The Cybersecurity HRM Forum roundtable in New York City brought together participants from leading organizations such as Mass Mutual, Natixis, Apple Bank, Goldman Sachs, and Columbia University for an in-depth discussion on managing the complex risk of human-IT interaction. As we waded into a discussion about the way security engagement relates to secure behaviors, the conversation diverged into several threads, including security awareness, outcome metrics, and leadership involvement in security management.
Engagement signals through learner feedback
Early in the discussion the group came onto the topic of security friction. That users often chafe under the yoke of restrictive security policies. That security controls can get in the way of doing the job. So people just bypass these controls. One of the CISOs in the room shared an anecdote from a past role (to be clear, NOT one of the companies in the room) of a security colleague figuring out his own way to bypass the firewall in order to get to certain online services. Policy resistance is a natural human tendency, even if said human is on the very team meant to implement the policy. The key, it turns out, is to engage IT users in understanding the sources of security friction, and then to mutually find solutions that get the business process working in a secure way. The holy grail is to get that level of business engagement to such a state where the business come to Security proactively, asking for help to build security into new projects from their start.
Engagement metrics vs. outcome metrics for security
One of the CISOs in the room pointed out the importance of measuring the impact of awareness programs. One way to measure impact has traditionally been through phishing simulations. Otherwise the status quo of measuring completions, as the only thing we can measure continues to be the uncomfortable norm. Engagement is important for the security team to measure, but likely not a metric for company leadership to track. Outcome metrics came up as a viable alternative to training completion rates. Something that measures meaningful resilience capabilities and can be continually improved. Dwell time (the time between first click and first report of each phishing email) can be a good example of such a metric. There are several others that will be the subject of a future post.
Engaging the business leadership
The topic of engaging business leadership in managing security in a human-centric way always comes up in these roundtables. Today’s session did not disappoint. The consensus around the table was that HRM is a risk the business needs to own, and the CISO’s role is to advise the business leadership how to manage this risk. One of the CISOs took us in the direction of having role-based training for the business leaders in the organization. Upon reflection this is really a matter of the CISO having a serious conversation with the relevant business leaders to level set the role and responsibilities of the business owner in setting company culture and strategy for collective ownership of security risk. This needs to be an ongoing conversation between business and security leaders in order to truly engage at the executive level.
Fostering in-team engagement
Another take on engagement is to run an effective security champion, or ambassador, program. Our CHRM Research Report spells out the behavioral segmentation of OutThink’s entire learner base, showing that 24% of learners turn out to be Security Champions. Running a process that identifies each individual’s behavioral segment can help identify the best candidates for a security champion program. The members of the roundtable agreed that champions will often appear more approachable than the CISO’s organization for questions about security or even feedback to the security team. Best case for engagement in this vein is to foster discussions about secure processes and behaviors inside and among the teams in the business. Something champions can help facilitate
In-training engagement
Engagement in security awareness training is critical for the training to be successful. While it may seem like a good idea to force engagement, through gamification or interactive content, forced engagement can turn into a net negative. If a busy executive is forced to play a “security game” in order to consume irrelevant content this experience can only build resentment towards the security team. This has the opposite effect of all the forms of engagement described in this post. Engagement has to be real, because the content is hyper-targeted and relevant. It cannot be forced atop “one size fits all” content.
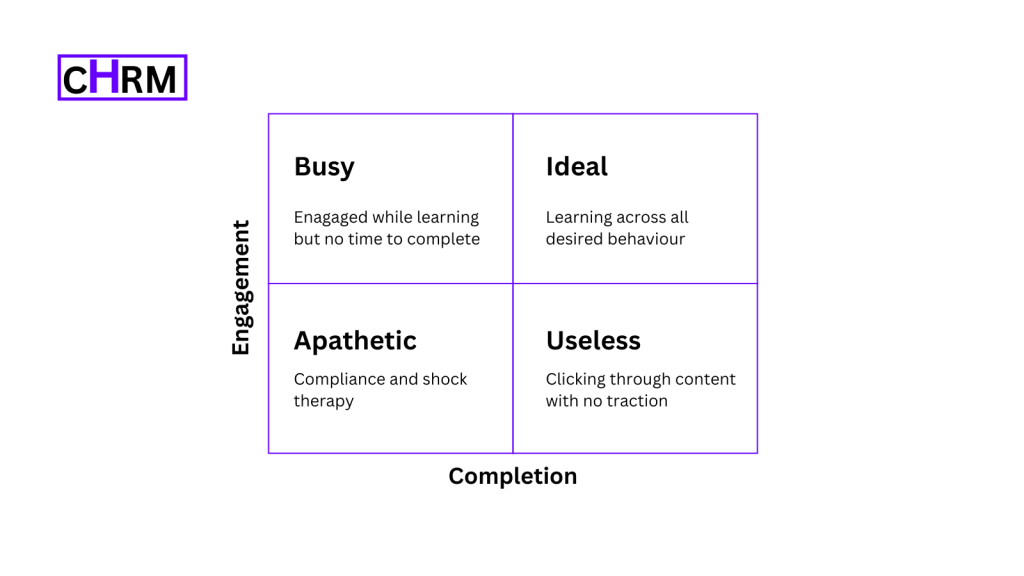
Of course, we want to avoid the bottom right quadrant of this Engagement-Completion matrix. But, we do want to track the learners that do fall into that bottom right category. Their lack of engagement tells us something that can become useful. For those who show themselves to be high-risk IT users through their actions, this insight can help the security team intervene in time to prevent an adverse event from happening.
Engagement after SAT
The level of actual engagement the security team generates with the employee base is most meaningful, of course outside and after the training interaction. Actual engagement can be seen in a variety of forms. The most common and obvious is the reporting of phishing attempts to the security team. Others have also been mentioned above, like asking for the security team to get involved in new initiatives for advice on making these new projects as secure as possible. Also providing feedback regarding control friction to the security team, either through champions or directly. Also, the level of interaction with post-training nudges can tell the security team whether users are engaging with that content. For example telling the system that nudges them after clicking on a phishing simulation the reason for their click.
Conclusion
Engagement is obviously critical for the security team to move up the Cyber HRM maturity journey. But engagement with training content is only one form of engagement, and perhaps the spark that starts the journey. There are many other ways the CISO should measure and seek engagement between employees and the business. We covered six of them here – the remaining 44 we leave to the reader’s imagination.