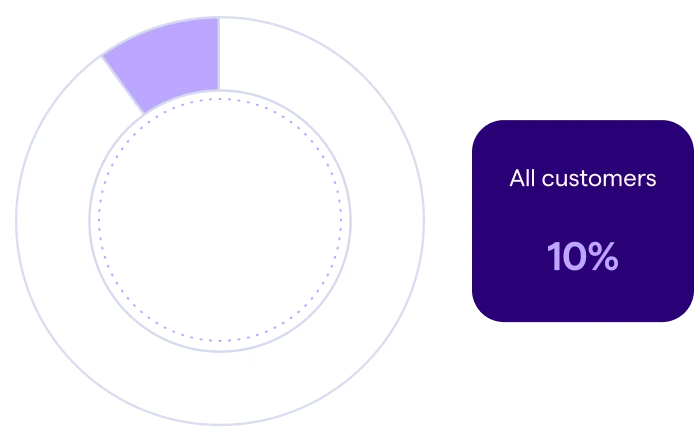
Figure 6: Proportion of employees who are security champions in organizations with higher-than-average engagement
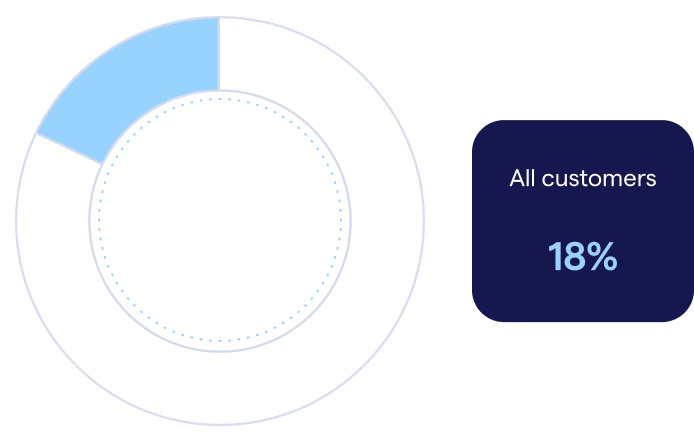
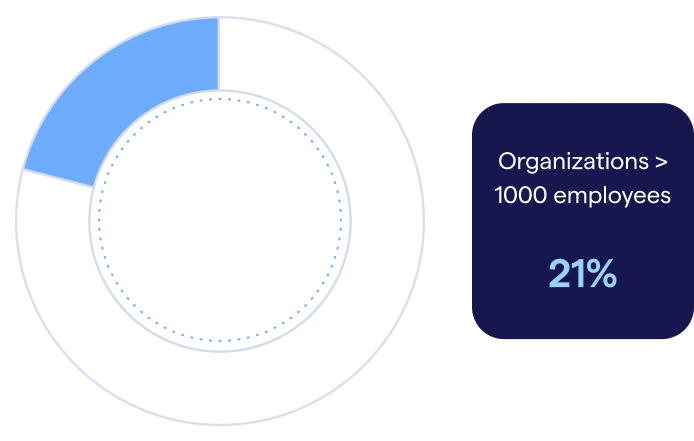
Figure 7: Proportion of employees who are security champions in organizations with lower-than-average engagement
Better engagement in security programs positively impacts the number of security champions and increases the number of employees who would be apt to support in the definition of security policies, which is expected to lead to improved business enablement and increased profits for organizations. So, how can security teams ensure their programs are as impactful as possible in driving engagement? And when employees still willingly and knowingly choose not to comply with policies, how can organizations better use human risk data in combination with technology to automatically reduce the risk?
How to mitigate human risk
The data in the previous section shows that mitigating human risk requires a combination of solutions. This includes adaptive training that is engaging and provides opportunities for employees to give feedback to the security team, thereby enabling security champions and collaboration on the development of policies. It also involves adaptive security practices, where security policies are automatically adjusted to become more stringent for those demonstrating the riskiest behaviors, such as privileged users intending to bypass controls. Through this approach, security leaders can be more adaptive, accurate, and proactive in managing and reducing cyber human risk, while also enabling the business to meet its goals.
1Effectively Train & ENGAGE Your People
2Build Phishing Resilience
3Automate conditional access & security controls
4Build effective & sustainable security
Figure 8: Components of adaptive training and adaptive security which combine to dramatically reduce human risk.
Adaptive Trainingmakes employees as cyber resilient as possible by putting employee engagement at the heart of the approach, utilizing targeted training, collecting insights, AI-powered phishing simulations, behavioral nudges and a gamified approach to demystify cybersecurity and significantly enhance users’ understanding of how their actions could impact the cybersecurity of the organization.
Adaptive Security automates conditional access and security controls, allowing technology to take over and prevent human-initiated security incidents in high-risk situations, such as where employees try to knowingly bypass policies. It also surfaces human risk data to line managers, as well as HR, ticketing, GRC, SOC, or access certification/recertification systems, which enables various teams across the organization to make better decisions regarding access grants, application download approvals, security risk assessments, policy exceptions, and incident triaging.
Adaptive Training:
Recommendations for increasing engagement and collaboration between security and business
Engagement with employees should be at the heart of any security awareness training program. However, the most commonly reported statistic for these programs is completion rate, often driven by regulations or the need to prove training completion for purposes such as procuring cyber insurance.
Focusing primarily on this metric turns security awareness training into a compliance check-box exercise, with little consideration for whether the cybersecurity policies and concepts are truly being absorbed, understood, or intended to be complied with by the learners.
To truly understand the impact of your training program on decreasing broader cyber human risk levels across your business, an important additional metric for security teams is to track is the learners’ levels of engagement with the content. This includes taking the opportunity to communicate with employees to learn how your security program and policies either enable the business or affect employees’ ability to be productive in their roles.
Engagement is essential in training as it helps learners focus, retain information, become more interested, and truly understand the concepts they are learning about. This leads to security being at the forefront of employees’ minds, making them more likely to apply what they’ve learned in their roles and daily lives. Additionally, engaged learners are more likely to value their cybersecurity courses, building a positive and collaborative relationship between security teams and the wider business.
Furthermore, by properly engaging with employees, security teams can start fostering conversations about security. An insight loop from the wider business can reveal where policies might be causing friction in meeting business goals, leading to the risk that they won’t be followed. Building trust and understanding means employees are more likely to ask questions or flag problems, rather than ignoring or bypassing security policies or controls. This leads to a reduction in security risk within the business and enables employees to contribute to the creation of cyber policies that drive improved profitability.
The following are recommended approaches to drive engagement in your security program.
1. Treat your security program like a conversation
Actively listening to others is crucial for effective communication. Understanding and responding to another person's perspective is more valuable than simply waiting for your turn to speak. The same can be said when launching a security awareness program – it is as important, if not more so, to listen to insights shared by your employees regarding their thoughts on observed behaviors, security policies, and training as it is to educate them through the content. If employees believe and communicate that security policies are not easy to follow due to negative impact on business productivity, it is important for security teams to understand and follow up on those concerns. Engagement increases when learners feel they are participating in a two-way conversation on security, and see their feedback acknowledged.
Organizations with the lowest (bottom quartile) proportions of employees reporting friction caused by security in their ability to meet business goals receive insights and feedback on security policies provided by every 118th employee, on average. In contrast, this figure rises to every 157th employee for the organizations reporting the most friction. The more engaged the employees, and the more input they provide into security policy definition, the more profitable the organization becomes.
One comment per 118 employees, <= 38% employees report friction

One comment per 157 employees, >38% employees report friction

Figure 9:Number of employees per one comment on security policy
2. Timing is everything
Engagement with training is much higher for courses which are bite-size in length, comprising a small number of “micro-modules” (less than 5 minutes’ duration) as opposed to hour-long campaigns. Training for 15-20 minutes every quarter as opposed to one hour a year also keeps security at the forefront of learners’ minds. Engaging learners in training when they’re in a mindset to learn, such as directly after the point of compromise in a phishing simulation, has also shown to be effective.
OutThink customers who break training into smaller campaigns distributed throughout the year achieve on average 6% higher engagement amongst their employees than organizations who launch bigger campaigns only once per year.
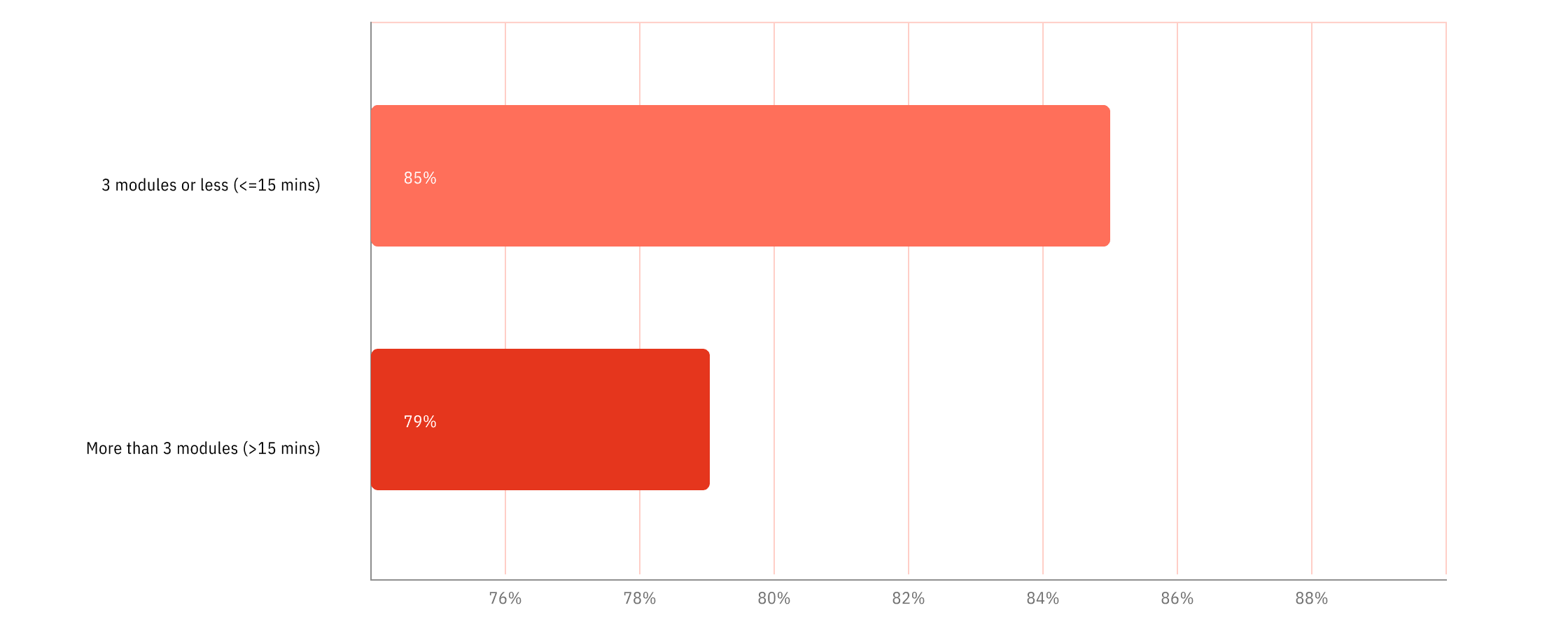
Figure 10: Employee engagement compared with training duration
3. Tailoring SAT content to role
Learners have a higher propensity to engage with and learn from content which relates directly to their role. When learners see how the risks being discussed could play out in their day-to-day activities, they can better understand the potential impacts of not following policy and take more interest in the steps they can take to reduce those risks.
Employees who are assigned role-based training are 7% more engaged than those who are provided with generic training.
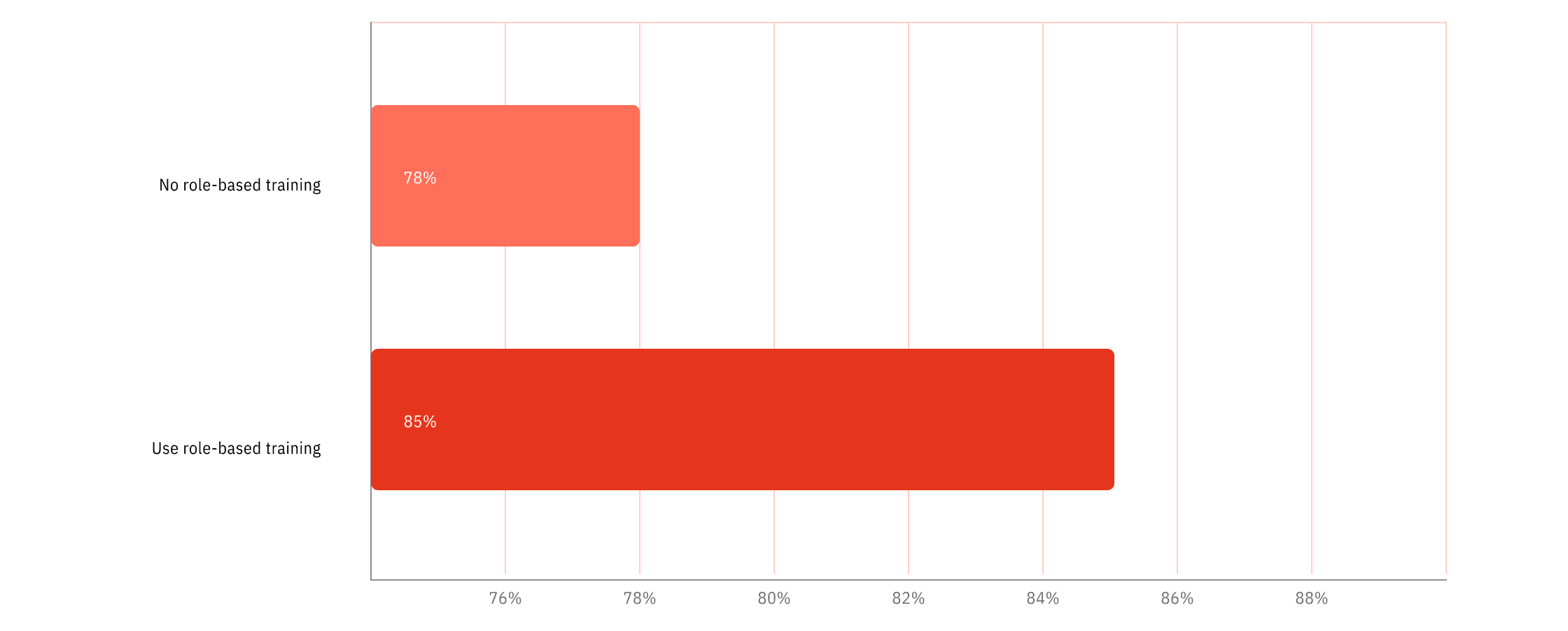
Figure 11: Employee engagement when using role-based training compared with not
4. Reflect on learner behavior and motivations
What are learners’ behaviors and motivations when undertaking training, and how should you account for this when recognizing that a one-size-fits-all approach is unlikely to lead to maximum engagement? Professor Angela Sasse (FREng), founder of the Research Institute in Science of Cybersecurity at University College London, uses the “Johari window” paradigm developed in behavioral psychology to divide an organization’s learner population into 16 psychographic segments . Employees who sit in each segment should be engaged in different ways: champions’ enthusiasm can be used to promote good cyber culture across your organization; uncertain learners are strongly motivated by security, but need more support in understanding why certain policies are in place – perhaps more training could help here; passive learners feel security is necessary, but not something they feel they themselves should put time into – how can you use role-focused or gamified training to help them pursue better habits?
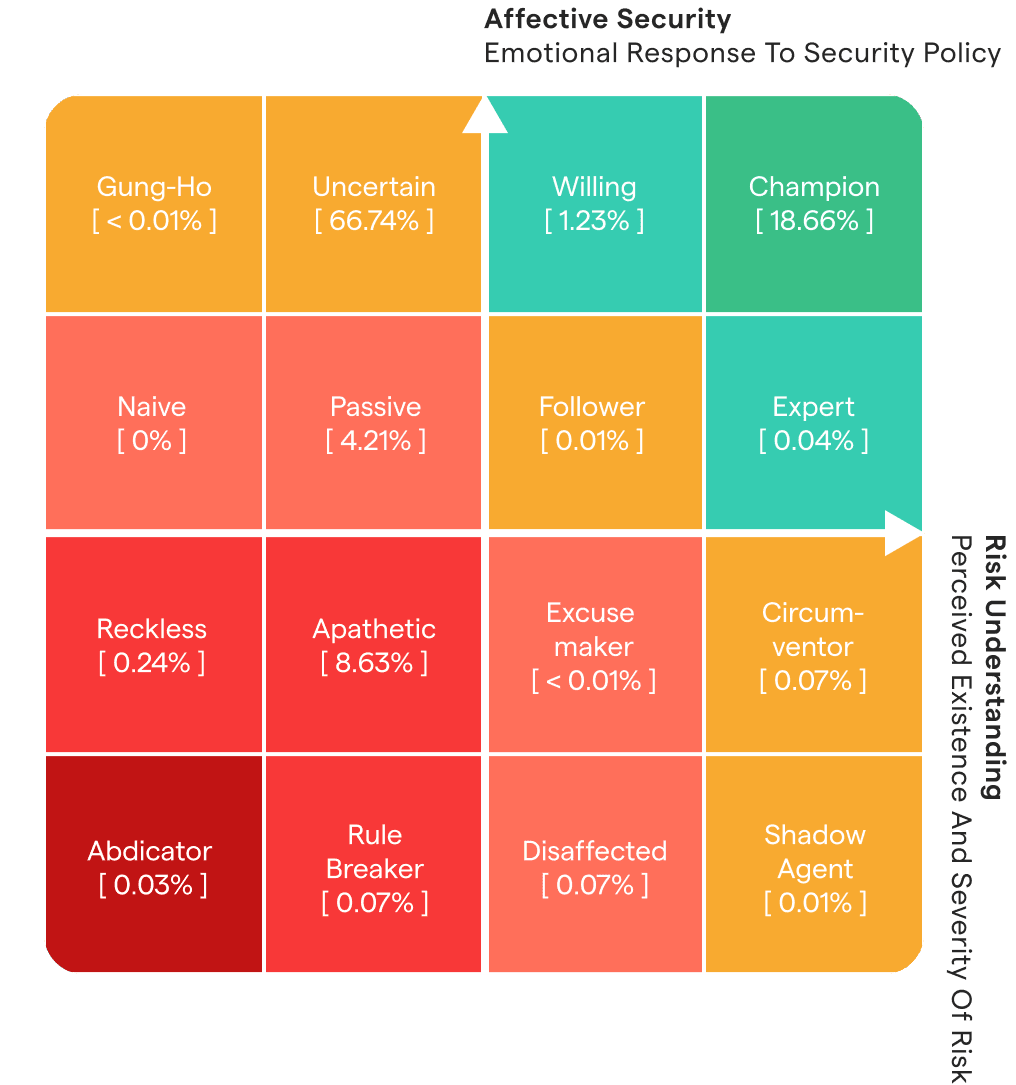
Across all OutThink customers, just over 18% of employees are champions. Some organizations leverage these champions to promote best practice cyber behaviors across their businesses. These champions often take on the role of “security liaisons” , receiving training in advanced policies and cyber concepts. Their peers in teams and business units are encouraged to approach them for advice and guidance on security matters. These employees are also well-suited to provide feedback on the impact of policies on business productivity, as they are likely to take a balanced view of risk versus reward. On the other hand, nearly 9% of employees are apathetic about security. For these individuals, additional training is unlikely to enhance engagement. Instead, some customers use line manager conversations to emphasize the importance of following policies.
5. Engaged managers equals engaged teams
When managers actively engage with cybersecurity, their teams are more likely to follow suit. This leadership sets a tone of importance and urgency, fostering a culture where security is prioritized. Managers can lead by example by swiftly completing their training, discussing cybersecurity in meetings, implementing best practices, and by encouraging their teams to behave securely, including nudging in cases where they don’t. Providing clear, accessible resources and support, as well as an understanding how their teams are engaging with security initiatives and policies, can make it easier for managers to champion cybersecurity efforts.
There is a strong positive correlation between the average completion rates of security awareness training campaigns by line managers and the average completion rates by their teams.
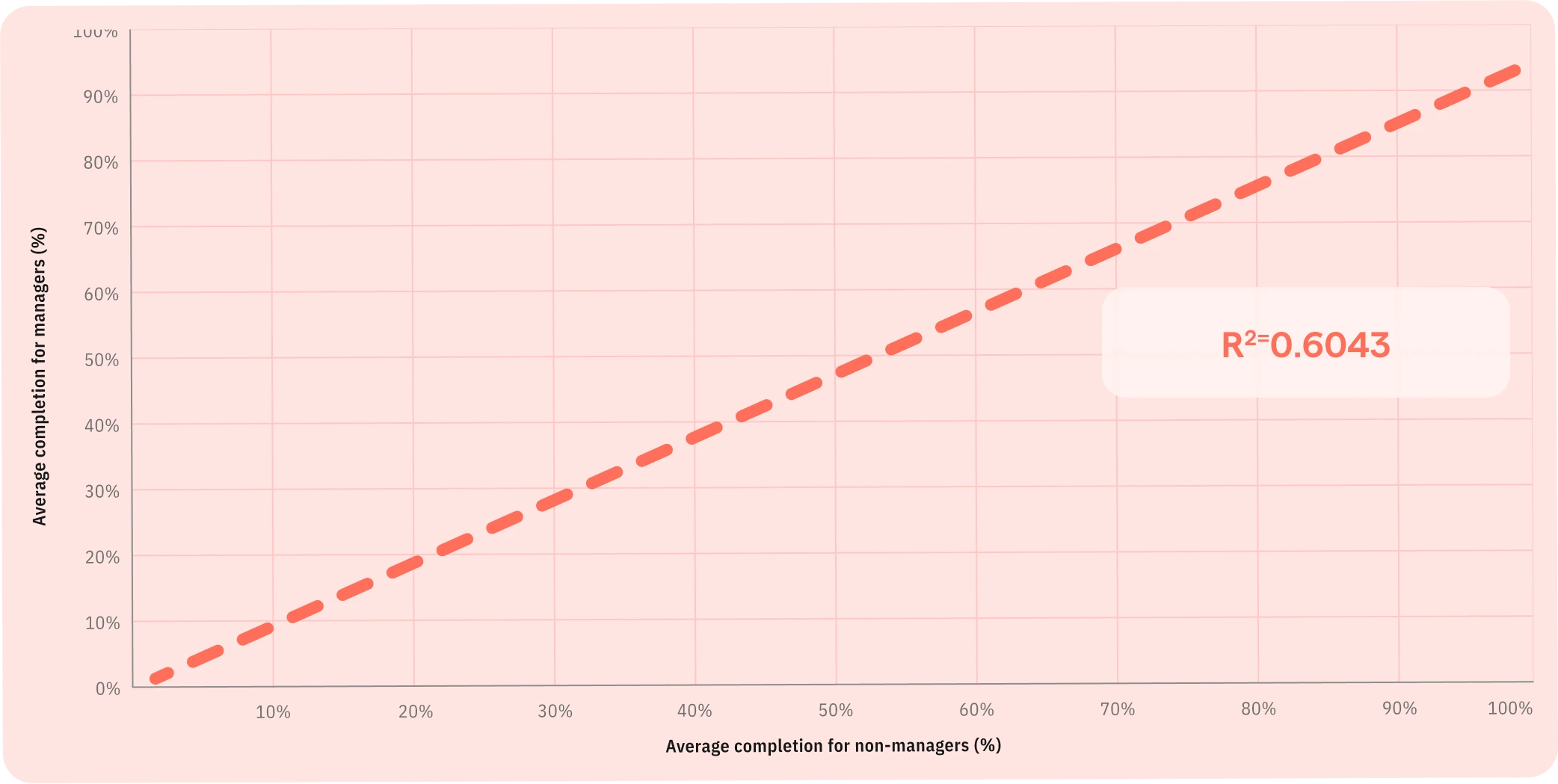
Figure 13: Relationship between line manager completion & overall company completion
Adaptive Security:
Recommendations for tightening controls for highest-risk behaviors
Even with maximum engagement, OutThink data supports Gartner research3 indicating that employees will knowingly take risks and bypass security controls to meet business objectives. Notably, 27% of employees with privileged access admit they don’t intend to follow all the security policies. Among those, 12% demonstrate low resiliency when faced with phishing simulations.
Statistics don’t improve much for the most engaged privileged users either, with 25% admitting they intend to bypass policy. The situation is even worse among the least engaged privileged users, with 32% planning to circumvent security controls.
Figure 5: On average, the proportion of employees highly engaged during their security awareness training campaigns
This data proves that training alone, whilst an important component, is not enough, and security teams should also consider increasing security controls for the riskiest or most susceptible users based on their demonstrated behaviors, environmental risks and sentiments towards security.
By automating conditional access and security controls, security teams can protect their workforce and data using existing technology to respond to human risk. This can be achieved by combining data from authentication, DLP, email security, endpoint and web gateway tools and defining logic based on “toxic combinations” of behaviors observed across these tools. These combinations automatically update rules driving security controls and policies for employees who demonstrate the highest risk. Such toxic combinations could be based on factors like their role, threats, level of access, attitudes and behaviors.
Effective and sustainable security can be built by feeding human risk data into business applications and security processes to include enhanced insights when making security decisions. As examples, human risk intelligence data could feed into the GRC platform so that security risk assessments cover all (people, process, technology) vulnerabilities or the ticketing / SOC system to give teams intel to make better decisions when granting access, approving applications for download, making policy exceptions or triaging incidents.
These practices represent a high level of human risk management maturity, enabling organizations to prevent human-initiated security incidents. While this level of integration is typically achieved as part of a later-stage maturity journey, it positions organizations to not only mitigate risks but also embed security as a strategic enabler across the business. This stage marks the final transition from reactive security awareness to proactive, adaptive security controls.
Conclusion: Where do we begin?
Adaptive training and adaptive security are both fundamental components for increasing employee engagement, putting humans at the center of security operations, and reducing risk. This approach transforms security into a business enabler and partner in driving profit growth. OutThink data supports independent research showing that organizations where employees collaborate with the security team and contribute to policy definition experience greater business enablement, with enterprise organizations being over 30% more profitable as a result.
Delivering such a human risk program requires a structured approach. Most organizations still operate at level 1 maturity, running reactive training with a compliance focus, tracking only knowledge and completion rates in training campaigns and click and reporting rates following phishing simulations. To mature to level 2, organizations should adopt an engagement-focused approach, adapting training for each user based on their role, behaviors and risks, and collecting insights from employees as part of campaigns to gather feedback on policies and observed security behaviors.
Once adaptive training is implemented, organizations can begin to analyze how to use the data insights they collect to implement adaptive security through the automation of conditional access and security controls. This sets the stage for full automation with predictive human risk management, delivering automated risk response workflows.
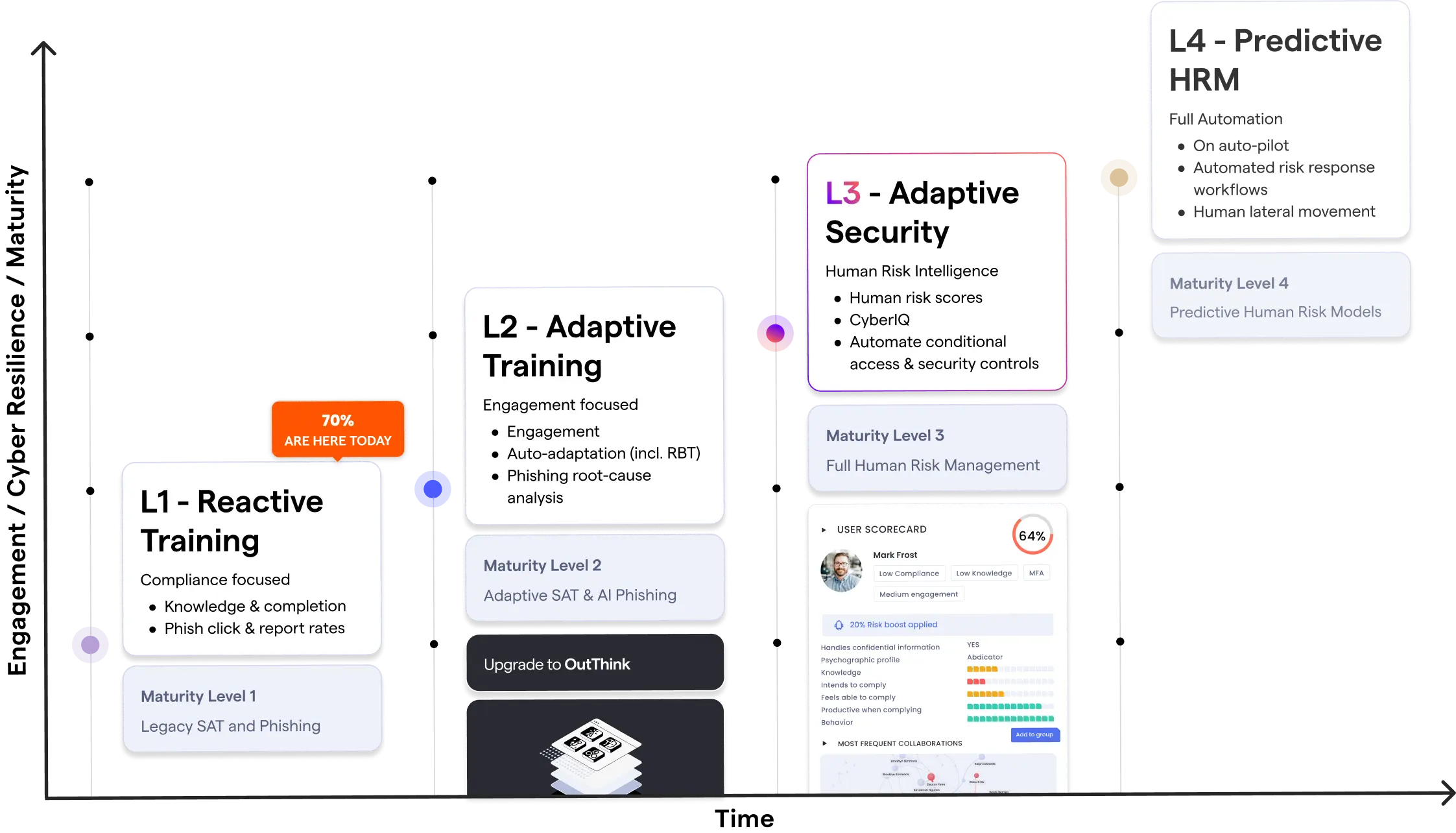
Figure 16: Human risk management maturity journey
Summary of OutThink
OutThink, founded in 2019 by five CISOs, is a revolutionary Cybersecurity Human Risk Management Platform that empowers security teams by targeting the source of up to 90% of all data breaches: human behavior. The platform combines the adaptive training and adaptive security to prevent human-initiated security incidents. It inspires employees to embrace security training through interactive and role-specific learning experiences, builds phishing resilience with adaptive, real-world simulations, and automatically tailors access and permissions based on individual cyber risk portraits. Additionally, OutThink elevates security to the C-suite agenda by integrating human risk intelligence into workflows, providing a 360-degree view of organizational cyber vulnerabilities and enabling data-backed decisions.